SOAR Explained: Workflow from Alert to Resolution

In today’s digital world, security teams face a flood of alerts every day. Handling them one by one with manual checks takes time and raises the risk of missing real threats. This is where Security Orchestration, Automation, and Response (SOAR) makes a difference. SOAR speeds up the alert to response flow with accuracy and consistency. When added to a Security Operations Center (SOC), it helps teams cut down manual work, stay less stressed, and resolve threats faster.
A strong SOAR use case in an automation SOC goes beyond basic alert handling. It connects different security tools, automates repetitive tasks, and supports smarter decision-making at the right moment. From phishing emails to insider threats, SOAR enables SOC teams to act within minutes instead of hours. And they can do this while keeping accuracy high and reducing risks.
What is SOAR?
SOAR stands for Security Orchestration, Automation, and Response. It is a security system that connects different tools, processes, and teams into one simple workflow. With SOAR, SOC teams can smoothly move from alert to response flow without wasting time.
Here’s how it works:
- Orchestration: SOAR brings together different security systems like SIEM, firewalls, EDR, and threat feeds so they work in sync.
- Automation: Repetitive jobs such as IP lookups, malware checks, or isolating a user account are handled automatically. Th is “hands-free” step saves time and boosts SOC efficiency.
- Response: Once an alert is confirmed, SOAR guides or fully automates the right actions. It can contain, fix, and recover from incidents quickly.
Example of a SOAR Use Case
Imagine your SOC team gets an alert for a phishing email.
Here’s what happens with SOAR:
- It extracts key details from the email.
- Runs a threat intelligence check.
- Quarantines the email before it spreads.
- Updates the incident log instantly.
All of this happens automatically, with little to no human help. That means analysts can focus on deeper investigation, strategic threat hunting, or policy refinement.
Why Automation SOC Needs SOAR? By adding SOAR into automation SOC workflows, businesses create a faster and smarter defense system. Instead of reacting late, they can stop threats early and reduce damage. SOAR makes the SOC stronger, more reliable, and ready for the future.
Key Components of SOAR
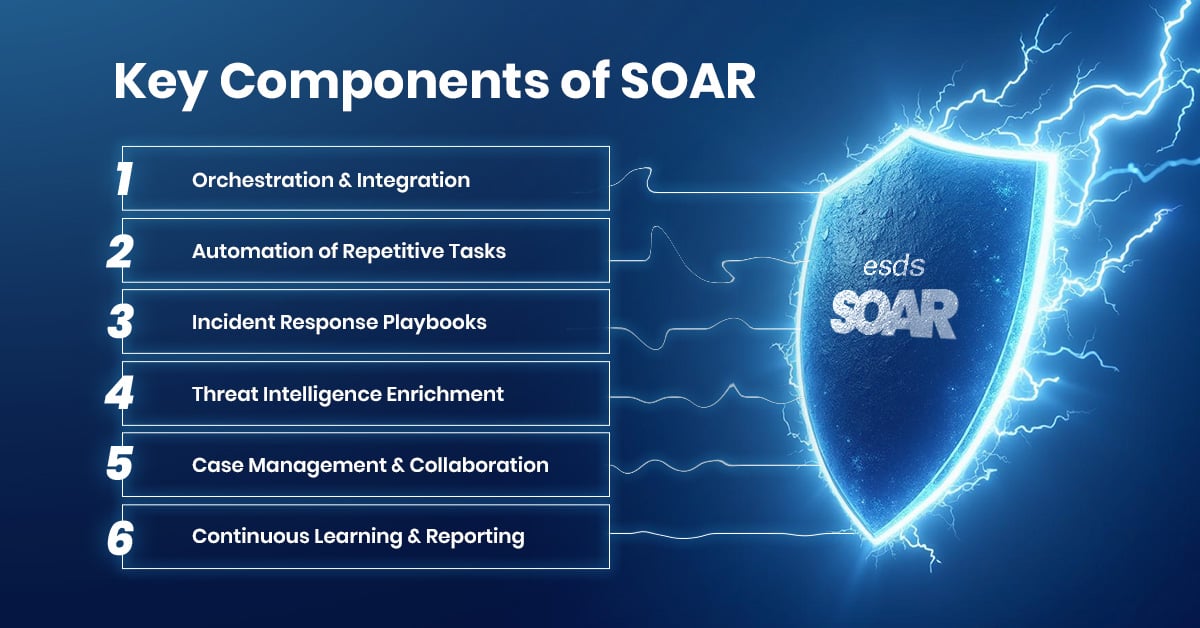
Security Orchestration, Automation, and Response (SOAR) brings together important tools and processes to make the alert to response flow faster and easier inside a modern SOC. It helps security teams make quicker decisions, follow consistent workflows, and reduce stress from endless alerts. Here’s how SOAR works:
1. Orchestration & Integration
SOAR connects all your security tools into one platform. This includes SIEM, firewalls, intelligence feeds, scanners, and ticketing systems. With this automation SOC setup, every alert gets extra context from multiple sources. That means better visibility and no more isolated responses.
