WANNACRY PETYA RANSOMWARE: ACT FAST, BEFORE IT’S TOO LATE!
Ransom:Win32/Petya.A-joey / Ransom:Win32/Petya
Alert level: Severe

Ransomware? WannaCry? Petya? What are these words? No dictionary mentions them or there wasn’t any bubble about them till last year, yet nowadays they tend to be the most powerful searched & feared terms! Searched by novices & Feared by the unfortunate affected victims!
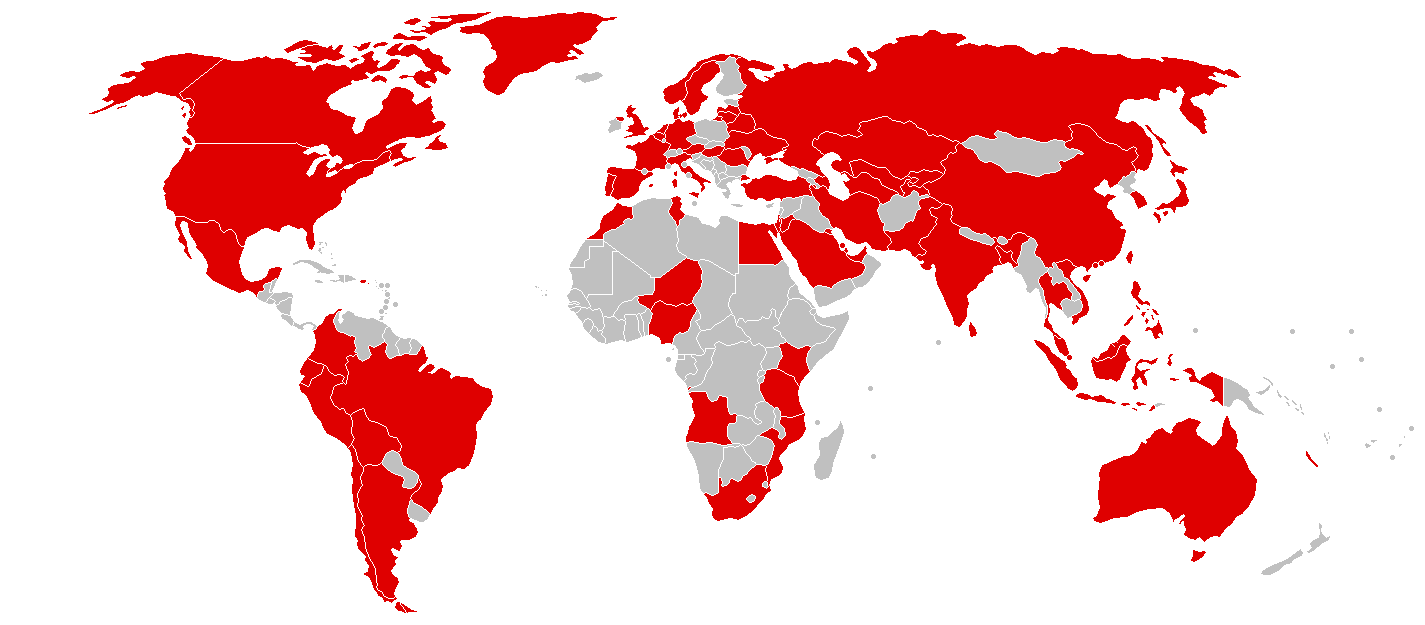
Starting the second week of May 2017, the entire world went into PANIC-MODE, one of the biggest cyber-attacks which spread globally in more than 150 countries affecting millions of computer systems due to a vulnerability in the SMB/CIFS protocol on Windows operating systems. Widely known as the WannaCry ransomware attack, it crippled multiple National Health Service trust centers in the United Kingdom, hundreds of computers at the Russian Interior Ministry, & many university networks in China. While security analysts from various organizations & governments are still struggling to recover from this “WannaCry” catastrophe, another ransomware bomb named “Petya” has been set off.

These kinds of attacks (popularly known as ransomware attack) encrypt the files of target system making them inaccessible to the user before demanding payment in return for decrypting those files. The user either ends up paying the ransom demanded or loses his data (by reinstalling the OS). Petya is also from the same family of encrypting ransomware that was first discovered in 2016 but on a very small scale. Petya propagates via infected email attachments. The malware also targets Microsoft Windows-based systems but infecting the master boot record to execute a payload that encrypts the NTFS file table, demanding a payment in bitcoin in order to regain access to the system. A new variant of Petya, dubbed as NotPetya because it masquerades as the Petya ransomware, uses a modified version of the NSA’s stolen & leaked EternalBlue SMB exploit similar to that of WannaCry.
