- CLOUD
- SOLUTIONS
DRaaS
Smart Solutions
Database Management
Managed Services
- Managed Colocation
- Cross Platform Migration
- Cloud Migration Services
- Backup and Recovery
- Email Migration services
- Business Continuity Plan
- Application Development
- Application Performance Monitoring
SAP
Banking Services
Cloud Applications
- Serverless computing - eNlight Cloud
- eNlight Big Data as a Service
- IoT (Internet of Things)
- eCOS (eNlight Cloud Object Storage)
- gDNS (Global Domain Name Services)
Content Delivery Network
- SECURITY
- INFRASTRUCTURE
- PRODUCTS
- ABOUT US
ESDS
Resources
Customers & Partners
GPTW
- Careers
Experience Superior Performance with Auto Scalable eNlight Managed Cloud
eNlight cloud gives you complete control and power to do more as you achieve superior performance on the World’s First Auto-Scalable cloud.
- Create on-demand Virtual Machines
- Reboot, Start and Shut down VMs, independently
- Deploy & assign resources dynamically
- Intelligent Auto Vertical and Horizontal Scaling
- Know Resource Usage before-hand, through eNlight's wise & Timely Predictions
- Pay Per Consume, eliminate the cost of unused resources
Register for eNlight cloud services by paying a one-time fee of Rs. 100 + GST which will be adjusted against your final cloud package amount once we begin your billing cycle.

Modern IT Infrastructure, Built for...
This infographic illustrates how enterprises can architect a resilient, scalable, and performance-driven IT environment by aligning core infrastructure with advanced compute needs. It highlights the strategic integration of dat...
Read More..
2026 Tech Shifts Shaping India’s ...
As 2026 approaches, India’s IT & ITeS SMEs are rethinking how they operate, secure, and scale. From GenAI-driven workflows and hybrid cloud adoption to automation-first operations and API-led platforms, these tech shifts defi...
Read More..
GPU-as-a-Service in India: Powering...
India’s GenAI adoption is driving demand for flexible GPU infrastructure. GPUaaS enables enterprises to run AI, ML, and HPC workloads with lower CapEx, faster deployment, and scalable, pay-as-you-use performance.
...
Read More..
Journey of a Banking Transaction in...
A seamless banking transaction depends on highly resilient data center infra that ensures secure processing, real-time validation, intelligent routing, an interrupted availability for enabling reliable digital payments even und...
Read More..
GPU-as-a-Service vs Traditional Inf...
This infographic highlights how GPU-as-a-Service transforms compute performance compared to traditional infrastructure. It showcases differences in deployment, scalability, cost, maintenance, and AI readiness, helping enterpris...
Read More..
Building India’s Own Secure Cloud...
This infographic explains Why India’s need for a sovereign cloud and how eNlight Cloud meets national data security, localization, and compliance goals. It shows key advantages, sector-specific cloud models, and how eNlight d...
Read More...jpg)
Data Localization Laws India 2025: ...
This infographic highlights India’s evolving data localization mandates, key compliance actions, sector-specific rules, and how enterprises can strengthen security, meet regulatory expectations, and host critical information ...
Read More..
Choosing the Right Cloud: Public, P...
This infographic simplifies the differences between Public, Private, and On-Prem cloud models, helping you navigate security, control, and compliance needs. It highlights how each environment supports scalability, governance, a...
Read More..
PaaS Essentials: Powering Faster, S...
PaaS removes infrastructure complexity and empowers teams to build, test, and deploy applications faster. It enhances automation, scalability, and collaboration across hybrid and multi-cloud environments.
This infogra...
Read More..
GPU-as-a-Service is shaping the fut...
GPU-as-a-Service is shaping the future of AI workloads, showcasing its rapid growth, scalability, and cost efficiency. The visual highlights industry applications, key advantages, challenges, and ESDS’s expertise in deliverin...
Read More..
How Is Cloud Adoption Reshaping Co-...
Discover how co-operative banks are moving beyond traditional systems with cloud adoption. This infographic unpacks the drivers, everyday impact, challenges, and the shift toward hybrid and community cloud models—ending with ...
Read More..
Foreign Cloud vs. Sovereign Cloud ...
Foreign Cloud vs. Sovereign Cloud highlights challenges like overseas data hosting, compliance risks, and costs, versus Sovereign Cloud benefits—data residency, compliance, independence, affordability, and national security, ...
Read More..
End-to-End IT Management flow...
It presents a streamlined approach to managing IT operations through a connected lifecycle, showcasing how businesses can enhance security, optimize performance, and achieve compliance. The design reflects modern digital infras...
Read More..
SOAR Automation Flow: Enhancing Cyb...
This visual guide outlines the key benefits and steps of implementing SOAR services to streamline security operations. It highlights how automation boosts incident response, improves scalability, and ensures standardized workfl...
Read More..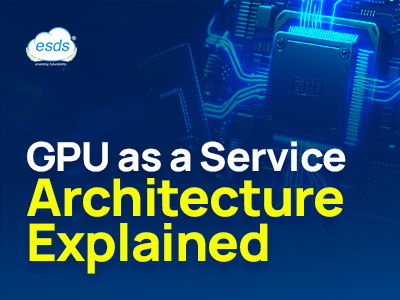
GPU as a service architecture expla...
This infographic explains the architecture of GPU as a Service, showing how users access GPU power through secure layers of management, virtualization, and infrastructure. It highlights the flow from user request to GPU executi...
Read More..
Managed IT Services Lifecycle for S...
Discover the lifecycle of Managed IT Services for SaaS companies, from assessment and cloud deployment to 24/7 monitoring, security, and continuous scaling. This infographic highlights how Managed IT boosts uptime, performance,...
Read More..
SOC on Autopilot? Here Are 4 Game-C...
Boost your cybersecurity with ESDS SOC automation — 80% faster incident response, 95% fewer human-error breaches, and 1,000+ hours saved annually. Experience the power of our AI-driven 4-step SOC workflow.

Transform, Secure, and Scale: Manag...
Transform your IT infrastructure with ESDS Managed IT Services. We offer comprehensive lifecycle support, including evaluation, installation, 24/7 monitoring, and proactive enhancements. Ensure enterprise-grade security, scalabili...
Read More..
Government Community Cloud, Where S...
From digital health to smart governance, India needs a cloud that’s local, secure, and built for the public good.
Here's why Government Community Cloud by ESDS is different — and why it matters.
...
Read More..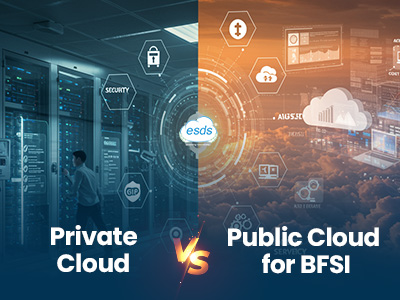
Private Cloud vs Public Cloud for B...
In the BFSI sector, the cloud decision isn't just about technology—it's about compliance, control, and cost-efficiency. This highlights key differences between private and public cloud models for financial institution...
Read More..
Secure. Sovereign. Scalable. Govern...
Secure your critical government data and applications with ESDS Software Solution Limited tailored Disaster Recovery as a Service. Trusted by over 34% of public sector entities, our compliant and geo-redundant solutions ensure ...
Read More..
Understanding Privileged Access Man...
Privileged accounts hold elevated access to critical systems, making them a frequent vector for security breaches. As organizations scale their digital infrastructure, implementing structured access controls becomes essential. ...
Read More..
Why SOC as a service matters...
Discover how SOC-as-a-Service help businesses to tackle rising cyber threats with 24/7 monitoring, AI-driven threat detection, and scalable cloud-ready protection. Explore key metrics, components, and benefits, all in one place...
Read More..
Scalable, Compliant Cloud Infrastru...
ESDS’s comprehensive cloud service portfolio, showcasing Tier 3 certified Data Centres across key Indian cities. It provides core offerings in Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Managed Serv...
Read More..
Managed Services: IT, Cloud, Securi...
Managed Services: IT, Cloud, Security & Continuity - Our managed services portfolio offers a diverse range of services to our customers to complement day-to-day data management of IT services and cloud migration.