2. Automation of Repetitive Task
Many alerts are routine and repetitive. SOAR takes care of these tasks automatically. Examples include checking phishing emails, blocking suspicious IPs, or suspending a user account. This automation in SOC cuts down manual work, shortens response time, and makes remediation actions more consistent.
3. Incident Response Playbooks
SOAR uses playbooks, which are step-by-step workflows for handling incidents. These playbooks define the alert to response flow from the moment a threat is detected to the point it’s contained and resolved. They ensure a standard process while still allowing flexibility when needed.
4. Threat Intelligence Enrichment
SOAR collects threat data from both inside logs and outside intelligence feeds adding rich context to each alert. This gives analysts a clear picture of each alert and helps them quickly separate false alarms from real threats.
5. Case Management & Collaboration
SOAR makes teamwork easier. It has built-in case management features where analysts can document actions, share findings, and work together in real time. This improves knowledge retention and well driven communication across teams, time zones, and even different offices.
6. Continuous Learning & Reporting
Every incident handled by SOAR is stored for future learning. This data helps with compliance reports, reviews, and trend analysis. Over time, the system gets smarter by improving automation logic and fine-tuning workflows for new threats.
SOAR Workflow: From Alert to Resolution
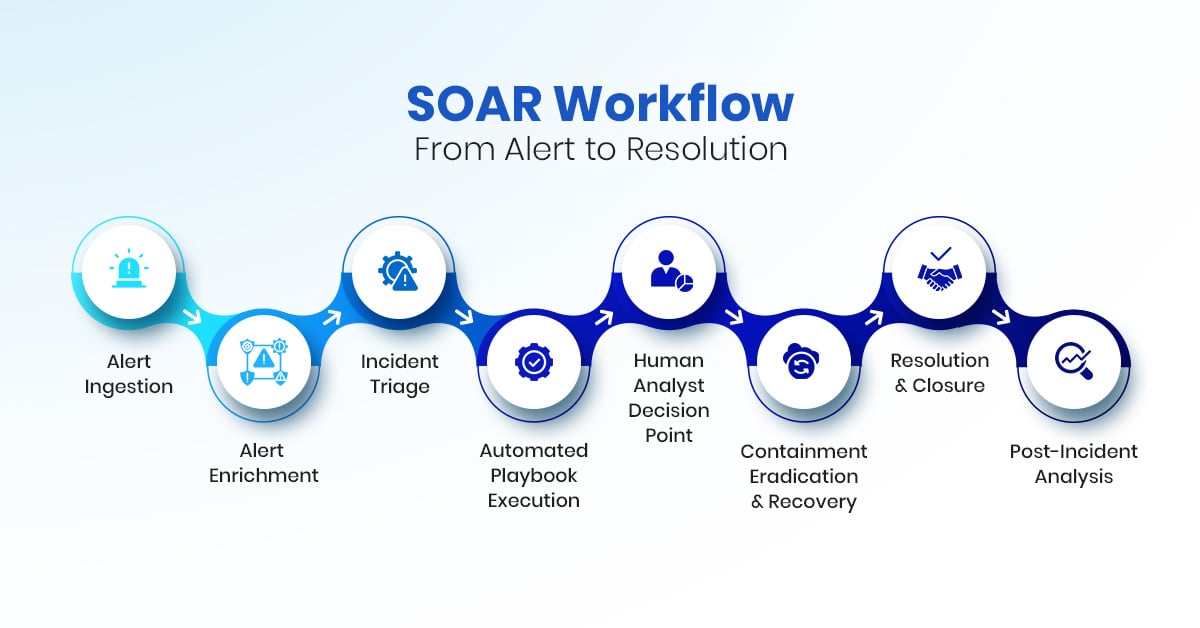
A SOAR workflow helps SOC teams handle alerts in a smooth, step-by-step process. It reduces noise, adds context, and guides actions until the incident is fully resolved. This makes the alert to response flow faster and more reliable in an automation SOC.
