How to Secure Cloud and On-Prem Environments with Unified Defense

In today’s rapidly changing digital landscape, organizations are increasingly moving towards hybrid IT environments, which offer the best of both worlds— secure cloud and on-premise infrastructure. The ease of scalability and flexibility make this an attractive solution; however, it presents new security challenges, specifically data and systems protection across these disparate environments. A unified security strategy is key to overcoming those problems.
Understanding unified security for hybrid IT
This strategic amalgamation pools security management across secure cloud and on-premise environments. Consistency is achieved in monitoring, policy enforcement, threat detection, and compliance. Without unity, organizations risk creating unnecessary blind spots, policy inconsistencies, and increased vulnerabilities due to fragmented security practices.
Critical components of unified security
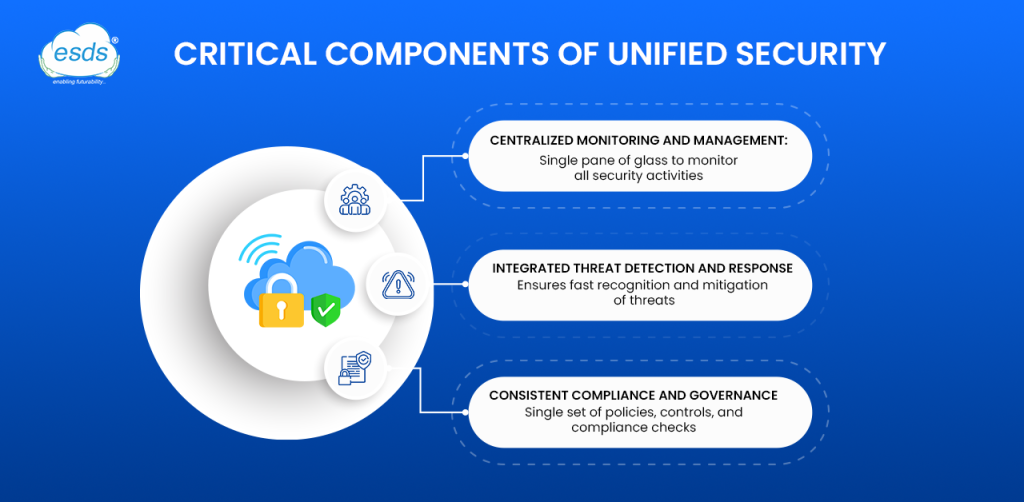
Centralized monitoring and management
Unified cloud data security solutions provide a single pane of glass to monitor all security activities across cloud and on-premise environments. Such central monitoring helps identify potential threats, anomalous behavior, and policy violations in real time, lowering response times.
Integrated threat detection and response
Threats detected by the cloud and those detected by the on-premise infrastructures are treated differently, security coverage becomes fragmented, and threats are likely to fall into gaps. Consolidation allows detection and response capabilities to offer an integrated solution so that fast recognition and mitigation of threats, irrespective of their source, are guaranteed.
Consistent compliance and governance
Unified security enables a single set of policies, controls, and compliance checks across IT environments. This minimizes non-compliance risk and ensures adherence to industry regulations and standards.
How to implement unified security
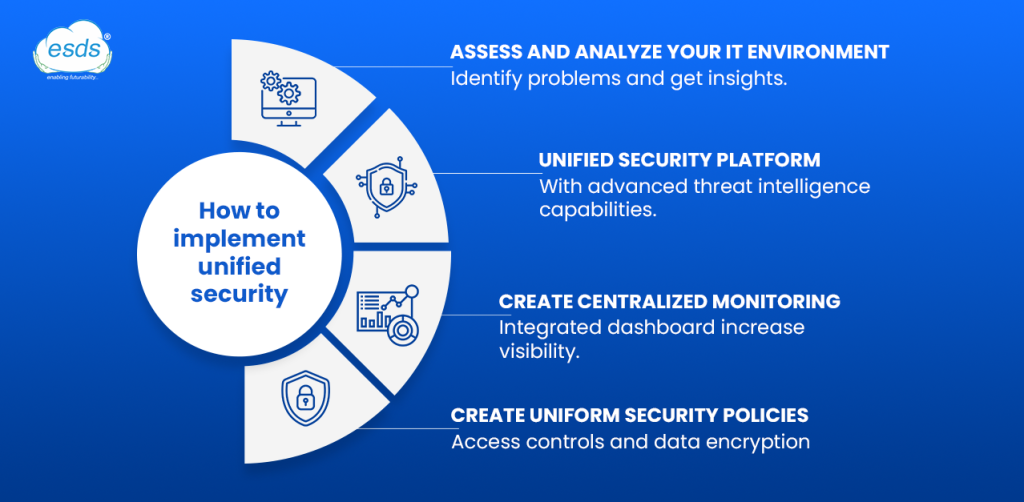
Assess and analyze your IT environment.
First, you should conduct a detailed evaluation of the infrastructure currently available. Find out all the different types of cloud and on-prem assets and the general state of security services. An audit like this will point to where the problems lie and give insight into areas that might require consolidation.
Unified security platform
Implement an integrated security platform that can quickly unite your cloud and on-premise security operations. Such a platform should ensure advanced threat intelligence capabilities, central activity monitoring, and automation in security incident response.
Create centralized monitoring
Install an integrated dashboard for monitoring security activity across all environments. Centralized monitoring will increase visibility so your team can virtually instantaneously see and address threats, regardless of the environment.
Create uniform security policies.
Create consistent security policies across the cloud and on-premises. This includes equal enforcement of controls for access, data encryption, and incident response, so policy inconsistency is less likely to open up wide security gaps or misconfigurations.
Advantages of consolidated security
· Improved visibility
Consolidated security provides a 360-degree view of your overall IT landscape, thus enabling the easy detection and minimization of threats.
· Efficient compliance
Consistent policies and monitoring centralization make compliance with regulatory requirements much easier and less resource-intensive.
· Improved efficiency
Consolidated security reduces the complexity of operations and ensures centralized management of all security activities from a single platform, saving valuable time and minimizing the process.
ESDS unified security solutions
ESDS offers advanced, integrated security solutions that protect cloud and on-premise infrastructures. Our security services include 24/7 monitoring through a dedicated SOC, advanced threat intelligence, and compliance management. Our security solution’s integrated approach will grant companies high visibility, accelerated threat detection, and streamlined security operations.
Wrapping up with a unified future for hybrid IT security
Building a monitoring infrastructure is not easy and requires managing complex multi-cloud environments. Still, getting an overall view of what is happening within your organization has never been more essential. A structured approach can help you handle this complexity and achieve your desired results.
It doesn’t stop with this alone. New software, new attacks, and new vulnerabilities spring up every single day, and all these would expand the organization’s attack surfaces. It needs continuous development. Assess threats all the time, create newer use cases, and update more rules to SIEM, SOAR, or equivalent systems in an organization. A business entity can see the steady augmentation of the security posture here.
One unified security strategy becomes critical as an organization adapts to the logic of hybrid IT models. Once integrated into a single platform, it can achieve robust protection and ensure compliance while working much more efficiently than when the cloud and on-premise security measures are treated separately. It is about security and preparing organizations for an impending landscape of evolving threats.
Let’s harden your hybrid IT infrastructure. Contact ESDS today to learn more about our unified security solutions.
- When Was the Last Time You Tested Your DR Plan? - May 29, 2025
- Is Your Business Prepared for Cyber Attacks During National Crises? - May 23, 2025
- SaaS Is Transforming the Way Companies Scale - April 28, 2025
