Is Your Business Prepared for Cyber Attacks During National Crises?

Cyberattacks have become a favored weapon for state-sponsored actors in a world where geopolitical tensions escalate quickly. These cyberattacks can shatter critical infrastructure, disrupt economies, and breach sensitive information. As individuals and companies become more dependent on digital platforms, the question is: Are you and your business prepared to resist cyberattacks during national crises? This article shows the methods of cyber-attack prevention in this ongoing critical situation.
Why is cloud security critical during national crises?
Organizations face increased cyber-attacks that target vital infrastructure and digital assets during national emergencies like pandemics, natural disasters, or geopolitical conflicts. Cloud systems, essential to modern operations, become extremely vulnerable at this point. Protecting sensitive data and maintaining business continuity depend heavily on cloud security.
Businesses can secure their data even during disruptions to traditional operations by implementing strong encryption, access controls, and threat detection methods. Additionally, cloud solutions provide remote access and scalability, facilitating easy collaboration and data availability in an emergency. At a time when stability is most important, companies without robust cloud security procedures face the risk of data breaches, financial loss, and reputational damage.
Real-world cyberattacks amid geopolitical tensions
State-sponsored cyberattacks have increased over the past few years, usually coinciding with geopolitical conflicts. Some examples include:
Ukraine-Russia Conflict: In December 2015, a cyberattack by the Russian group “Sandworm” knocked Ukraine’s power grid offline, leaving about 230,000 individuals in the dark without electricity. Later, in June 2017, initially targeted Ukraine, the NotPetya cyberattack got out of hand, hitting more than 60 countries. Global giant Maersk was among the hardest hit, losing 49,000 laptops and all print capabilities in a few hours.
- Iran-U.S. Tensions: During rising tensions, Iranian hackers have been linked to campaigns of defacement and data destruction attacks against U.S. infrastructure in an attempt to create chaos and distrust.
- India-China Border Disputes: After clashes at the borders, Indian officials claimed a spike in phishing and DDoS attacks on public sector websites suspected to be mounted by Chinese state-sponsored groups.
These cases highlight the strategic employment of cyber warfare to destabilize enemies without traditional military confrontation.
The surge of cyberattacks during crises
Cyberattacks offer nations a means to project power and influence without confrontation. During conflicts, these attacks often aim for:
- Disrupting critical infrastructure: Targeting power grids, communication networks, and financial systems to create widespread disruption.
- Stealing sensitive information: Exfiltrating classified data to gain strategic advantages.
- Spreading misinformation: Undermining public trust through propaganda and fake news campaigns.
Cyber operations are appealing tools for states to achieve objectives without overt aggression because of their deniability and anonymity.
The role of national cybersecurity initiatives for Indian enterprises
India’s national cybersecurity initiatives provide a strategic backbone for enterprises functioning in an increasingly digital and threat-prone environment. To improve the digital security of businesses, government organizations such as the National Critical Information Infrastructure Protection Centre (NCIIPC) and the Indian Computer Emergency Response Team (CERT-In) offer incident response procedures, advisories, and frameworks.
Programs such as “Cyber Surakshit Bharat” aim to educate leaders and IT professionals on best practices in cybersecurity. These initiatives support compliance with national policies, such as the Digital India mission, promote collaboration between the public and private sectors, and make it easier to share cyber intelligence. In addition to ensuring compliance, Indian businesses that support these measures greatly improve their security posture against advanced attacks and support the country’s cyber defense.
A civilian’s responsibility for taking cyber attack prevention
In the volatile global scenario today, while the Indian Army guards our borders, working day and night to keep the nation secure, civilians should be aware that not all threats are physical or tangible. Remaining away from the field doesn’t necessarily mean we’re safe. Cyberattacks do not require physical boundaries to breach. These attacks target loopholes in systems and individuals. A misplaced click, an old system, or a weak password can open up sensitive information, potentially crippling entire networks and impacting millions. One compromised breach can create a domino effect on national security. This is the moment to remain vigilant, take control, and arm ourselves with the proper knowledge and tools for cyber attack prevention.
Cybersecurity best practices for every civilian

- Use strong, unique passwords for each platform. Use not-too-obvious combinations, and never reuse a password.
- Turn on two-factor authentication (2FA) to provide an additional layer of protection to your accounts.
- Watch out for suspicious links and attachments in emails, messages, and websites, even if they look like they come from familiar contacts.