IT disasters real-world cases conse...
Explore real-world IT failures, their consequences, and proven strategies to prevent disasters. Learn how backup, cybersecurity, and disaster recovery can safeguard your business. Stay protected against IT disruptions.
<... Read More..
All you need to know about IT failu...
IT failures can lead to massive financial losses, security breaches, and operational downtime. Discover the key causes, real-world consequences, and proven solutions like backup strategies, disaster recovery plans, and cybersec...
Read More..
The Future of Cloud Hosting, Trends...
Cloud adoption is soaring! With 90% of enterprises embracing multi-cloud and global cloud security spending hitting $98 billion by 2025, businesses are prioritizing agility, security, and cost ...
Read More..
ESDS Government Community Cloud: Po...
ESDS offers secure disaster recovery and cloud solutions for government, emphasizing their certified, scalable, and highly available Government Community Cloud, which supports critical e-governance infrastructure.

How to Select the Right Colocation ...
Selecting a colocation provider is a critical decision. Prioritize location in stable regions with robust power. Evaluate facilities for efficient cooling and backup systems. Confirm strong security measures, compliance certifi...
Read More..
How banking community cloud with da...
Explore how cloud adoption with data sovereignty safeguards banking data, ensuring compliance, security, and future-proof financial technology strategies. Transforming banking data security by BFSI community cloud navigates com...
Read More..
Stay Resilient, Recover Faster: ESD...
Disaster recovery is vital for protecting critical data and ensuring business continuity. ESDS Disaster Recovery as a Service (DRaaS) delivers tailored, secure, and cost-effective solutions to safeguard your operations during d...
Read More..
Revolutionizing the Cloud in India:...
43% of enterprises overspend on cloud due to inefficient resource allocation. eNlight Cloud, a pioneer since 2010, optimizes cloud usage, saving businesses up to 50% on costs. With the global cloud market projected to reach $1....
Read More..
The PAM Checklist: Must-Have Featur...
Discover the essential features every business needs in a Privileged Access Management (PAM) solution to safeguard against cyber threats. From role-based access control to real-time monitoring, ensure your organization stays se...
Read More..
Choose the Right Managed Security S...
It is very important today to select the perfect Managed Security Services Provider (MSSP) to protect your business assets against cyber threats. This guide outlines key evaluation criteria, warning signs to watch for, and best...
Read More..
Optimize Your Business Operations w...
Explore the advantages of cloud hosting, which include 99.99% uptime, faster loading times, cost efficiency, advanced security, and scalability. Cloud hosting provides reliability and security, making it ideal for modern busine...
Read More..
Colocation Data Centers: Powering t...
Witness the evolution of data centers – from humble beginnings as simple server rooms to the sophisticated powerhouses driving our digital world today. Explore how these critical hubs have adapted to the cloud era and are now...
Read More..
Government Community cloud – The ...
India’s digital transformation is booming—but can it thrive without a secure, scalable, and compliant cloud solution? ESDS Government Community Cloud is here to power the next wave of innovation with 100% data sovereignty, ...
Read More..
Air vs. Liquid Cooling for Data Cen...
Liquid cooling is rapidly becoming the preferred method for cooling high-performance servers due to its superior efficiency and ability to handle soaring AI workloads. Unlike traditional air cooling, which relies on air to diss...
Read More..
Why Community Cloud is the Future o...
Discover how Community Cloud is transforming the banking sector in India! This infographic reveals how banks can unlock cost savings, enhanced security, and seamless scalability. Learn why more banks...
Read More..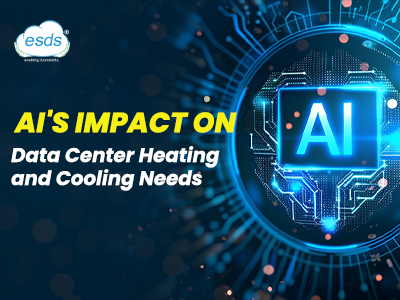
AI Drives Demand for Advanced Cooli...
Artificial Intelligence transforms the data centers with an increase in energy demand and heat generation, making cooling critical and difficult. This is due to the high energy consumed by powerful GPUs and NPUs that power AI w...
Read More..
BFSI Cloud - The Future of Financia...
BFSI Cloud transforms the financial sector with unmatched security, scalability, and performance. In addition to offering best-in-class protection through end-to-end encryption, real-time monitoring, and high-grade threat detec...
Read More..
Transforming Cybersecurity with SOA...
Ready to transform your cybersecurity operations? Discover how Security Orchestration, Automation, and Response (SOAR) can revolutionize your threat management! Our comprehensive infographic includes the core components, benefi...
Read More..
Stay Ahead with Cyberthreats...
Do you have a limited IT budget and not enough cybersecurity experts? SOC-as-a-Service enables the creation and retention of an in-house 24/7 SOC team. It's an excellent technique to resist data breaches. But there's a ...
Read More..
Backing up the Data...
Your business runs on data - whether it’s customer information, financial records, or daily operations. A data loss can cause major setbacks, from halting operations to financial losses and damaging your reputation. Protect y...
Read More..
Uncover, Protect, Secure - Your Ult...
VAPT is one of the security services meant to detect and eradicate possible vulnerabilities within an IT infrastructure. It's characterized by two crucial processes: Vulnerability Assessment - and Penetration Testing. New r...
Read More..
Managed Security Services - The Key...
Are you tired of worrying about cyber threats and data breaches? Discover how managed security services can revolutionize your bank's security posture. This infographic will guide you through the key benefits of partnering ...
Read More..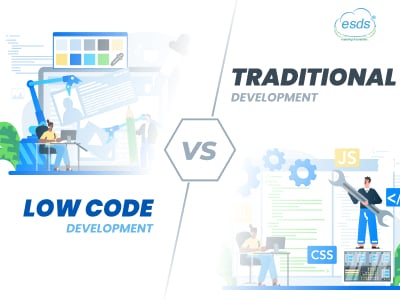
Low Code Development VS Traditional...
Low-code development dramatically speeds up the application process, allowing developers to build and deploy apps up to 10 times faster than traditional methods. A 2021 survey found that 29% of users saw a 40–60% increase in ...
Read More..
Security Loopholes in Your IT Infra...
Streamline your security with ESDS's VAPT tool. Manage Vulnerability Assessment and Penetration Testing entirely online, achieve CERT-in certification with just a few clicks, and ensure comprehensive network protection with...
Read More..
Top 5 Cloud Migration Mistakes Ever...
Rushing into cloud migration without a comprehensive plan can lead to unexpected costs, data loss, and downtime. To avoid disruptions during the transition, ensure a thorough strategy that addresses security, compliance, and sc...
Read More..
Learn About 15 Cyber Attacks & How ...
Stay ahead of 15 Types of Cyber Attacks. Discover the crucial threats targeting your applications and IT infrastructure, from phishing to ransomware. Equip yourself with the essential knowledge to enhance your organization'...
Read More..
Anatomy of Data Center...
A data center is a physical room, building or facility that houses IT infrastructure for building, running, and delivering applications and services, and for storing and managing the data associated with those applications an...
Read More..
From Vulnerable To Victorious - VTM...
Based on the data, 1,075 ransomware victims were posted on leak sites in the first quarter of 2024, despite disruptions to major ransomware groups LockBit and ALPHV/BlackCat.
To prevent hackers from accessing your sys...
Read More..
Don't Get Hacked - Automate Your De...
Security teams are affected by manual tasks, slowing down their response times and leaving them vulnerable to security incidents. This is due to complex networks and ever-evolving threats.
The report shows that an org...
Read More..
Safeguard Your Data with ESDS Backu...
60% of businesses experience data loss events every five years, and 43% of cyberattacks specifically target small and medium-sized enterprises. Our reliable solution offers seamless data protection and recovery, ensuring you...
Read More..
Stop Ransomware Now...
In the past year, 59% of organizations experienced ransomware attacks, 70% of which resulted in data encryption. Ransom demands have increased fivefold over the last 12 months. 32% of attacks originated from unpatched vulnerabi...
Read More..
Backup - the ultimate safety net...
Backup offers the ultimate safety net against unexpected loss or damage. ESDS Backup as a Service (BaaS) automatically backs up critical business information to secure, offsite servers. Work easy knowing your data is safe, r...
Read More..
Cloud Migration : Taking Your Busin...
Join the 85% of businesses leveraging cloud computing to reduce IT costs by 20-30% and discover the multitude of benefits for businesses of all sizes. By carefully planning and executing your migration strategy, you can unlock ...
Read More..
Empower Your Business With Seamless...
Empower Your Business With Seamless Disaster Recovery and Data Migration Solutions : Disaster recovery data migration between platforms is crucial during a crisis. However, such projects usually exceed budgets by 25 – 100%...
Read More..
Why Do Business Need Privileged Acc...
Every organization relies on privileged access management tools for defending critical systems. They protect against internal and external threats which are often arise from incorrect use of admin rights. With ESDS PAM, busines...
Read More..
Protect Your Business From Ransomwa...
Ready to equip yourself with 10 essential strategies to shield your business from the growing threat of ransomware attacks? Learn how to safeguard your data, thwart online threats, and empower your employees to be cybersecurity...
Read More..
Safeguarding Your Digital Fort With...
In an era where cyber threats loom large and skilled defenders are in short supply, ESDS Managed Security Services stands as your digital shield. With our 24/7 vigilance and expert insights, rest assured that your business is f...
Read More..
Ever wondered how businesses stay a...
Within the unpredictability of disasters, businesses need robust solutions to weather the storm. Enter DRaaS by ESDS - your lifeline in times of crisis. With rapid data and system recovery, fortification against cyber threats, ...
Read More..
Tips & Traps - Engaging with Manage...
Is your business ready to level up its IT infrastructure? Don't settle for less when it comes to Managed Service Providers! Dive deep into the crucial tips and potential pitfalls to ensure you're partnering with the per...
Read More..
10 Benefits of Blockchain For Your ...
43% of global organizations are already investing in blockchain technology, and another 30% are actively planning to do so within the next two years. This underscores the growing acknowledgment of blockchain's capacity to r...
Read More..
Are You Prepared For a Cyber Emerge...
Don't wait for a cyber crisis! Data security is a must, with risks like security breaches, natural disasters, theft, and human error. ESDS offers cutting-edge solutions with 99.99999999999% reliability. Protect your data to...
Read More..
Enhancing Data Center Security:Fort...
Crack the Code to Data Center Security!" Explore our infographic: "Digital Fort Knox - Guarding Your Data Fortress!" Delve into physical and network security, data encryption, access control, audits, disaster recovery, and clou...
Read More..
Why Low-Code is a must: 5 Eye-Openi...
The benefits of Low Code cannot be overstated. The low code platform allows organizations to implement automation faster without adding expensive, highly experienced developers. Here are some ...
Read More..
10 Key Questions CEOs Should Ask Ab...
10 key insights especially tailored for CEOs - Navigate your leadership journey confidently as you explore the pivotal queries that define top-tier leadership ...
Read More..
Top 5 Reasons That Make Healthcare ...
In an increasingly interconnected world, the healthcare industry has emerged as a prime target for cybera...
Read More..
7 Benefits of URL Monitoring to Boo...
URL monitoring, an essential practice in today's digital landscape, involves the continuous tracking ...
Read More..
Is your IT management Team Thinking...
Managing IT infrastructure can be intricate, but not with ESDS eNlight 3600. Effortlessly monitor ...
Read More..
Thrive or Strive: The Role of Cyber...
Small Business, Big Security: Safeguard Your Future with Cybersecurity Implementation. Don't underestimate the risks! Discover the importance of securing your business against cyber threats. Stay protected and build trust w...
Read More..
Mastering Enterprise Data Protectio...
This informative infographic presents the essential strategies for safeguarding enterprise data with efficient backup and recovery practices. Explore the top 5 industry-proven methods to ensure data integrity, reduce downtime, ...
Read More..
The Growing Vulnerabilities: 8 Fact...
The expanding cyber-attack surface refers to the increasing range of vulnerabilities and potential entry points that can be targeted by cyber attackers. It represents the broader attack surface that emerges as organizations ado...
Read More..
10 Types of Cyberattacks Your Websi...
Discover the 10 most common cyberattacks that pose a threat to your website's security. From DDoS attacks and SQL injections to XSS attacks and phishing scams, this comprehensive guide unveils the vulnerabilities your websi...
Read More..
Managing your IT Environment, the P...
We take care of your entire IT environment, handling all the technical aspects so you can focus on what you do best. Our team of professionals ensures your systems are optimized, secure, and up-to-date. From proactive monitorin...
Read More..
6 Crucial Components for an Uninter...
Refer to the six key components mentioned in this infographic and are essential to ensure a smooth Intern...
Read More..
Defending Against Top 10 Database S...
Discover the most pressing database security threats and learn how to defend against them. From SQL injections and insider attacks to ransomware and data breaches delve int...
Read More..
10 Ways to Improve the Cybersecurit...
In today's digital landscape, safeguarding your business from cyber threats is paramount. Implementing robust cybersec...
Read More..
SIEM and SOC: What's the Difference...
SIEM and SOC are both modern options to handle your business's cyber security. But what should you opt for, SIEM or SOC? What's the difference between SIEM and SO...
Read More..
Cyber Attacks, Data Breaches & Rans...
Are you taking learnings from the recent cyber-attacks, data breaches, and ransomware incidents?
At ESDS, we understand the importance of staying one step ahead in the ever-changing world of cybersecurity. Discover ho...
Read More..
Safeguarding Your Data in a Remote ...
Endpoint backup is essential for organizations to safeguard their data, especially when they have a geographically distributed and remote working team. Here we list down the benefits of endpoint backup.