Here’s how the process works:
1. Alert Ingestion
- Alerts come from many sources like SIEM, threat intelligence feeds, and endpoint security tools.
- Security event data may include correlated base events, such as logs from a “Remote Port Scan Detected” scenario, which provide valuable investigative context.
- The system filters and groups alert to cut down duplicates and reduce noise. This way, only meaningful alerts move forward into the response flow.
2. Alert Enrichment
- SOAR adds more context to each alert. Predefined classification rules act as pre-processors, tagging alerts and linking them to relevant action plans or playbooks.
- It pulls extra details such as IP addresses, usernames, timestamps, and related historical events, to populate case details.
- Modern SOAR platforms further enhance alerts using automated lookups (IPs, URLs, file hashes) and asset inventory checks, helping analysts understand the potential impact faster.
3. Incident Triage
- The enriched alerts are grouped into cases. If alerts are related, they are linked together under one case.
- The system then assigns severity levels, helping SOC teams know which alerts need urgent attention.
- Automated dispatch rules route cases to the right analyst or SOC team, applying labels or watchers as needed to streamline visibility.
4. Automated Playbook Execution
- SOAR runs playbooks to handle incidents step by step.
- High-severity threats are given priority.
- They may include synchronous tasks (e.g., threat intelligence enrichment) and asynchronous actions (e.g., isolating endpoints, blocking IPs, or disabling compromised accounts).
- For example, a typical SOAR use case could look like this:
- Isolate the endpoint → Block the IP → Notify the user → Update the case file.
- This automation ensures quick action with little manual effort.
5. Human Analyst Decision Point
- Not every incident can be solved by automation, there might be situations when further manual investigation is needed.
- When needed, analysts step in to validate results, perform deeper checks, or roll back actions.
- If a case is serious, they can escalate it to a higher team.
6. Containment, Eradication & Recovery
- Depending on the attack, SOAR takes action to stop the threat.
- This may include blocking an IP, quarantining phishing emails, or removing malware.
- Rollback features in SOAR add a safeguard against false positives by allowing reversal of certain automated actions.
- Recovery steps then restore systems back to safe working order.
7. Resolution & Closure
- Once resolved, the case is closed.
- If a playbook includes a closure step, the case is automatically marked as resolved; otherwise, analysts close it manually after confirming remediation.
- All evidence, actions, and notes are saved in the system. This helps with audits and keeps the SOC ready for compliance checks.
8. Post-Incident Analysis
- After closure, the SOC reviews what worked and what needs improvement.
- Playbooks are fine-tuned, automation rules are updated, and the system learns from past incidents.
- This constant learning makes the automation SOC stronger and faster at handling new threats.
Benefits of SOAR in This Workflow
Bringing Security Orchestration, Automation, and Response (SOAR) into your SOC automation workflow changes the way threats are mitigated.
It makes the alert to response flow faster, smoother, and more reliable. Instead of drowning in alerts, your team gets clear signals they can act on right away.
Here’s how SOAR helps:
- Faster Incident Resolution: Automated playbooks cut down manual steps. Analysts can respond within seconds of an alert.
- Reduced Alert Fatigue: SOAR filters out false alarms and highlights real risks. Your team spends time only on what matters.
- Consistent Responses: Every incident follows the same proven process. This reduces mistakes and builds trust in your workflow.