- Keep your software, operating systems, and apps up to date to close known vulnerabilities.
- Regularly back up data on secure cloud platforms or external drives to prevent ransomware.
- Avoid financial transactions over public Wi-Fi; establish a secure VPN connection instead.
- Be aware of prevalent cyber threats like phishing, smishing, and malware.
- Install reliable antivirus and anti-malware software across all personal and business devices to ensure cyber-attack prevention.
- Limit sharing of personal data online, and most especially on social media platforms.
- Participate in cybersecurity awareness programs whenever possible—knowledge is your first line of defence.
How businesses can ensure cyber-attack prevention
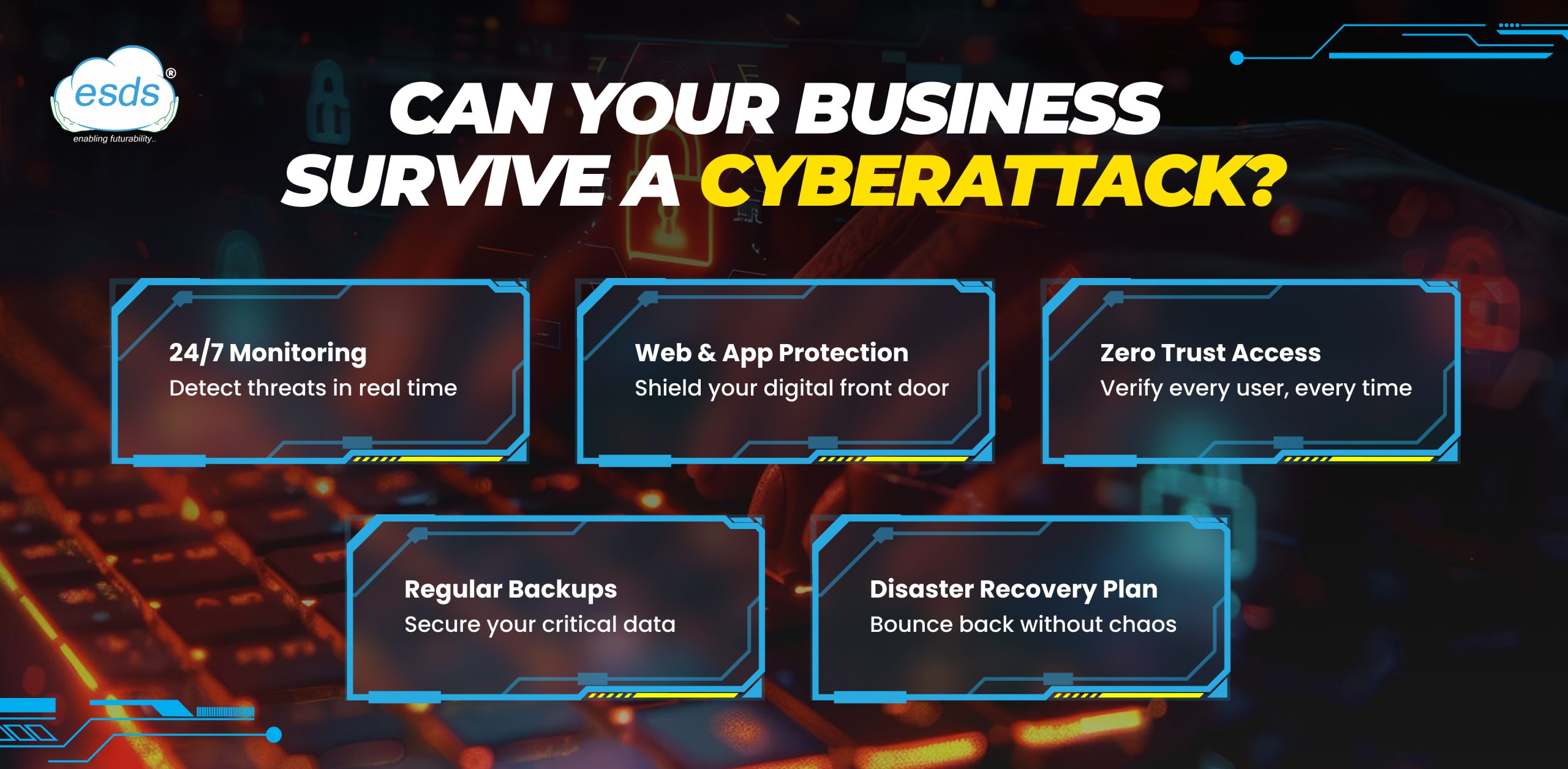
For cyber-attack prevention, businesses should invest in robust cybersecurity measures:
- Security operations center (SOC) is a centralized unit that monitors, detects, and responds to real-time cybersecurity incidents.