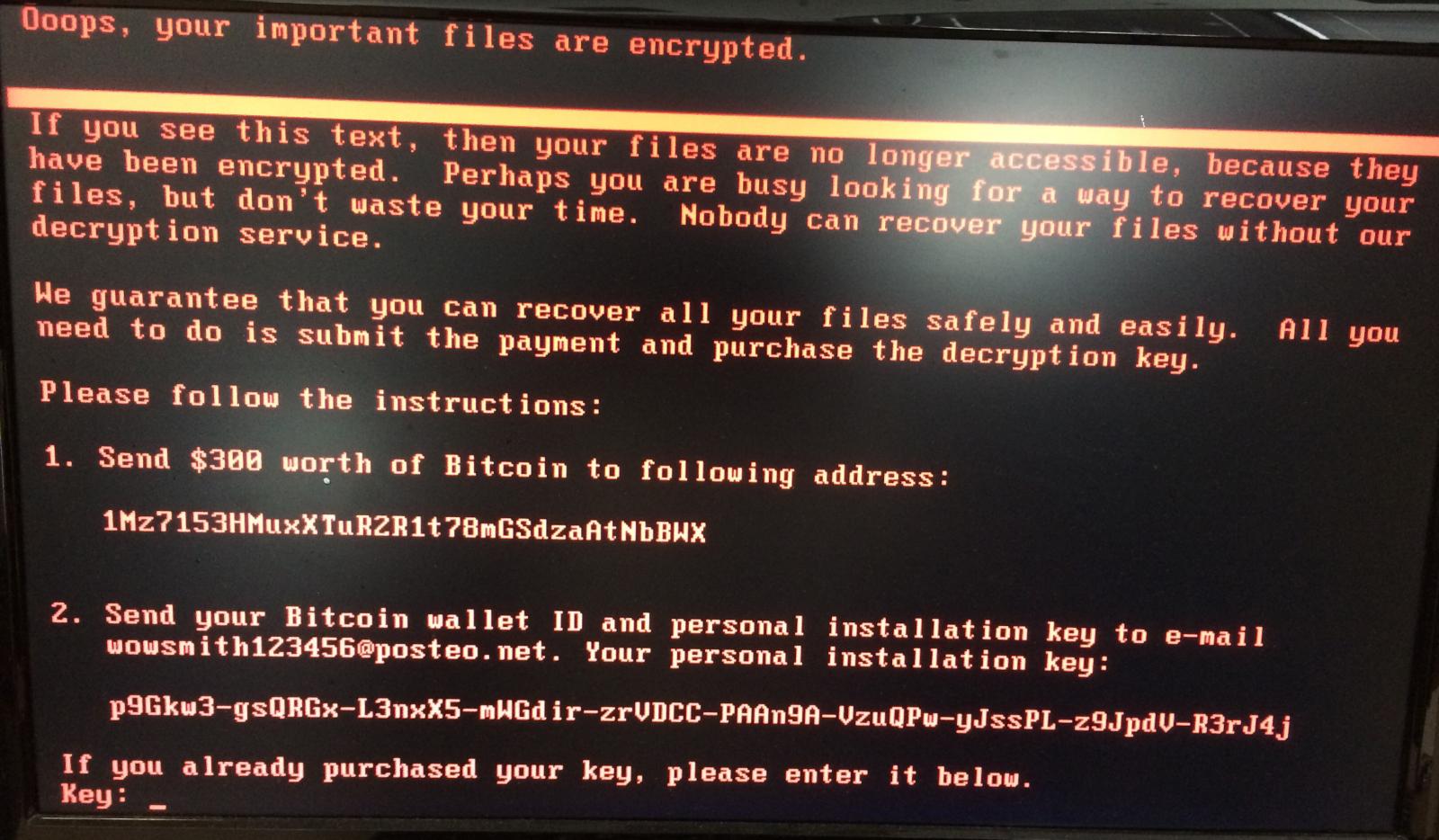
Petya doesn’t encrypt files on a targeted system one by one, as in other ransomware, it reboots victim’s computers & encrypts the hard drive’s master file table (MFT) & making the master boot record (MBR) inoperable by denying access to the full system by attacking low-level structures on the disk (restricting access file names, sizes, & location on the physical disk). Petya replaces the computer’s MBR with its own malicious code that displays the ransom note & leaves computers unable to boot the OS. This ransomware’s authors have not only created their own boot loader but also a tiny kernel, which is 32 sectors long. Now when the affected system’s master boot record (MBR) is overwritten by the custom boot loader that loads a tiny malicious kernel, then, this kernel proceeds with further encryption. Petya’s ransom note states that it encrypts the full disk, but this is not true. Instead, it encrypts the master file table (MFT) so that the file system is not readable. If it fails to encrypt the MFT, then the OS boots normally &
This ransomware have two infection stages, the first is executed by the dropper (Windows executable file, delivered via scam emails themed as a job application. E-mail comes with a Dropbox link, where the malicious ZIP is hosted). It overwrites the beginning of the disk (including MBR) & makes an XOR encrypted backup of the original data. This stage ends with an intentional execution of BSOD (& a reboot post it). Saving data at this point is relatively easy, because only the beginning of the attacked disk is overwritten. The file system is not destroyed, & we can still mount this disk & use its content. That’s why, if you suspect that you have this ransomware, the first thing we recommend is to not reboot the system. Instead, make a disk dump. Eventually you can, at this stage, mount this disk to another operating system & make the file backup. See also: Petya key decoder. The second stage is executed by the fake CHKDSK scan. After this, the file system is destroyed & cannot be read. Like WannaCry, Petya is also exploiting SMBv1 EternalBlue exploit & taking advantage of unpatched Windows machines.
