How to Prevent Data Breaches with Cyber security monitoring services?

Data security is a critical concern for businesses of all sizes and industries, as cyber-attacks continue to rise and become more sophisticated. According to a recent study by IBM, the global average cost of a data breach in 2023 was $4.35 million, a 2.6% increase from the previous year. With the increasing frequency and severity of data breaches, it’s clear that businesses need to take proactive measures to protect their sensitive data and prevent costly and damaging breaches. Cyber security monitoring services are an essential tool in preventing data breaches and safeguarding your business against cyber threats. In this article, we will explore the key ways in which cyber security monitoring services can help protect your business, and provide tips for implementing these services effectively. By prioritizing your data security and investing in cyber security monitoring services, you can help minimize the risk of data breaches and protect your business from the damaging consequences of cyber-attacks.
What are Cyber Security Monitoring Services?

Cyber security monitoring services refer to a set of advanced security measures that organizations use to monitor their IT infrastructure, networks, and systems in real-time. These services aim to detect and prevent security threats, including cyber-attacks, data breaches, and other unauthorized activities, by continuously monitoring and analyzing network traffic, logs, and user behavior. Cybersecurity monitoring services are designed to offer a holistic approach to security, providing organizations with end-to-end visibility and control over their entire IT environment. These services work by deploying advanced monitoring tools that use a range of techniques, such as intrusion detection and prevention systems, security information and event management (SIEM) solutions, and threat intelligence feeds, to collect and analyze security data from various sources. These tools can then identify anomalous behavior and potential security incidents, alert security teams in real-time, and provide actionable insights to remediate the threat. Cyber security monitoring services also offer security teams with 24/7 support, incident response planning, and threat-hunting capabilities to ensure timely detection and response to security incidents.
Cyber security monitoring services differ from other types of security measures, such as firewalls, antivirus software, and intrusion detection systems, as they provide a more comprehensive and proactive approach to security. While traditional security measures focus on preventing security threats at the perimeter, cyber security monitoring services provide continuous monitoring and real-time analysis of security data across the entire IT environment, including cloud-based and mobile devices. This makes these services better suited to detect and prevent sophisticated and targeted attacks that can evade traditional security measures. Overall, cyber security monitoring services are an essential component of any organization’s security strategy, providing end-to-end protection against a wide range of security threats.
The Importance Of Cyber Security Monitoring Services In Preventing Data Breaches