- Web application firewalls (WAFs)protect web applications bsy filtering and monitoring HTTP traffic, defending against common attacks like SQL injection and cross-site scripting.
- Virtual private networks (VPNs)secure remote access by encrypting data transmissions, essential for organizations with distributed workforces.
- Disaster recovery and data backup enhance business continuity by regularly backing up data and having a recovery plan to restore operations swiftly after an incident.
Implementing these tools creates a multi-layered defense strategy, reducing the possibilities and impact of cyber incidents and enhancing cyber-attack prevention.
Cloud security amid uncertainties
As cloud computing grows increasingly common, protecting these settings is crucial for cyber-attack prevention:
Private cloud: To protect sensitive data, stringent access controls are put in place, and frequent audits are conducted.
Public cloud: Use the security features that providers have installed, like identity management software and encryption.
Hybrid cloud: To avoid configuration drift, use unified management systems to guarantee uniform security policies across on-premises and cloud platforms.
Regular system updates, vulnerability monitoring, and staff training on security best practices are essential elements of cloud security.
Adopting zero trust architecture for cloud workloads
The Zero Trust model operates on the principle of “never trust, always verify,” requiring continuous authentication and validation of users and devices. Key benefits include:
- Increased security: Restricting access to resources through rigorous verification minimizes the chances of unauthorized access.
- Reduced attack surface: Network micro-segmentation eliminates lateral movement for attackers.
- Increased compliance: Complies with regulation requirements by imposing strict access controls and monitoring.
Implementing Zero Trust architecture fortifies security, especially in complicated cloud environments.
Why emphasize BFSI and government segments?
Banking, Financial Services, Insurance (BFSI) and government organizations are the prime targets for cyberattacks because they possess sensitive information. Protective measures include:
Multi-Factor Authentication (MFA): Provides an additional layer of security in addition to passwords.
Regular security audits: Detect and fix vulnerabilities promptly through cloud security audits.
Employee training: Train employees to identify phishing attempts and adhere to security protocols.
Investing in these cloud security measures protects critical infrastructure from emerging cyber threats.
Achieving multi-cloud visibility and active threat monitoring
As companies embrace multi-cloud strategies, visibility and monitoring across platforms are critical:
- Unified security platforms: Implement solutions with a centralized view of cloud security activity across all services.
- Continuous monitoring: Install tools that identify anomalies and potential threats in real-time.
- Automated response mechanisms: Use automation to respond quickly to incidents, minimizing response times and damage.
These cyber-attack prevention practices ensure that security teams can detect and address threats promptly, regardless of where they originate.
Conclusion
In an increasingly volatile global landscape, cyber-attack prevention is not optional but necessary. By learning about the dynamics of cyber threats in times of national crisis and adopting robust physical and cloud security practices, enterprises can safeguard their assets, keep customers’ trust, and preserve business continuity. Proactive investment in cybersecurity is necessary for organizations aiming to thrive in the digital age.
Disclaimer
“ESDS Software Solution Limited is proposing, subject to receipt of requisite approvals, market conditions and other considerations, to make an initial public offer of its equity shares and has filed a draft red herring prospectus (“DRHP”) with the Securities and Exchange Board of India (“SEBI”) that is available on the website of the Company at https://www.esds.co.in/, the website of SEBI at www.sebi.gov.in as well as on the websites of the book running lead managers, DAM Capital Advisors Limited at https://www.damcapital.in/ and Systematix Corporate Services Limited at http://www.systematixgroup.in/ The website of the National Stock Exchange of India Limited at www.nseindia.com and the website of the BSE Limited at www.bseindia.com, respectively. Investors should note that investment in equity shares involves a high degree of risk. For details, potential investors should refer to the RHP which may be filed with the Registrar of Companies, Maharashtra at Mumbai, in future including the section titled “Risk Factors”. Potential investors should not rely on the DRHP filed with SEBI in making any investment decision.”
- Achieving Secure, Reliable Compliance with India’s Data Sovereignty Mandates - November 17, 2025
- Implementing GPU workloads in critical government application - November 12, 2025
- Why Data Sovereignty Is Important for Indian Enterprises - August 22, 2025
