IPSec – what is it ?
IPSec – is a widely used technology which allows you to add an additional level of encryption and authentication / message integrity to any traffic, which is transmitted over IP. It is used both to create a VPN, or just for protecting individual hosts or data.
ipsec
Principally, the IPSec can be divided into three separate parts:
1. A protocol for AH, which allows you to sign / hash IP-packets, which allows the sender to verify the authenticity and integrity of the package. It just adds a signature to a package and does not encrypt it.
2. Protocol ESP – Encapsulated Security Payload – allows you to encrypt all data in the package as a whole, using different algorithms.
3. Minutes of IKE, which can optionally be used to exchange encryption keys between the parties.
Basically, the authentication of the parties uses RSA-certificate or shared key. With this choice, it depends on the problem. In general, RSA-certificates are a more scalable option, especially in the presence of a distributed network with multiple connections between hosts or routers, as in this case, each node is sufficient to have only a certificate of your Certificate Authority (CA) to authenticate the sender, and not a separate passphrase for each connection.
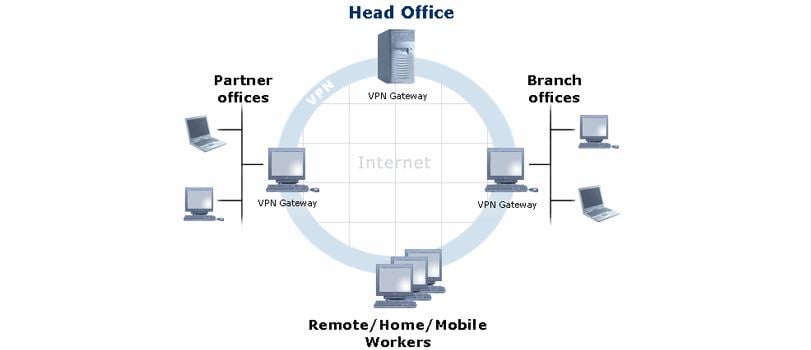
IPSec can be used in two different modes that have different applications.
1. Transport mode: Just encrypt / sign data packets in accordance with prescribed policies. Used in the compounds of host-host.
2. Tunnel mode: Is used on routers to create encrypted tunnels between private networks over public networks such as the Internet. Characterized in that, the traffic from the protected network is encapsulated in the IP-packets with headers and encrypted / signed, then sent to another router, which it decodes and passes on.
Thus, there are different modes in which you can use IPSec:
1. Host-host connection.
2. Connection host gateway.
3. Gateway connection gateway.
In all three cases, there is a slightly different approach, especially in the mobile version of the host gateway, where the address of the mobile dedicated hosting is not known beforehand.
Moreover, for some operating systems, there are several implementations of IPSec-stack, which can be configured differently (although the concept is the same everywhere).
The main difficulty in installing IPSec-connections between different OS / devices is the possible incompatibility between implementations or different sets of supported protocols and authentication methods.