What are the benefits of endpoint b...
Protect your business-critical data and ensure continuity with endpoint backup solutions. Don't let data loss or downtime put your business at risk. Simplify your data recovery and safeguard your success with endpoint backu...
Read More..
Why your business needs a Cyber Sec...
Are you taking the necessary steps to protect your business from cyber threats? Conducting regular cyber security risk assessments can help identify vulnerabilities and pro...
Read More..
5 Innovative Ways AI is Changing Cl...
As the world becomes increasingly reliant on cloud computing, the role of artificial intelligence (AI) is becoming more important. AI is transforming the way we manage and ...
Read More..
Best Practices for Maintaining Digi...
In the age of remote work, it's crucial to maintain good digital hygiene to protect sensitive data and avoid cyber threats. Stay secure by using strong passwords, avo...
Read More..
5 Reasons to Choose an MSSP...
Want to save costs, boost productivity and supercharge your business? It's time to consider Managed Service Providers! Learn about the top 5 reasons to choose an MSP in our informative new infographic

5 Benefits of managed Security Serv...
Benefits that Managed Security Services offer to the Banking Industry, include proactive threat management, increased compliance, reduced risk of data breaches, improved operational efficiency, and access to expertise and techn...
Read More..
which individuals or teams are typi...
An IT disaster has the potential to disrupt the entire business, dragging in every department, So, Its imperative to involve every department in the process of Disaster Recovery for a wholesome finish.