- Smarter Use of SOC Resources: Routine checks like IP lookups, malware scans, and log reviews run in the background. Analysts can focus on deeper threat hunting.
- Seamless Tool Integration: SOAR links your SIEM, threat feeds, and endpoint tools together for one connected response system.
- Full Visibility: From the first alert to the final fix, the SOC team sees everything in one place and in real time.
The result?
A smarter and more agile and proactive SOC that detects, responds, and prevents threats before they can cause damage.
Use Cases of SOAR
Security Orchestration, Automation, and Response (SOAR) makes life easier for Security Operations Centers (SOCs). Instead of wasting time on manual work, teams can use SOAR to connect tools, automate tasks, and respond to threats faster.
Think of it as a smart helper that keeps the alert to response flow smooth and quick. With the right setup, SOAR can handle different types of cyber threats and reduce the pressure on your security team.
Here are some of the most common SOAR use cases where organizations see real results:
| SOAR Use Case | How It Works | Result / Benefit |
| Phishing Email Investigation & Response | • Suspicious email flagged • SOAR enriches data with sender details, URL/IP checks, and sandbox scans • Malicious emails quarantined, users alerted, and blocking rules applied | Faster remediation, reduced manual effort, prevents widespread compromise |
| Ransomware Containment | • Isolates infected endpoints • Triggers forensic collection • Initiates backup and restoration protocols | Minimizes downtime, prevents data loss, quick containment |
| Threat Intelligence Integration | • Ingests external threat feeds • Correlates with internal logs • Automated blocking across firewalls, endpoints, and cloud access points | Near-instant, closed-loop detection and response |
| Insider Threat Detection | • Abnormal activity flagged by UEBA • SOAR validates with HR, identity, and endpoint logs • Suspicious account access is suspended automatically | Early detection of malicious insiders, reduces insider risks |
| Incident Reporting & Compliance Automation | • Auto-generates incident reports with full logs • Ensures compliance documentation • Maintains audit trail for review | Meets strict BFSI & govt. regulations, avoids reporting delays |
In essence, SOAR’s automation SOC capabilities transform the traditional, manual security process into a fast, accurate, and scalable defense system turning an overwhelming flood of alerts into a smooth, orchestrated alert to response flow.
Best Practices for Implementing SOAR
Setting up Security Orchestration, Automation, and Response (SOAR) is not only about adding new tools. It is about improving how your Security Operations Center (SOC) works every day. With the right approach, SOAR can make your alert to response flow faster, cut down human mistakes, and help analysts handle incidents with confidence.
Here are five best practices to make sure your SOAR setup gives the best results:
1. Identify High-Value SOAR Use Cases First
Pick the SOAR use case that brings the most value to your team. Good starting points include phishing investigations, malware containment, or insider threat detection. These tasks are often repetitive and high in volume, which makes them perfect for automation. Your SOC team can quickly experience efficiency gains while demonstrating measurable ROI to stakeholders..
2. Connect Smoothly with Existing SOC Tools
The real strength of SOAR comes when it links with your automation SOC tools like SIEM, firewalls, endpoint detection, and threat intelligence platforms. Make sure these systems connect properly so your workflows run from start to finish without manual steps slowing them down.
3. Standardize and Automate the Alert to Response Flow
Map out the full path of an incident, from detection to resolution. Define each step clearly, including actions and decision points. This creates a consistent process and ensures even junior analysts can follow playbooks to close incidents successfully.
4. Establish Measurable Metrics and KPIs
Track numbers like mean time to detect (MTTD), mean time to respond (MTTR), how many incidents are resolved automatically, and hours saved for analysts. These continuous measurements show progress and help fine-tune your SOAR workflows prove the value of automation SOC operations over time.
5. Train Analysts and Continuously Update Playbooks
Tools alone are not enough. Analysts need regular training to understand SOAR workflows and adjust them for new threats. Keep updating playbooks with the latest threat intelligence and lessons learned from past incidents.
By following these practices, your organization can build an automation-driven SOC that is faster, smarter, and ready to handle modern security challenges.
Differences between SOAR, SIEM and XDR
Understanding the difference between SOAR, SIEM, and XDR helps security teams choose the right tools for their workflows. Each has a unique role in protecting organizations from threats.
