Data Center Security: Core Concepts and Market Trends
Understanding Data Center Security
The concept of Data Center security discusses the practices, policies, security measures along with technologies that are used for ensuring physical and virtual protection of any Data Center facility. Data Centers need to be safeguarded against all forms of insider and outsider threats besides other forms of prominent forms of cybercrimes. They constantly pose threats to a Data Centre’s security infrastructure.
The following are some basic yet commonly used considerations for deciding the effectiveness of a Data Center-
- Physical security of the Data Center infrastructure
- Managing and controlling user access
- Defining security procedures and protocols
The considerations mentioned above might be complex in nature, made of different elements used to define individual Data Center components’ effectiveness. The absence of a multi-layered security environment at a Data Center may compromise the Data Center infrastructure against all forms of persistent threats.
Why is Data Center Security Needed?
Data Center Security is important for any organization that stores critical and vital user information within Data Centers. A robust Data Center security infrastructure ensures hackers and other cybercriminals are kept away from the central repository. A Data Center security solution can be achieved either through Data Centers or a partner.
The absence of Data Center security can possibly invite the following attacks-
- Scanning/Probing- In this form of a Data Center attack, a request is given to multiple port addresses present on an active port with the intent to create damage using the weakness present in the service port.
- Denial of Service (DoS) Attacks-Denial of Service attacks occurs when the system owners are restricted from accessing their network and other critical system resources, resulting in a hostile threat-like situation.
- Distributed Denial of Service (DDoS) Attacks- This attack takes place on several systems present in the network, leaving the entire network open to cyber risks.
Access Controls in Data Centers
There are three significant reasons why an access control mechanism is indispensable in any Data Center infrastructure. These reasons include-
- Physical Security- A Data Center’s physical security is clearly guaranteed when selecting the Data Center access controls. The Data Center providers don’t want unrestricted members to access the floor. The physical security of Data Center becomes an ultimate security measure when it combines with the compatibility and compliance of Data Centers.
- Compatibility- In terms of compatibility, using a Cloud-based Access Control mechanism allows the Data Center providers to integrate the existing IT infrastructure with all the physical components present in the Data Center. Cloud-based access control can be combined with intrusion detection alerts, multi-factor authentication, and other enhanced security measures. Usually, the legacy access control systems can be highly ineffective as they don’t assure any form of compatibility.
- Compliances-To ensure the complete security of a Data Center, it is a must that the Data Center provider follows certain protocols required for implementing a system and legal compliances within the Data Centers.
Implementing Physical Security Policy in Data Centers
A Data Center provider needs to ensure that the physical security solutions are accompanied by a detailed physical security policy of a Data Center. Such policies ensure that accessing sensitive information is asked to follow a well-defined operating procedure to mitigate any form of risks like data breaches, cyberattacks, or even damage to the hardware.
Ensuring Digital Security in Data Centers
Intrusion detection and threat prevention mechanisms can notify the system administrators about any form of advanced persistent cyberthreat. The advanced persistent cyber threats are usually performed by hackers, with the clear intent of collecting users’ critical information. Detection of advanced persistent threats within a Data Center demands continuous & real-time monitoring. The network and system log files must be constantly scanned and report an alert in case of any unusual events.
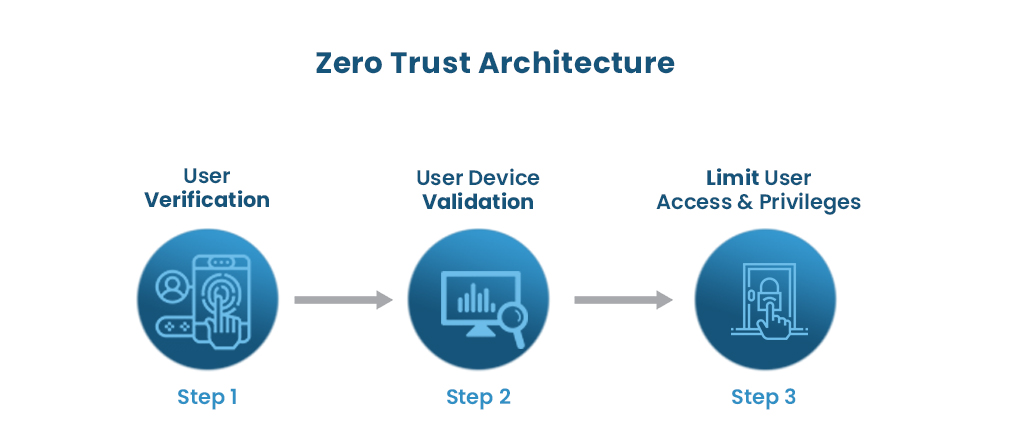
Zero Trust Architecture
Zero Trust Architecture or Zero Trust depicts security concepts and threat model that doesn’t need the assumption that actors, security systems and services functioning within the security perimeter should be trusted. Instead, anything and everything that is being connected to the systems needs to be verified. The Zero Trust architecture has been designed to restrict all forms of security breaches that can hamper Data Centers’ working.