Brand Protection Service - Protecti...
Are you leaving your brand vulnerable to ever-evolving threats? ESDS’ robust technology scans the internet, analyzes potential threats, and detects phishing threats, onli...
Read More..
How do AI & ML help gain cybersecur...
Machine learning (ML) and artificial intelligence (AI) are increasingly being used in the field of cyber security to help identify and mitigate security threats. Here are s...
Read More..
Managed Security Services - The Fut...
Discover the top 10 reasons why your business should choose managed security services. From enhanced protection against cyber threats to reduced IT costs and improv...
Read More..
PHISHING - Don't Take The Bait in T...
Don't get hooked! Phishing attacks continue to be a top security threat. Stay vigilant by avoiding suspicious emails, messages, and links. Remember, if it looks too good to be true, it probably is.

How Disaster Recovery is Different ...
In the arena of data protection Disaster recovery and regular backup are related yet different in nature. Despite the same similarities, both concepts have different goals and approaches. Learn how disaster recovery and regular...
Read More..
How To Plan A Cloud Disaster Recove...
Don't get caught in a cloud of chaos! Protect your business and secure your data with a winning Cloud Disaster Recovery strategy by ESDS. Ensure seamless continuity even in the face of unexpected disasters.

How Safe Is Your Business on the Cl...
The easier it has become to store, retrieve and analyze data online or on the cloud, the easier it has become for hackers to hack data through multiple ways unknown to us. ...
Read More..
Why Uptight Cyber Security Gives Yo...
With the increasing dependence on technology and the internet, cyber risks have become a major concern for individuals, businesses, and governments. To mitigate these risks, organizations should implement a comprehensive cybers...
Read More..
DISASTER RECOVERY MENDING YOUR GAPS...
A shocking 45% of businesses experienced outages or downtime this year. For how long your business can survive with your IT systems at a halt? It’s time to be proactive and tackle disasters at will. Plan your DR on ESDS Cloud...
Read More..
5 Major Security Risks For Online B...
With the increasing dependence on technology and the internet, cyber risks have become a major concern fo...
Read More..
Your Ultimate guide to a data backu...
Discover the essential steps to creating a secure and effective data backup plan. From understanding the ...
Read More..
The Future of Data Management...
Unlock the full potential of your data with cloud-based data fabrics. Connect and share data seamlessly across systems and applications, scale on demand, and access your ...
Read More..
Unlock the Benefits of DCIM Tools -...
To manage their data center environment, enterprises increasingly rely on ...
Read More..
Can scaling your business be possib...
ESDS’ Managed Security Services enable you to swiftly fortify your environment and grow more robust over time, regardless of your challenges with overcoming skill shortages, countering new threats, or seeking greater efficien...
Read More..
How costly and time consuming can a...
Data breaches can be both costly and time-consuming. The cost can also include loss of business or damage to a company's reputation. The time it takes to investigate an...
Read More..
5 Most Potential Cybersecurity Issu...
Remote workers may be more susceptible to phishing and social engineering attacks because they may be les...
Read More..
Know the top 8 Advantages of Outsou...
The practise of employing a third-party service provider to manage and secure an organization's cloud computing environment is referred to as outsourcing cloud security...
Read More..
Database Hosting for Big savings, G...
In a time when every company generates vast amounts of data, it is only wise to go for database hosting services. ESDS Databa...
Read More..
Core Benefits of Managed Security S...
Complete implementations, insights, and administration of a company's security process are what exactly managed Security Services do. Now With the help of MSS Partner, a company gets 24*7 dedicated monitoring.

Top Managed Security as a Service T...
Why are managed security services in action?
Just as businesses leverage the cloud's scalability, hackers do the same. More DIY harmful tools are now freely accessible and available online, allowi...
Read More..
Cybersecurity - Get it right with C...
Cloud Security solutions can protect your business data, prevent unauthorized access to your data, and control who has access to your data. However, many businesses need ...
Read More..
5 Benefits of Green Cloud Computing...
In terms of green cloud computing, there are different approaches. Besides manufacturing eco-friendly IT hardware, eco-friendly applications promote environmental sustainability by being used in various fields. 'Reduce, Reu...
Read More..
The Blend of Cloud Computing & Arti...
Cloud computing and artificial intelligence are often mentioned in the same breath. If you’re wondering why there’s so much hype about the use of AI and cloud computing, then perhaps you need to look at it from a practical ...
Read More..
How is ESDS contributing to the gov...
With the world being digitalized, it has become vital for government agencies to adopt technologically advanced technologies for the smooth workflow of govern...
Read More..
Your organizations best SOC practic...
There is no way you could leave the ever-evolving threats unattended. Here is how ESDS assists you in outlining the best SOC practices in achieving its mandate of protectin...
Read More..
Breaking The Silence Of The PAM...
How do you become a self-sufficient security champion? PAM should be easier. Get acquainted to the best security practices with ESDS and take your business to the next leve...
Read More..
6 Benefits of Cloud-Based SIEM...
Cloud-based SIEM is a great way to keep your business safe and secure. With Cloud-based SIEM, you can easily monitor and protect your data, including your employees' data, from unauthorized access. You can also keep your bu...
Read More..
Understanding the Tiers of Data Cen...
Data is growing exponentially which requires safe and flexible storage space to further process it, for which data centers play a crucial role in leading...
Read More..
Dark Web Monitoring - Why Your Busi...
Using dark web monitoring, you can gain insight into threat actors and their activities by leveraging the broadest and deepest coverage of dark web sources. Ensure your organization completes cybersecurity with a Dark Web Monit...
Read More..
IS IT THE RIGHT TIME TO MODERNIZE Y...
For how long could your business sustain the legacy burden?
Benefits offered by legacy application modernization are plenty, with some of them being enhanced interoperability with new technologies, platforms, and code...
Read More..
Backing up your data – Myths VS F...
We all know how important data backups are for any business. But do we have all our facts right?
What if we told you, you will be taken aback with your life-long assumptions on backups and those may be resisting you from...

An impactful solution to the challe...
As the amount of Data is growing vastly so is the need for its management and security. Data alignment, smooth integration, and access are the need of the hour and Data Fabric brings that for growing businesses..

Why Are Companies Adopting Cloud Co...
It's no longer just a buzzword - cloud computing has a global market value of $371 billion (and growing). Globally, cloud computing is expected to surpass $832 billion in value by 2025. There are countless reasons why cloud...
Read More..
THINGS TO COME - The Tech Trends Fo...
Today's technology is evolving quickly, enabling quicker change and advancement and accelerating the rate of change. Find out what, when, and how major technological trends will impact your strategic ambitions in the year a...
Read More..
What is Security Monitoring & Who C...
Monitoring networks and infrastructure for compromises, security misconfigurations, and vulnerabilities must be carried out in real-time. And that is where security mon...
Read More..
Why is Website Security Important f...
We are all aware of the risks of having an insecure website. For example, if you are the victim of a cyber-attack, your website may be down for several days, your customer data may be compromised, and you may lose hard-earned m...
Read More..
Cloud Migration: How ESDS Cloud Mig...
Reduced time in the total cost of ownership (TCO), faster delivery time, and enhanced innovation opportunities are just a few benefits of ESDS cloud migration services. Explore why you need cloud migration and what are the exte...
Read More..
Technological leaps come with great...
A company's data may be threatened by ransomware, human error, natural disasters, and hardware failures. In such an event, a Backup and Disaster Recovery solution is a must-have for businesses to return to safe, regular ope...
Read More..
It's all about managing the data ef...
Data has become an invaluable asset for businesses across the globe and managing the data is equally an important task. With the help of Data fabric organizations can secure, manage, and integrate their data in line with the cu...
Read More..
Application Migration to the Cloud...
Has your business realized its potential in modernizing business applications?
Starting with a review of your infrastructure, ESDS works with you to develop an application migration plan that's specific to your ...
Read More..
eNlight WAF | Your specially engine...
How concerned are you with your organization's security posture?
The cost of dealing with a security breach can prove to be alarming to your business. ESDS eNlight WAF is a specially engineered Web Application sec...
Read More..
ARE YOU PREPARED FOR A CYBER EMERGE...
With the increasing number of attacks, your organization must be securely protected from these common threats. ESDS is dedicated to keeping your data safe from disasters of every kind.
Check out our infographic to learn abo...