- SOAR (Security Orchestration, Automation, and Response) – SOAR helps security teams save time by automating tasks. It connects different security tools and creates a clear alert to response flow. This makes it faster incident detection, investigation, and response. SOAR is often used in automation SOC to improve efficiency.
- SIEM (Security Information and Event Management) – SIEM focuses on collecting and analyzing logs from many systems. It looks at data from servers, networks, and applications to find suspicious activity. SIEM alerts teams when something unusual happens and supports further investigation.
- XDR (Extended Detection and Response) – XDR brings everything together. It monitors endpoints, networks, cloud, and other layers in one view. With this, teams can detect threats and respond faster. XDR creates a unified defense by combining multiple sources of security data.
| Feature / Aspect | SOAR (Security Orchestration, Automation, and Response) | SIEM (Security Information and Event Management) | XDR (Extended Detection and Response) |
| Primary Purpose | Automates incident response, orchestrates workflows, and integrates multiple security tools for faster resolution. | Collects, aggregates, and correlates logs/events from various sources to detect security incidents. | Provides unified threat detection, investigation, and response across multiple security layers. |
| Core Functionality | Incident triage, playbook execution, automated threat containment, and cross-tool coordination. | Centralized log management, rule-based correlation, alerting, and compliance reporting. | Advanced threat detection with AI/ML, behavioral analytics, and integrated response actions. |
| Data Sources | Pulls from SIEM, threat intel feeds, EDR, firewalls, and other security tools. | Logs/events from network devices, servers, applications, security appliances. | Telemetry from endpoints, networks, email, cloud workloads, and security tools. |
| Automation Level | High – Automated responses reduce manual workload significantly. | Low to Moderate – Primarily manual investigation and response. | Moderate to High – Many responses can be automated, especially in integrated environments. |
| Threat Detection | Relies on integrated tools (like SIEM/XDR/EDR) for detection, focuses on response and orchestration. | Rule/signature-based, anomaly detection, correlation rules. | AI-driven, behavioral, and cross-domain correlation for advanced threats. |
| Response Capabilities | End-to-end incident resolution via automation: containment, remediation, and communication. | Minimal native response — alerts sent to analysts for action. | Integrated remediation actions across environments (e.g., isolate endpoint, block domain). |
| Integration Scope | Designed to connect with multiple security tools, ticketing systems, and workflows. | Integrates with log sources and alert pipelines. | Primarily integrates across vendor ecosystem and supported third-party tools. |
| Complexity | Requires upfront playbook creation and integration setup; powerful once configured. | Easier initial setup; complexity grows with more data sources and rules. | Simplified compared to managing SIEM + SOAR separately, but depends on vendor lock-in. |
| Compliance Role | Automates evidence collection and incident documentation. | Strong compliance reporting and audit support. | Supports compliance with integrated data retention and reporting. |
| Best For | Mature security teams needing faster, automated response and high alert volumes. | Organizations focused on log management, compliance, and visibility. | Companies wanting integrated detection and response without managing multiple platforms. |
| Limitations | Needs reliable detection sources; automation risks if playbooks are poorly designed. | Can generate alert fatigue; limited response automation. | Vendor lock-in, may lack flexibility of custom integrations. |
| Example Use Case | Phishing email reported → SOAR pulls data from SIEM, checks threat intel, blocks sender, and updates ticket automatically. | Server logs show repeated failed logins → SIEM alerts analyst for manual investigation. | Suspicious lateral movement → XDR correlates endpoint, network, and email activity → quarantines endpoint and blocks attacker’s IP. |
Conclusion
The power of SOAR comes from how it turns a messy alert to response flow into a smart and super-fast security process.
Whether it’s phishing detection to insider threat management, every SOAR use case shows how automation in SOC cuts down response time and lowers human mistakes. This gives security teams more space to focus on strategy and building stronger defenses.
At ESDS Software Solution Limited, SOAR is built into your security setup with ease. With our automation SOC expertise, strong threat intelligence, and proven experience in BFSI, Government, and large enterprises, we make sure you’re always ahead of cyber risks.