The group behind all this trouble, The Shadow Brokers (TSB), is a hacker group who first appeared in 2016 publishing several leaks containing some of the National Security Agency (NSA)’s hacking tools, including several zero-day exploits. Specifically, these exploits & vulnerabilities targeted enterprise firewalls, anti-virus products, & Microsoft products. This leak of NSA’s exploits leads to a potential weapon of emails with MS17-010 the SMBv1 vulnerability exploitation along with the explosion of WannaCry & Petya like Ransomware. Havoc wrecked all over Europe & several entities are reporting ransomware infections & destruction of data. Tens of hundreds of computers at private companies are also affected including German rail operator Deutsche Bahn, international shipper FedEx Corp, car manufacturers Renault & Nissan, & Spanish telecommunications company Telefonica, to name a few. Global automaker Honda had to shut down its manufacturing plant for a day owing to the ransomware infection.
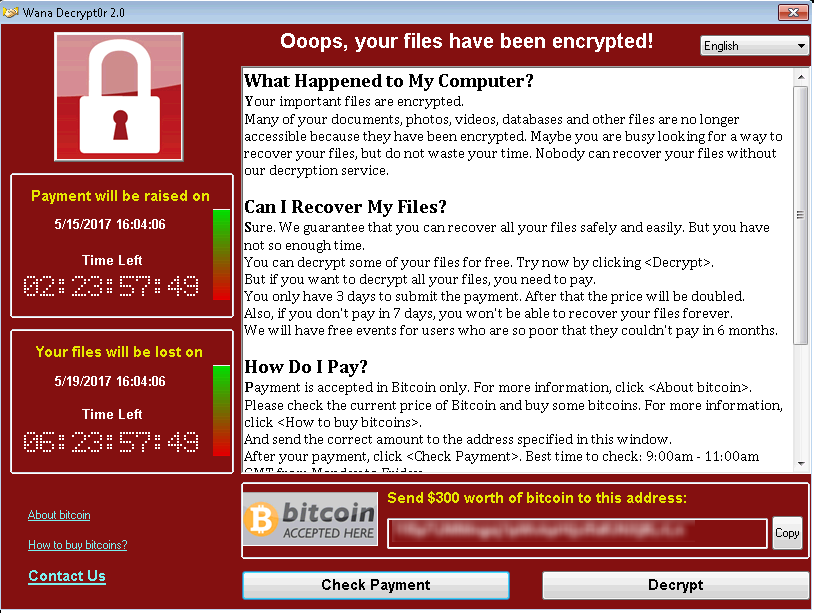
Although the attack had slowed down by May end, WannaCry’s creators continued to ask for ransom for decrypting the encrypted data. The attack is still in progress & we suspect that it will continue to affect businesses across the world in the coming days. It is still possible that many companies haven’t noticed the attack yet but should be careful enough to avoid getting attacked & their data held for ransom. This malware primarily targets PCs & laptops that still use Windows XP, more recent Microsoft systems, including Windows 8 & 7, can also be infected. There hasn’t been any reported exploitation in Windows 10 yet. Once a user clicks on unsuspecting links or email attachments, WannaCry downloads itself on the system & uses strong, asymmetric encryption, employing the RSA 2048-bit cipher to encrypt all the files. Whereas, Petya reboots victim’s computers & encrypts the hard drive’s master file table (MFT) & rendering the master boot record (MBR) inoperable, restricting access to the full system by seizing information about file names, sizes, & location on the physical disk. Petya replaces the computer’s MBR with its own malicious code that displays the ransom note & leaves computers unable to boot.
Security Patch: No business would want critical documents locked out of reach; until the ransom is paid. If any of your systems are still using Windows XP, upgrade it to a more recent operating system on priority. For other Windows operating system versions, install this security patch by Microsoft.
Issue Internal Warning: Microsoft has advised users to avoid downloading random attachments & click on links from email senders they do not recognize. You should send out a warning email to all the employees about it.