WHAT DOES PCI DSS MEAN TO YOU IN 20...
If your process for accepting the payments is not PCI DSS certified, you are putting your business at risk. ESDS is PCI certified and it is an integral part of our overall business equation. Learn how to give your PCI complianc...
Read More..
Understanding the impact of Cyber S...
How smart businesses are upgrading their security standard with Cyber Security Mesh?
A cyber-defense strategy with more of a holistic approach that provides better security control is how Cyber security Mesh helps growin...

Better Safe Than Sorry: Alarming En...
Endpoint devices pose a great threat to your business's cybersecurity. Businesses need endpoint protection to prevent ransomware, phishing, malware, and other cyberattacks on critical systems, intellectual property, custome...
Read More..
5 Reasons Why Financial Sectors Mus...
The banking, financial, and insurance industries have migrated to the cloud as digitization has swept across the industry and the general populace. As a result, a company's operations are impacted by cloud computing and how...
Read More..
Innovation is not a side project. D...
The cloud offers more than just affordable IT infrastructure. Cloud computing is the primary catalyst for business innovation as it combines all the components you'll need for innovation—data, processes, and technology—...
Read More..
Here Is Why You Need Disaster Recov...
No one wants to plan for the worst, but, when it happens, you want to be prepared. Planning for a disaster is something every company should consider and find the resources to implement. Whatever solution or model you choose, D...
Read More..
Is your business cyber resilient?...
What is your business’s worst nightmare?
Inevitably, Data loss. It’s no longer a question of “if” fraud happens – rather, it’s a question of how to respond to an attack, and how to prevent it. Cyber resil...

Benefits & Future Prospects of Colo...
Does your business seek a higher premium on decreased maintenance or data security? Or is your business limited on space but demands a robust IT infrastructure? Colocation is the solution here. Get reliable IT infrastructure, ...
Read More..
You Need Cloud Computing to Make Bi...
Structured and unstructured data volumes require increased processing power, storage, and more. In order to perform real-time analytics on big data, the cloud is a perfect platform as it enables higher storage and fast computin...
Read More..
Picking the Best AI Chatbot for You...
Over 64% of company respondents say AI enabled chatbots help businesses provide more customized services to clients. Indeed, chatbot functionalities...
Read More..
16 Best Practices for Endpoint Secu...
The expanding digital world offers many benefits, but it also has some drawbacks. Although, your digital assets, such as user devices like PCs, laptops, servers, smartphone...
Read More..
Document Management System Solving ...
Do manual paper filling and piled-up documents stress you out?
Your business needs a smart move toward a document management system that provides a dependable option that will cut down your paper files, organize b...
Read More..
Shields Up! Guard your websites wit...
The first step toward creating a sustainable and successful business is preparedness against any type of incident. As the world moves faster with digital transformation, cyberattacks are more prone, and these tips help to under...
Read More..
Cloud Computing Stats Part 2...
There are many benefits to making your move to Cloud. Still, wondering whether you should migrate to Cloud? Here are hard-hitting statistics that will compel you to migrate to Cloud and reassures you that the future is in Cloud...
Read More..
10 Cloud Computing Stats to Help yo...
A cloud adoption strategy reduces costs, mitigates risk, and enables scalability of database capabilities. If you haven't already moved to the Cloud, here are statistics demonstrating why you should move to Cloud!
... Read More..
Understanding the Patterns and Effi...
In the competitive and unpredictable market businesses need to stay on the top of their game. With a modern dynamic ecosystem for businesses, cloud-native technology supports requirements to run a public, private or hybrid cl...
Read More..
DDoS attacks will double to over 15...
Web application and server infrastructure protection from DDoS attacks is no longer an option for organizations with an online presence. All websites are now vulnerable to DDoS attacks due to the introduction of DDoS-for-hire s...
Read More..
Database Management System...
Mission-critical record items in databases for businesses have intricate logical connections to a variety of different datasets that expand with the number of users. In order to guarantee a high degree of performance, organizat...
Read More..
5 Major Benefits Of Cloud Computing...
Cloud computing has made technologies—hardware or software—that were previously only accessible to huge corporations easily accessible to small Enterprises as well. Cloud computing has several advantages for your company. ...
Read More..
Privileged Access Management ‘key...
Privileges are prevalent across the digital business world. PAM assists organizations in ensuring that personnel only have access levels required for job performance. PAM also gives security personnel the ability to spot crimin...
Read More..
Is Your Business Protected From Ins...
Users who have access to a company's assets and abuse them intentionally or accidentally are insider threats. Therefore, all organizations need to have a robust internal threats protection strategy. Know what is internal th...
Read More..
The Security of Bank Data: What are...
Banking is the only sector that contains every individual's financial and personal data. As digitization in the banking sector has taken a leap, there are many things added to help banks automate workflow like ESDS BFSI Com...
Read More..
From Legacy to Cloud – Your imper...
Some changes are welcomed, while others are avoided. The necessity of altering business processes, including going remote, virtualizing desktops, and possibly more importantly deciding whether to keep, transfer to the cloud, or...
Read More..
Are You Monitoring what matters?...
Being proactive in order to maintain an organization's IT infrastructure, is no small feat. They are well aware of how crucial it is to continuously monitor all IT activity in order to provide all users with top-notch servi...
Read More..
ESDS's Colocation Data Center Servi...
Lead your critical IT assets with better control and smart monitoring In order to achieve swift workflow with more controlled access to your critical IT needs, rigorous monitoring is the key. An...
Read More..
Rapid Recovery needs Swift Solution...
In this data-driven world, keep your business disaster ready. An exuberant and reliable partner for rapid recovery and disaster solutions is an ideal business strategy for smart leaders. A tactful disaster recovery solution co...
Read More..
'eNlight' Cloud Hosting Benefits fo...
Running SAP solution in the cloud can give numerous advantages to users at all levels of the organization. However, many unforeseen, hidden, and costly issues can develop before, during, and after transferring mission-critical ...
Read More..
SOC-as-a-service - A complete 360 D...
Your organization needs SOC-as-a-service to be safe and secure. With SOC as a service, you'll be able to quickly and easily detect and respond to threats. SOC provides y...
Read More..
Cloud Hosting: 7 Reasons for Your B...
Cloud hosting makes cloud resources available to apps and websites. Unlike traditional hosting, cloud hosting is not implemented on a single server. Instead, the application or website is hosted by a network of connected virtua...
Read More..
SaaS Architecture Applications - Ef...
Leverage business growth with the SaaS Architecture model With versatility and the ability to address issues, SaaS is considered among the significant architectures that can be used to deliver services to customers from anywher...
Read More..
How AI is transforming The Banking ...
The digital marathon began with organizations through numerous phases of digitalization and has set up the Financial Services Firm's Artificial Intelligence phase. Artificial Intelligence is one technology that's goi...
Read More..
Machine Monitoring Your First Step ...
Machine Monitoring systems allow for real-time remote visualization of machine data, including utilization, performance, condition, resource consumption, automated data collection, and AI-based analyses. It optimizes machine op...
Read More..
Public vs GCC Cloud...
Cloud services have made a significant shift in traditional businesses by offering automation in the business workflow. Cloud computing provides automation, high-end security, and scalability according to the organization's...
Read More..
Backup in the Cloud - The way to go...
Data can be put in jeopardy by user error, hacking, sync issues, or malicious hackers. Maintenance and management of backup can take a load on your business. Moving to cloud backups is a smart way that guarantees you security, ...
Read More..
ARE YOU PREPARED FOR A CYBER EMERGE...
It's always the worst time to get a cyberattack. With new cyber-attacks emerging every day, the only question is, how prepared are you to protect your business during cyber emergencies? Let's look at the types of cybera...
Read More...jpg)
Cloud Computing Stats & Facts to Kn...
How a company operates its cloud computing strategy is critical in today's increasingly digital world. The pandemic has hustled cloud usage, which has been growing for several years. However, as the post-pandemic world begi...
Read More..
Why Should You Use ESDS' eNlight We...
A clientless, intelligent cloud-hosted VPN solution from ESDS, eNlight WebVPN provides both incoming and outgoing TCP load balancing technologies and proxy balancing (backend server load balancing) to give you ...
Read More..
Utilizing Cloud Security for Boosti...
Scalability, Flexibility, Storage and Security are among many reasons why businesses are moving on the Cloud. Thanks to the pandemic, the growth of Cloud and Data center services have only accelerated and going forward this gra...
Read More..
Why Is Cloud-Based Banking Infrastr...
In today's digital age, India's banking sector needs to diversify its revenue models from free transactions to new client-based services, which will be the biggest driver of the cloud in the BFSI sector...
Read More..
Co-locate with ESDS to keep costs L...
Co-locate the smarter way with a high-speed redundant infrastructure composed of a speedy network and secure storage that reduces your CAPEX and lets your business scale. Host your mission-critical IT assets in state-of-the-ar...
Read More..
How is the Cloud positioned in 2022...
Cloud computing growth has been skyrocketing over the years and will only keep rising as per reports. Here are some statistics to get an overview of the usage of the cloud and how it is positioned in 2022.

