5 Reasons to Protect Your Business Beyond Endpoints
When it comes to data security, the endpoint channel is undoubtedly one of the most crucial components. It is the location where end users create, edit and store data. Endpoints such as laptops, and desktops are often the primary points of access to sensitive data held by an organization and can be vulnerable to a wide range of security threats.
Your users perform nearly all of their hybrid/remote work on endpoints, including reading emails and creating files on endpoints. The endpoint touches multiple channels, including web traffic, cloud applications, web applications, and the network, but does it record everything?
In the past, it might have been sufficient to protect only the endpoint channel. For the organisations of today, though, that is not the case. Here are 5 reasons why concentrating your data security efforts solely on the endpoint actually limits your capacity to stop data breaches and guarantee compliance with regulations:
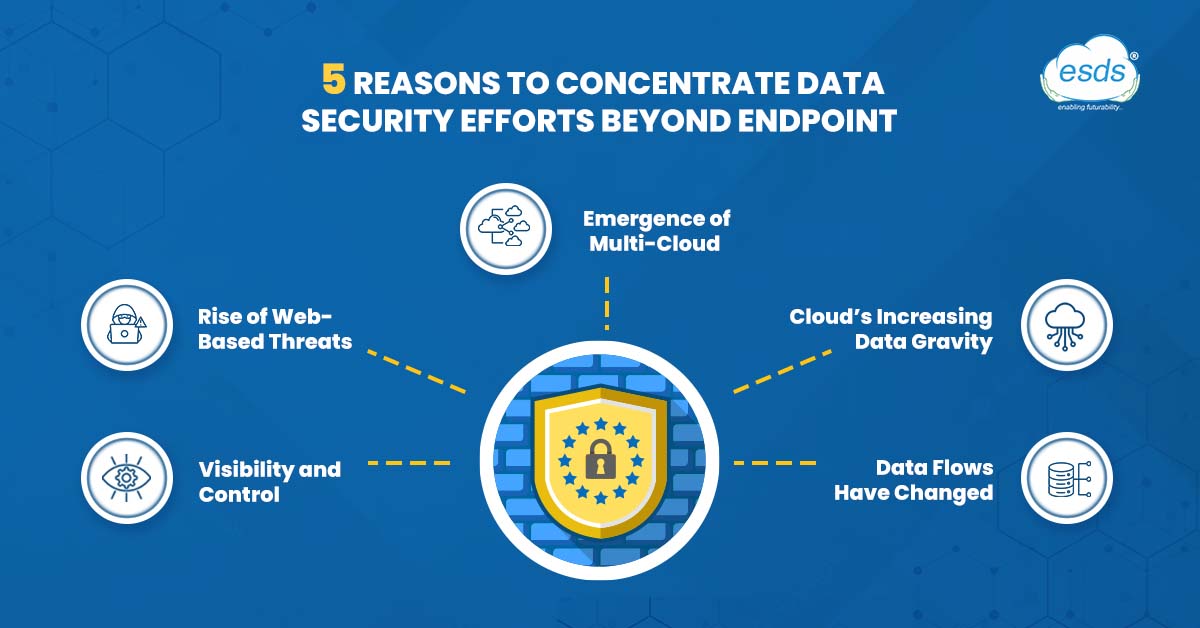
- First, data flows have changed.
Since it is an addition to existing data flows, they are not being completely replaced. As long as your users are using laptops and desktop computers (and increasingly BYOD devices), and as long as digital transformation is ongoing, the amount of data flowing to and from endpoints will increase at an astounding rate. Additionally, the prevalence of distributed environments is encouraging an increase in the movement of sensitive data among numerous locations, frequently without ever passing through a managed endpoint.
- Second, the cloud’s increasing “data gravity”.
According to projections, the market for cloud storage is expected to experience a compound annual growth rate of 24.8% until 2030. One of the primary reasons for this shift in data flow is the concept of “data gravity,” which describes the tendency of large data sets to attract smaller datasets, as well as related services and applications. As a result, numerous applications and services have been drawn into the cloud due to the vast amount of data stored there. This means that data flows between these applications and services can remain within the cloud, without ever needing to cross an endpoint.
- Third, the emergence of multi-cloud environments
Some of the major public cloud vendors would have you believe that the only data you need to worry about securing is on their particular platform. They encourage customers to choose a primary public cloud and stick with the ecosystem of applications and services it provides. However, the reality of the cloud world is far more complex. Most companies today store their data in multiple clouds, ranging from large public clouds to smaller SaaS solutions. As a result, cloud locations and applications continue to proliferate, and the trend towards multi-cloud environments shows no signs of slowing down. Consolidating all data into a single public cloud or ecosystem is not a feasible solution for most companies.
- Fourth, the rise of web-based threats
In today’s digital landscape, many applications operate through web-based interfaces, and their numbers have grown exponentially in recent years. As a result, data flows across the web, posing significant concerns for security professionals. Malicious websites continue to proliferate. It becomes crucial for companies to be able to block them, scan downloads for viruses, and inspect web traffic for potential threats. To put it into perspective, the scale of web-based threats demands a proactive approach to security.
- Web application attacks account for 26% of all breaches, making them the second most common type of attack.
- Web applications are the most vulnerable security vector or channel for hacking and social breaches, accounting for over 40% of all such incidents.
The complexity of the web channel creates numerous blind spots where the endpoint can completely lose visibility, making it a distinct and challenging channel to secure. This underscores the need for tailored security measures that specifically address the unique requirements of web-based applications and services.
- Fifth, visibility and control are still critical in 2023
Wasn’t this one of the original objectives for securing data? With the continued growth of regulatory compliance, expected to protect over 75% of individuals worldwide in 2023 (up from just 10% in 2020), the need for visibility and control is more important than ever. With data moving in multiple directions and across numerous locations, centralizing data security management across multiple channels, not just at the endpoint, becomes increasingly crucial. To ensure compliance and protect against cybersecurity threats, organizations must have robust visibility and control over their data flows, regardless of where they originate or terminate.
So, how are organizations expanding visibility and control beyond the endpoint? Many of them are incorporating additional channels and integrated data security methods. However, these methods often operate independently of the organization’s current DLP endpoint vendor, leading to decentralized data security. Forcepoint cautions against this approach for several reasons. Firstly, it can be extremely costly. More importantly, it greatly complicates DLP management and regulatory compliance, posing significant challenges for organizations.
Shield Your Business with ESDS Endpoint Security
Installing individualized security systems can be difficult. Customers may be hesitant to use your business’ services due to numerous security concerns. Users can pass the fewest security checks possible thanks to ESDS’ Endpoint security, which monitors user behavior and application behavior. Thus, users can gain from a faultless experience. One security system that connects to all computers, servers, and other devices is provided by endpoint security (ESDS). Due to this common characteristic, security solutions can dynamically prevent zero-day and multi-vector attacks. Endpoint security from ESDS uses a centralized security system to manage all active devices in a network. Because ESDS takes care of everything for you, there is less need to
To accommodate the growing variety of devices, whether on-premises or remote, employee or vendor, solutions and strategies must scale. The most important thing is to build your endpoint security technology stack with a solution provider like ESDS who works with the rest of your IT and security ecosystem.
- 6 Ways AI Reinvents the Security Landscape - January 9, 2024
- Top 6 Current Cybersecurity Trends For 2024 - January 9, 2024
- What Have We Learned from The Recent Cybersecurity Incidents? - January 3, 2024