In order to prevent infection users & organizations are advised to apply patches to Windows systems as mentioned in Microsoft Security Bulletin MS17-010 Microsoft Patch for Unsupported Versions such as Windows XP, Vista, Server 2003, Server 2008 etc. http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598
To prevent data loss Users & Organizations are advised to take backup of Critical Data
Block SMB ports on Enterprise Edge/perimeter network devices [UDP 137, 138 & TCP 139, 445] or Disable SMBv1. https://support.microsoft.com/en-us/help/2696547
Apply following signatures/rules at IDS/IPS:
alert tcp $HOME_NET 445 -> any any (msg:"ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response"; flow:from_server,established; content:"|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|"; depth:16; fast_pattern; content:"|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|"; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:2;)
alert smb any any -> $HOME_NET any (msg:"ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Request (set)"; flow:to_server,established; content:"|00 00 00 31 ff|SMB|2b 00 00 00 00 18 07 c0|"; depth:16; fas
t_pattern; content:"|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|"; distance:0; flowbits:set,ETPRO.ETERNALBLUE; flowbits:noalert; classtype:trojan-activity; sid:2024220; rev:1;)
alert smb $HOME_NET any -> any any (msg:"ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response"; flow:from_server,established; content:"|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|"; depth:16; fast_pattern; content:"|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|"; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:1;)
Best practices to prevent ransomware attacks:
1) Perform regular backups of all critical information to limit the impact of data or system loss & to help expedite the recovery process. Ideally, this data should be kept on a separate device, & backups should be stored offline.
2) Establish a Sender Policy Framework (SPF), Domain Message Authentication Reporting & Conformance (DMARC), & DomainKeys Identified Mail (DKIM) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
3) Don’t open attachments in unsolicited e-mails, even if they come from people in your contact list, & never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail & go to the organization’s website directly through the browser.
4) Restrict execution of PowerShell /WSCRIPT in the enterprise environment. Ensure installation & use of the latest version (currently v5.0) of PowerShell, with enhanced logging, enabled, script block logging, & transcription enabled. Send the associated logs to a centralized log repository for monitoring & analysis.
5) Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA%, %PROGRAMDATA% & %TEMP% paths. Ransomware sample drops & executes generally from these locations. Enforce application whitelisting on all endpoint workstations.
6) Deploy web & email filters on the network. Configure these devices to scan for known bad domains, sources, & addresses; block these before receiving & downloading messages. Scan all emails, attachments, & downloads both on the host & at the mail gateway with a reputable antivirus solution.
7) Disable macros in Microsoft Office products. Some Office products allow for the disabling of macros that originate from outside of an organization & can provide a hybrid approach when the organization depends on the legitimate use of macros. For Windows, specific settings can block macros originating from the Internet from running.
8) Configure access controls including file, directory, & network share permissions with least privilege in mind. If a user only needs to read specific files, they should not have write access to those files, directories, or shares. Maintain updated Antivirus software on all systems.
9) Consider installing Enhanced Mitigation Experience Toolkit, or similar host-level anti-exploitation tools. Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf. Regularly check the contents of backup files of databases for any unauthorized encrypted contents of data records or external elements, (backdoors /malicious scripts.)
10) Keep the operating system third party applications (MS Office, browsers, browser Plugins) up-to-date with the latest patches.
11) Follow safe practices when browsing the web. Ensure the web browsers are secured enough with appropriate content controls.
12) Network segmentation & segregation into security zones – help protect sensitive information & critical services. Separate administrative network from business processes with physical controls & Virtual Local Area Networks. Disable remote Desktop Connections, employ least-privileged accounts.
13) Ensure integrity of the codes /scripts being used in database, authentication & sensitive systems, check regularly for the integrity of the information stored in the databases.
- Restrict users’ abilities (permissions) to install & run unwanted software applications.
- Enable personal firewalls on workstations.
- Implement strict External Device (USB drive) usage policy.
- Employ data-at-rest & data-in-transit encryption.
- Carry out Vulnerability Assessment & Penetration Testing (VAPT) & information security audit of critical networks/systems, especially database servers from CERT-IN empaneled auditors. Repeat audits at regular intervals.
- Individuals or organizations are not encouraged to pay the ransom, as this does not guarantee files will be released. Report such instances of fraud to CERT-In & Law Enforcement agencies.

- WANNACRY PETYA RANSOMWARE: ACT FAST, BEFORE IT’S TOO LATE! - June 28, 2017
- “D” for Demonetization! - January 5, 2017
- 2017 – The Year of the Internet of Things - September 1, 2016
Thanks for letting us know troypoint mobdro
Thanks for sharing such a wonderful post..
Thanks…
right information from this blog about SAP user list
Thank You…