Cloud Computing and Healthcare - A ...
The healthcare sector has been slow on the uptake to have picked up drastically over the years in implementing cloud technology. With more and more use cases of cloud computing, the sector is coming to realize the true potentia...
Read More..
Public and Private Cloud: 10 Factor...
Gist about Public & Private Cloud
The Public Cloud
A third-party provider provides shared, on-demand infrastructure and resources through public clouds. In a public cloud dep...

IoT Sensors to help in improving Ai...
With the hope to make this world a better place for the coming generations is to improving the air quality, the IoT Internet of Things looks like a promising option. IoT sensors can track, analyze and share data on the pollutio...
Read More..
Know the Top 10 Benefits of Disaste...
Disaster recovery has been the most crucial part of any small, medium, or large organization. Every business or organization mandatorily has business-critical information to be kept safe from any attack/mishap or disaster. Read More..

8 Reasons to choose SaaS Products ...
Software as a Service, or SaaS, is a cloud-based software delivery model that allows you to access software solutions via the internet. This unique delivery approach has several advantages. SaaS enables businesses to pass owne...
Read More..
Your Business Is Not as Secure as Y...
SIEM solutions are a must-have as they allow organizations to collect and analyze log data from all of their digital assets in one place. They can recreate incidents from the past or analyze new ones to detect suspicious activi...
Read More..
Know the Most About Community Cloud...
Security and compliance, compute resources, and applications are typically similar among organizations from the same community (For e.g. Bank, Education, Government, etc.). A community cloud combines the featur...
Read More..
Cost-Effective & Seamless Cross Pla...
As an expert in cross-platform data migrations, ESDS has successfully processed migrations related to a wide range of organization database packages and operating systems. Whether you are migrating an Oracle database from an HP...
Read More..
6 Cloud Computing Myths and Facts t...
One of the trending topics with many myths is Cloud Computing. I would rather put it, what is cloud computing without myths? You may think a certain statement about cloud computing is true, but that may turn out to be otherwise...
Read More...jpg)
Elevate your Business Growth with a...
In order to scale up your business growth in this Data-Driven industry, developing an effective Data Strategy is a must. Organized data gives clarity to making important decisions and other strategic actions for better business...
Read More..
The Impact of Cloud Computing in th...
Retailers can use the cloud to replace legacy systems with infrastructure that allows them to react to changing market conditions. Aside from more basic benefits like cost savings and disaster preparation, the cloud has enticed...
Read More..
Using SaaS is a SMART move...
SaaS is a feature-rich cloud-based solution that offers customers scalable, secured, easily accessible, and compatible software solutions saving huge costs. The many benefits of SaaS have made it the most rapidly rising cloud c...
Read More..
Your business can benefit from AI a...
Your business is future-proof and can benefit exponentially from AI and Cloud Collaboration. AI and Cloud together will help your business thrive with greater efficiency, productivity, and digital security. Read on to know mo...
Read More..
Cloud Storage and eCOS- The Best Cl...
Cloud storage enables you to keep data and files in a remote location that you can access via the internet or a dedicated private network connection. Data that you send to a third-party cloud service for storage becomes their r...
Read More..
Top Digital Banking Trends For 2022...
Over the last few years, the digital banking landscape has expanded and evolved significantly. This digital banking evolution aims at a more data-driven, customer-centric, and personalized banking experience. As each financial ...
Read More..
An Overview of Hybrid Cloud Network...
Hybrid cloud networking enables organizations to leverage the increased capacity, scale, and affordable prices of the public cloud when needed and is connected through telecom services and supporting infrastructure. A ...
Read More..
Successfully Migrate Your Emails- K...
If you intend to migrate emails from your on-premises system to an email client, you are on the right track toward secure email migration and management. By switching to a new email client, you can solve many problems in your o...
Read More..
eNlight 360- Your Clouds' Orchestra...
CIOs and CTOs require an orchestration tool to systematize interactions within Private and Public Cloud deployments for increased efficiency. Achieving a cohesive workflow without such a tool is difficult because simplifying en...
Read More..
What to expect from your SOC-as-a-S...
SOC as a Service is the most affordable way to have maximum cyber security. Also, it brings several benefits such as faster detection, threat intelligence, and cyber risk mitigation. Get all the cyber security assistance you ...
Read More..
5 Technologies To Digitally Transfo...
Various technologies are being used across the world that has aged in years and is overhauling the logistics sector. These technologies still are infants when it comes to the digital transformation in the Indian logistics secto...
Read More..
Understanding PaaS in Cloud Computi...
In Cloud Computing, Platform as a Service is one of the popular business models known for its automation and resourceful technological advantages. Understand and evaluate your business needs for yielding results with Cloud comp...
Read More..
Digital Banking Cybersecurity Risks...
As the world becomes more digitally connected, fraudsters have more entry points; as a result, cybersecurity in digital banking has become more essential than ever. There have been data breaches at technologically advanced bank...
Read More..
5 major advantages of cloud computi...
A report by Market research future states that the manufacturing sector is forecasted to attain $111.9 Bn worth of cloud computing investment by 2024. Refer to the infographic to know about the major advantages of cloud computi...
Read More..
How AI with Machine Learning is cha...
It has always been our goal to build technologies that mimic human intelligence. That's why Machine Learning and AI is at the center of today's industries, ready to turn their aspirations into realities.

Why Do You Need eNlight SIEM?...
SIEM (Security Information and Event Management) solutions provide enterprises with network security insights and real-time monitoring for network gadgets, frameworks, and applications. SIEM tools are best used for real-time v...
Read More..
A Secure, Cost-effective & CERT- In...
Cybersecurity has been an increasing concern for many organizations and with the likelihood of business assets being damaged or destroyed, a multi-layered secure vVAPT lets your business take control by securing your sensitive ...
Read More..
Accelerate Smart Manufacturing To O...
Smart manufacturing allows a technology-driven and collaborative approach to run factories that connects machinery via the internet. Smart manufacturing improves the manufacturing and production process.