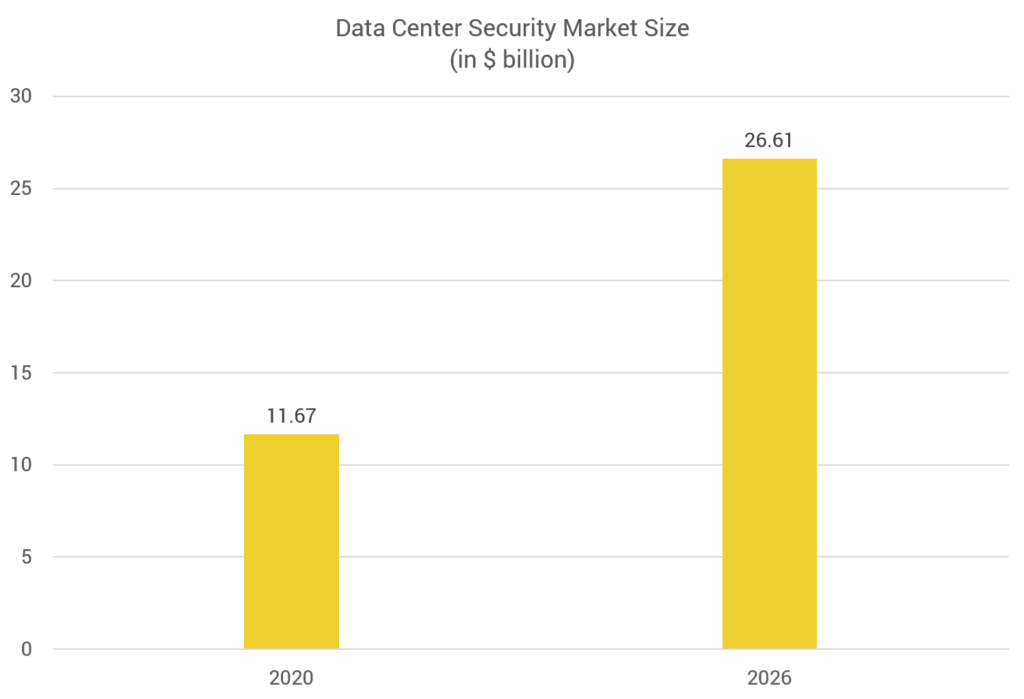
Global Data Center Security Market
As per an online published report, the global Data Center Security Market was valued at $11.67 billion in 2020 and is forecasted to reach $26.61 billion by 2026. During the forecasted period, i.e., 2020-2026, this market is expected to witness a growth CAGR of 14.91%.
Global Data Center Security Market Size
Market Growth Drivers
The growth of this market segment can be attributed to the following reasons-
- The increasing data traffic emerging from a large number of devices is driving the growth of Data Centers. To ensure secure connectivity of user-critical data and confidential information also demands localized (within geographic boundaries of a country) Data Centers.
- A tech company estimates that there has been a significant growth registered in the global Cloud Data Center traffic, rising from 6.0 ZB (in 2016) to 20.6 ZB (in 2021).
- There has been significant growth in the overall number of cyberattacks and data breaches, causing substantial monetary and non-monetary losses to business organizations. This has created an increased demand for data localization, focusing on hosting user data within the Data Center provider’s same geographic boundaries.
Wrapping Up
The security of the Data Center must be considered seriously. Most organizations today are now migrating their critical applications and data to a Cloud Computing infrastructure. This migration to Cloud infrastructure from the traditional, legacy systems can make the Data Centers a soft target for cyberattackers.
Business organizations must carefully compare their real practices against the defined best practices and accordingly make adjustments to ensure complete Data Center security. For any enterprise, a breach in their Data Center is no less than a nightmare, and this is where Data Center providers like ESDS complete security of the data hosted across its Data Center locations. ESDS deploys a 7-layer Security Infrastructure for ensuring advanced, and best-in-class Managed Security.
- Considering Data Centers in India to Overcome Economic Conditions - May 10, 2022
- Determining Why Your Organization Needs Web Application Security - February 11, 2022
- How Does a Business Benefit with Managed Services - January 21, 2022