Cybersecurity threats continue to evolve at an alarming pace, and data breaches are becoming more common than ever. Data breaches can have severe consequences for businesses, including financial losses, reputational damage, and legal liabilities. To prevent data breaches, organizations must have robust cybersecurity measures in place, and comprehensive cybersecurity monitoring services play a critical role in this regard. Key threats and vulnerabilities that can lead to data breaches include phishing attacks, malware infections, social engineering, insider threats, and unpatched software vulnerabilities. Comprehensive cybersecurity monitoring services help to detect and prevent these threats by providing continuous monitoring and real-time analysis of security data across the entire IT environment.
These services use advanced tools such as intrusion detection and prevention systems, security information and event management (SIEM) solutions, and threat intelligence feeds to identify anomalous behavior and potential security incidents. They also provide 24/7 support, incident response planning, and threat-hunting capabilities to ensure timely detection and response to security incidents. Specific features and tools of comprehensive cybersecurity monitoring services that are particularly effective in preventing data breaches include user behavior analytics (UBA), endpoint detection and response (EDR), and threat intelligence feeds. UBA helps to detect insider threats and anomalous user behavior, while EDR provides real-time monitoring and analysis of endpoint devices to detect and prevent malware infections. Threat intelligence feeds provide up-to-date information on the latest threats and vulnerabilities, enabling organizations to stay ahead of the curve and proactively prevent data breaches. Hence, comprehensive cybersecurity monitoring services are essential for preventing data breaches. These services provide end-to-end protection against a wide range of cybersecurity threats, and their advanced features and tools are particularly effective in detecting and preventing data breaches. By leveraging these services, organizations can ensure that their IT infrastructure, networks, and systems are secure and resilient against cybersecurity threats.
Key Strategies for Implementing Cyber security monitoring services
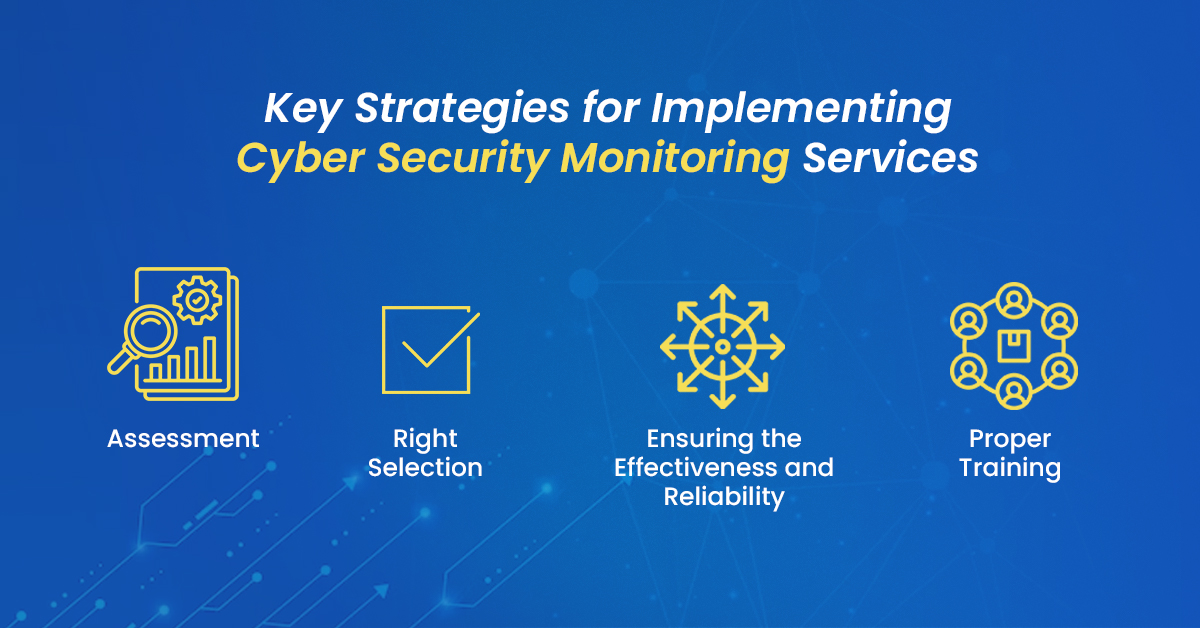
Implementing cybersecurity monitoring services is essential for protecting organizations against cyber threats. However, it is crucial to have a well-planned strategy for successful implementation. This brief will discuss the key strategies for implementing cybersecurity monitoring services in your organization.
Assessment: The first strategy is to assess your organization’s cybersecurity risks and requirements. This will help you determine the scope of the cybersecurity monitoring services you need to implement. You should also consider your organization’s specific needs, such as compliance requirements or the need for real-time threat detection.
Right Selection: The second strategy is to choose the right cybersecurity monitoring service provider. Key considerations when selecting a provider include their experience, expertise, and track record in providing cybersecurity monitoring services. You should also consider the provider’s capabilities, such as the ability to monitor endpoints, networks, and cloud environments. Comprehensive Framework: The third strategy is to implement a comprehensive cybersecurity monitoring framework. This framework should include policies, procedures, and tools to monitor and detect threats across the entire IT environment. You should also establish incident response plans to address and mitigate any security incidents detected.
Effective and Reliable: The fourth strategy is to ensure the effectiveness and reliability of your cybersecurity monitoring services. This can be achieved through regular testing and validation of your monitoring capabilities, as well as by ensuring that your security controls are properly configured and up-to-date.
Proper Training: Finally, ongoing training and education are crucial for the success of your cybersecurity monitoring services. Ensure that your staff is trained on cybersecurity best practices and understands their roles and responsibilities in monitoring and detecting cybersecurity threats.
So, implementing cybersecurity monitoring services requires a well-planned strategy that includes assessing your organization’s risks and requirements, selecting the right service provider, implementing a comprehensive monitoring framework, ensuring the effectiveness and reliability of your monitoring services, and providing ongoing training and education to your staff. By following these strategies, organizations can enhance their cybersecurity posture and protect against cyber threats.
Conclusion:
In conclusion, comprehensive security monitoring services are an essential tool in preventing data breaches and safeguarding your business against cyber threats. By leveraging the latest technologies and techniques, these services can help detect and prevent a wide range of threats, including insider threats, malware, phishing attacks, and more. When implementing security monitoring services, it’s crucial to select a reliable and experienced service provider and ensure that the services are tailored to the unique needs of your business. Additionally, it’s important to prioritize employee education and training on best practices for data security to complement the security monitoring services. By taking a proactive and comprehensive approach to data security, businesses can help minimize the risk of data breaches and protect themselves from the damaging consequences of cyber-attacks. Investing in security monitoring services is a critical step in this process, and we hope that this post has provided valuable insights into the key benefits and strategies for implementing these services effectively.