Why is Data Security and Privacy Es...
Data security and privacy have always been a priority for everyone. Data privacy is becoming more important as more of our data is digital and we share more information online. A single firm may hold the personal information of...
Read More..
Do You Know These Top 9 Uses of Clo...
Cloud computing has become the ultimate choice for businesses to gain popularity in the thriving market. Cloud computing not only helps in potential business operation transformation but also offers an affordable business solut...
Read More..
4 Benefits of Endpoint Security tha...
Endpoint Security or Endpoint Protection is a method of securing endpoints such as desktops, laptops, and mobile devices in a company's network from being exploited by malicious actors and ensuring cybersecurity.
...
Read More..
Understanding Significance of Cyber...
With the increasing number of online attacks & other threat vectors, CIOs have become mandatory to ensure cybersecurity in digital banking. With a robust banking cybersecurity mechanism in place, it secures user-critical applic...
Read More..
Understanding the process of Email ...
Emails hold crucial business data, and businesses need a reliable email service, where their data is smoothly transferred and stored safely for their daily activities. Choosing the right tool is the first and foremost important...
Read More..
11 Best Data Recovery Solutions...
If you work with electronic devices or servers, you may experience data loss; if not, lucky you! Perhaps your cellphone, laptop, computer, pen drive, or server containing information suddenly lost the data due to a mishap, leav...
Read More..
7 Key Points On Managed Vs. Unmanag...
Cloud services are booming in the market for offering various organizational benefits. Software, Platform, and Infrastructure are the cloud services provided by third-party providers, available to end-users via the internet. Read More..

2022 Forecast for the Mobile Applic...
The ever-evolving mobile application market has been on the rise for the past 2 years. To grab and hold the fragile attention span of the users, businesses are investing time and money into understanding and analyzing the use...
Read More..
Strengthen your cyber attack surfac...
Moving closer to the depths of digitization, reinforcing cyber security has become crucial now more than ever. To block and minimize the attack impact, businesses are embracing new technologies with a stronger cyber security pl...
Read More..
Predictions for Data Center Industr...
2022 seems to be a year full of technological disruptions that will transform the Data Center industry. Some notable trends include implementing advanced technologies like AI, while some include major infrastructure changes. Read More..

What is Blockchain Technology?...
Blockchain is a record of any digital asset, unalterable and transparent, through the use of decentralization and cryptographic hashing. Blockchain technology is simply defined as a decentralized, distributed ledger that record...
Read More..
How SaaS will benefit your company ...
Today, SaaS (Software-as-a-Service) solutions are a chunk of almost every commercial workflow. It’s a given because of the accessibility, versatility, cost-effectiveness, and agility of these offerings. With SaaS trends takin...
Read More..
Understanding How Managed Services ...
With Managed Services, CIOs & IT Heads overcome the stress of managing their in-house services & focus on business growth competencies. Here are the benefits that MSPs offer & their future in India. Managed Service Providers li...
Read More..
Security Elevates The True Potentia...
IoT security is a powerful way to keep your IoT systems safe. IoT security protects IoT systems and IoT networks from threats and breaches, helps in identifying, mitigating, and fixing vulnerabilities. IoT security assures the ...
Read More..
8 Compelling Reasons Why a Managed ...
A Managed Security Services Provider helps businesses combat all forms of cyberattacks while allowing CIOs to focus on their growth areas. What are other benefits that a Security Provider offers? Find out below.

Common IoT Security Challenges...
IoT is the next emerging technology that has transformed how we communicate with each other & devices. However, this interconnectivity can bring in certain security challenges. The following are some of these common challenges ...
Read More..
We Are Living in the CLOUDS...
We are using Cloud services all the time even without realizing it. When you use any online service, be it sending emails, listening to music, storing pictures, playing online games, or accessing files. Cloud computing is the d...
Read More..
Disaster Recovery Using Cloud: Imp...
DRaaS on the Cloud gives you a single independent DR Site to act as backup for your Multiple Datacenters across the globe. It also gives you flexible, easily scalable deployment and storage options. The time taken for recovery...
Read More..
Why Safeguard Cybersecurity While M...
Organizations and enterprises migrating to cloud-based services and ecosystem is a general phenomenon now. The trend has rather increased but still, there are people sceptical about the potential of cloud computing. let us take...
Read More..
How Technology is Enabling Smart Fa...
Smart farming is the most cutting-edge approach to transforming the agriculture sector. Smart Farming applies technologies such as IoT, AI & ML, Robotics, Drones, etc. to keep farms and farm livestock in top conditions, incre...
Read More..
Benefits, Hurdles & Future Scope of...
The digital progression in the banking industry in the last few years has been remarkable. With cloud-based solutions provide paperless banking services and further leading to a quick and improved end-user experience. Let us id...
Read More..
5 Reasons Why You Need a Cloud ERP ...
Cloud offers a wide array of benefits to end-users, from Scalability to Availability, ensuring data concurrency. So, here are the top compelling benefits that a CIO gets with a Cloud ERP Solution compared to traditional & on-pr...
Read More..
5 Tips for Securing Dedicated Serve...
In a Dedicated Server Hosting, the computing resources are not shared with anyone on the hosting server. Find out some of the common yet effective ways to ensure maximum security of Dedicated Servers.

How AI & Machine Learning Benefit t...
Technologies like Artificial Intelligence and Machine Learning have played a major role in transforming various modern-day industries. Let's determine the key benefits that the Insurance industry gets with these technologie...
Read More..
Practical Tips for a Secure Cloud E...
Cloud Computing is one of the most fastest adopted technology in recent times. As an end-user, how can one ensure that his Cloud Environment remains secure? Scroll down and discover these effective tips for a secure Cloud Inves...
Read More..
Benefits, Use Cases and Future Scop...
A CDN or Content Delivery Network Solution refers to the network of Data Centers and geographically distributed localized servers. Let's identify their benefits, use cases, and projected market growth for CDN Solutions thro...
Read More..
Top 5 Facts You Might be Curious to...
With the potential to transform the way business is done, AI has gained immense recognition from investors. Enterprises are leveraging the power of Artificial Intelligence to construct robots replicating human behavior enabling...
Read More..
Get Enhanced Cybersecurity Posture ...
ESDS Security Services - A trusted name for providing the best-in-class Managed Security that ensures complete protection of user-critical data by enhancing an organization's cybersecurity posture & hosting it within multi...
Read More..
Significance of Big Data in Cloud...
Today, leading organizations host their Big Data in Cloud owing to the multiple benefits that Cloud Computing has to offer. When Cloud hosting, this Big Data can be made readily available anywhere and anytime through secured me...
Read More..
ESDS - The Cloud of India...
The most trusted Cloud Service Provider in India has transformed the operations of various industries through its Cloud technology. With its Cloud services, ESDS serves the nation by ensuring the Data stored in its Cloud server...
Read More..
Steps Involved in an Effective Disa...
A Disaster Recovery Plan is essential for every business for recovering access and functionality to its IT infrastructure after events like a natural disaster, cyber-attacks, or even business disruptions. According to a survey,...
Read More..
Key Elements of a Disaster Recovery...
DR: Elements on Disaster Recovery Plan : The infographic represents the elements of How Disaster Recovery can be planned and the organization's performance can be enhanced and rescued from any kind of Disaster.
... Read More..
High Alert- Hacker Might Be Spying ...
High alert – Hacker is ready to attack! The year 2019 has seen a huge number of cyberattacks incurring unbearable losses to companies.VTMScan offers Content Change Monitoring, a unique feature that notifies the website owne...
Read More..
Artificial Intelligence Facts you s...
Artificial Intelligence is enhancing our lives making them much better and easier. Businesses are investing in AI to optimize their operational procedures improving business growth. The digital era will soon find robots working...
Read More..
IoT Stats Changing Manufacturing La...
In the era of IIoT and Digital Transformation, IoT investments are driving the manufacturing industry towards digitization. The stats justify how the Indian manufacturing industry is leveraging IoT. Internet of Things (IoT) is...
Read More..
IoT Touching Your Life...
IoT is not just a buzzword. It is closer to you than you think. Check out these facts about IoT that show its growth by 2020. IoT allows companies to automate processes and save money on labor. It also reduces waste and...
Read More..
Cloud Hosting in India...
What trends are going to dominate the Indian Cloud Hosting Market in the coming time?
For a better experience, cloud services will collaborate with IoT and Big Data. Cloud-based services...

Amazon EC2 v/s eNlight Cloud - Clou...
Amazon EC2 v/s eNlight Cloud - The Following Infographic will elaborate on the key differences between Amazon EC2 & ESDS.
eNlight Cloud is a cloud computing platform based on the Xen virtualization platform by ESDS Softw...

eMagic - Datacenter Infrastructure ...
eMagic is a web-based system for IT asset management, device deployment, comprehensive server monitoring, and network management in datacenters spread across different geo-locations. eMagic is about three clicks - Build, Deploy...
Read More..
Steps To Migrate Your Cloud...
Cloud Migration is the process that refers to moving/migrating the data, resources, and servers from a physical environment to the cloud infrastructure. The migration can also be from one cloud service provide...
Read More..
Cloud Trends 2019 | Technology Expe...
The beginning of a year starts with calculations and stats of the previous so that we can know what’s here to stay and what’s not. Technologies keep changing and the yearly trends need to be known. Check out the cloud compu...
Read More..
A Dozen Cloud Facts Revealed!...
Cloud computing is all about renting computing services. This idea first came in the 1950s. In making cloud computing cloud computing has evolved and emerged a great deal since its inception. Here is an intuitive infographic...
Read More..
A Foolproof Formula for Easy Disast...
Any kind of unplanned downtime destructions will definitely cripple the business. A Disaster Recovery Plan (DRP) is a must to minimize IT risk and ensure business continuity.
Develop and deploy a foolproof Disaster R...
Read More..
ESDS - VTMScan...
According to an internet estimate, the average cost of a data breach is $3.92 million. This is a significant sum for any company, making CTOs and other important corporate decision-makers always concerned about data breaches an...
Read More...jpg)
The 6 WH SAP data migration questio...
6 ‘WH’ SAP data migration
We present you the checklist of ‘WH’ questions that are needed to ask your Cloud Service Provider (CSP) when you plan your SAP Data Migration. Scroll through this colorful guide to ...
Read More..
Big Data : A Competitive Weapon for...
Today, too many organizations using big data seem only to be limited by what they dare admit to the public. From traffic patterns to music downloads to web history & medical records data is recorded stored and analyzed to enabl...
Read More..
enRise - Human Resource Management ...
A web-based HRMS system automating an organization's HR processes. the system is a comprehensive, flexible, and easy-to-use solution designed to manage all key HR operations delivering an exuberant experience to enterprises...
Read More..
Website Security Scanner | Online V...
Website owners are continuously striving to better their businesses; however, they are unaware that web security is at the heart of every online business nowadays. Quality was always higher for a legitimate website and a secure...
Read More..
Datacenter Tier Cheat Sheet...
Data Center Tiering was introduced by Uptime Institute where the Data Centers were classified into 4 Tiers – Tier 1, Tier 2, Tier 3, and Tier 4. A data center's design is based on a network of computing and s...
Read More..
Project Green Connect – ESDS Comm...
ESDS is strongly committed to Green IT and has laid strategic plans right from its inception. We are rigid promoters of energy recycling and energy conservation which is best epitomized in our energy-efficient...
Read More..
Hybrid Cloud – The Answer & the F...
Visionary enterprises have taken the Hybrid approach to combine the capabilities of Public and Private Cloud. Hybrid Cloud is a versatile computing model that supports variable workloads and allows modifications of services tha...
Read More..
Redefining Cloud Technology With eN...
Organizations have been spending a fortune on IT infrastructure to build a stack efficient enough to help them stay ahead of their business demands. eNlight gives you the right cloud infrastructure, perfectly pooled resources,...
Read More..
India Prone to Attack by Cyber-crim...
India has already seen a 37 percent increase in cyber-attacks in the first quarter of 2020. Data leakage, use of insecure Wi-Fi networks, phishing attempts, ransomware, malware, and apps with poor encryption (also known as brok...
Read More..
Cloud Computing and its Features...
Simply put, cloud computing is the delivery of computing services—including servers, storage, databases, networking, software, analytics, and intelligence—over the Internet (“the cloud”) to offer faster innovation,...
Read More..
Managed Services In Cloud – ESDS ...
Managed services have come a long way since the days of outsourcing complex IT projects to pricey consultants. Managed services enable companies to Focus on their core business by increasing efficiency, reduce costs, & leverag...
Read More..
Datacenters An Integral Part of Our...
Datacenters An Integral Part of Our Lives: How Execution of the most crucial elements of our day-to-day life is impossible without datacenters. Datacenters are centralized locations with computing resources and crucial teleco...
Read More..
Cyber Crime : Statistics & Trends...
Recent trends, side effects of a global pandemic, and cybersecurity statistics reveal a huge increase in hacked and breached data from sources that are increasingly common in the workplace, like mobile and IoT devices. Cybercri...
Read More..
Cloud Statistics 2015 Vs 2016...
Cloud statistics 2015 Vs 2016 highlights the latest trends and swifts in the cloud strategy over a year that can help guide you to set benchmarks for your organization. The time series shows the forecast global revenue of clou...
Read More..
Cloud Computing : The game changer ...
Advances in technology and consumer behavior are leading to a transformation in the way video content is delivered to consumers. Due to this, there is a migration away from traditional broadcasting models and platforms towards...
Read More..
Why is your private cloud beginning...
Companies are likely to give in to the sirens of the Private Cloud. Agility, ease of deployment, and administration are indeed all assets that call for these infrastructures, but the creation and use of such a platform are ca...
Read More..
Cloud Security Standards in eNlight...
eNlight Cloud service has been designed and developed to address all security needs and prevent the threats existing in today’s environment to ensure the smooth functioning of business operations. Find out more info with this...
Read More..
Embrace the Future with Cloud Compu...
Here's a look at some of the cloud computing trends expected to loom large in 2021. The global public cloud infrastructure market will grow 35 percent to $120 billion in 2021, as the cloud continues to “take center stage�...
Read More..
BFSI vertical`s evolution with Clou...
Cloud Computing is buzzing in technology spheres. Banking & Financial Service Institutions are possibly the most advanced in terms of technology adoption and use it as a key differentiator, BFSI sector is not behind in leverag...
Read More..
Unraveling the Myths on DCIM...
Attempt on unfolding the myths about DCIM software that is commonly accepted, Reality being different and advantageous for Datacenters as well as enterprises. Datacenter management software has become an integral part of plann...
Read More..
Pros and Cons of Multicloud...
Combinations of the service providers for varied applications with different platforms make a Multicloud environment, it can also be said as a Heterogeneous Cloud platform. Multicloud platform comes with some benefits and some ...
Read More..
Enable Cloud anytime, anywhere with...
eNlight Cloud Mobile App enables Cloud anytime, anywhere providing complete flexibility. Check out below cogent features of eNlight Cloud App. eNlight Mobile APP provides a real-time insight into the status of any of your s...
Read More..
Migrating Enterprise Data to the Cl...
The following Infographic will Assess you with few Important points to consider and address as you start migrating to the cloud. There are various types of cloud migrations an enterprise can perform. One common model is the t...
Read More..