Cyber Security: Your incident vs response plan
The threat of cyberattacks and ransomware assaults has increased significantly as technology continues to permeate more and more aspects of our daily life. Therefore, any organization must have a cyber-incident response plan to defend against and respond to cyber threats.
This manual will walk you through the crucial components of an efficient cyber incident response plan. We also discuss the six stages of a cyber-incident response plan based on NIST incident response guidelines. We’ll also demonstrate how to carry out this plan well and strengthen your incident response capabilities.
Critical Elements of a Cyber Incident Response Plan
We must reiterate right away that building cyber resilience takes time. It is insufficient to only have an efficient incident response plan. This strategy needs to be updated regularly to account for new risks.
Additionally, you may occasionally consult with outside cybersecurity experts to get their expert assessment of your preparedness for a cyberattack. They can also assist in updating your strategies and protocols. Finally, to determine just how vulnerable your organization is in the event of an incident, they can also help you conduct a thorough risk assessment.
Several important components should be present in a thorough cyber incident response plan, including:
- An organized team with defined tasks and responsibilities for responding to incidents.
- The incident response plan is routinely tested and trained. By doing so, it will be guaranteed that the plan would truly limit the harm that data breaches and/or ransomware attacks may do.
- Procedures for locating, stopping, stopping the spread of, analyzing, eradicating, and recovering from an incident.
- Plans for communicating the occurrence and its effects to stakeholders, including employees, clients, and customers.
- Knowing when to contact law enforcement and how to do so in case of a cybersecurity incident.
The steps to assess and modify the incident response strategy.
The NIST Computer Security Incident Handling Guide’s advice should be considered.
A CIRP should incorporate specific protocols for other incident types, such as malware, phishing, and natural catastrophes, in addition to these essential components.
Six Incident Response Phases
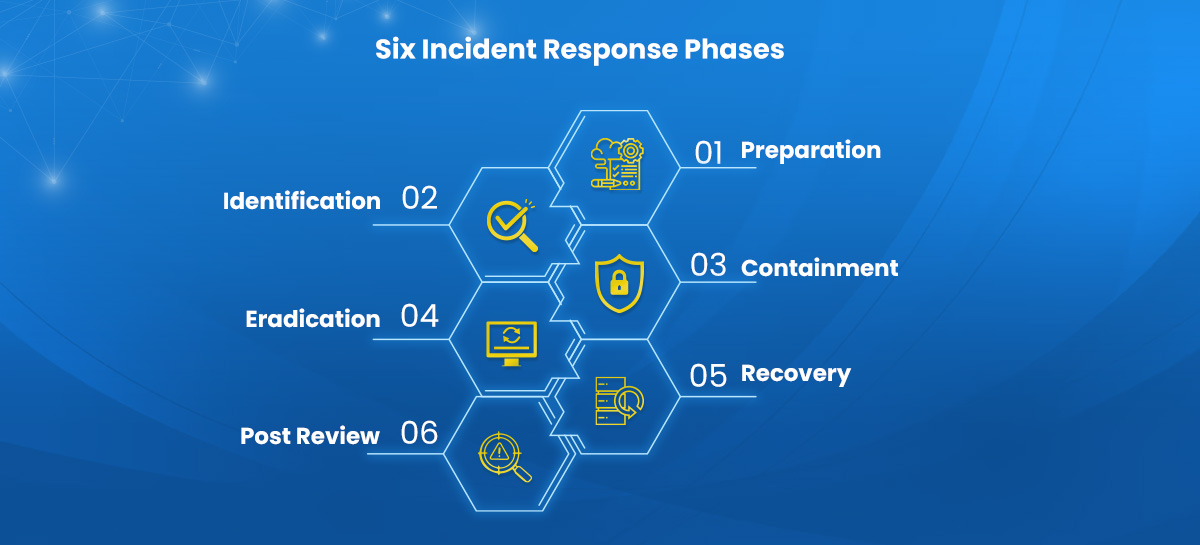
Let’s move on to the six essential phases of incident response now that you probably have a clearer concept of what should be in a cyber-incident response plan.
Phase 1: Preparation
An incident response plan’s initial phase is all about getting ready. This entails determining potential threats and weaknesses as well as creating a strategy for handling cybersecurity crises. It’s crucial to have an established team of incident responders, as well as roles and duties that are crystal clear for every team member. To ensure preparation in the case of an actual attack, this phase also involves testing the incident response plan and providing frequent cybersecurity training to the workforce.
Phase 2: Identification
Identification takes place in a CIRP’s second phase. This entails locating the precise occurrence and estimating how it will affect the organization. This is often accomplished by keeping an eye out for odd activity on various systems and networks and by checking security logs.
Phase 3: Containment
The next stage is to contain an incident after it has been located in order to limit additional harm. This can entail removing impacted systems from the network, installing firewalls, and taking other precautions to stop the problem from spreading.
According to many experts, this is incident response’s most important component and the reason why business continuity depends on it so much.
Let’s be honest. An attack can no longer be completely avoided. The best we can do is efficiently handle an event so that the business can quickly recover.
Minimal interference with business operations, financial results, and brand perception is desired.
Phase 4: Eradication
Eradication is the fourth stage of incident response. This entails eliminating the incident’s cause and resetting the systems to their default settings. This can entail removing malware, fixing vulnerabilities, and taking further precautions to stop the incident from happening again.
Phase 5: Recovery
Recovery is a CIRP’s fifth phase. This entails bringing things back to normal and getting things back to business as usual. This might entail recovering data, evaluating systems, and offering assistance to staff members and clients.
The main objective of eradication and recovery is to ensure that no malware remains on your systems following an assault. Additionally, all the flaws and cracks that initially caused your network to be compromised must be instantly closed.
Phase 6: Post Review
Lessons learned, also known as post-incident activity, is the last stage of a CIRP. This entails assessing the incident response procedure, finding potential areas for development, and revising the incident response plan as required. To stay abreast of the most recent threats and vulnerabilities and avert more security events, it is crucial to regularly update the incident response strategy.
Conclusion: Creating an Effective Incident Response Plan
To safeguard your company from potential cyber-attacks, you must have a cyber-incident response plan. ESDS’ security services can successfully get you ready, respond to, and recover from a cyber-incident.

Additionally, you must regularly conduct coached cyber-attack tabletop exercises properly to test the efficacy of your incident response procedures. These tests will help you determine whether your strategies are practical and up to date, given the shifting nature of the threat environment. The facilitator should provide you with an executive report that highlights the tabletop exercise’s areas for development, gaps, and strengths.
This study can significantly increase your cyber resilience. It also makes sure that important information about your clients, business partners, and company as a whole is kept secure.
- Why does your business need Endpoint Detection and Response (EDR)? - May 15, 2024
- Are your business endpoints completely secure? - March 26, 2024
- Is Colocation key to transforming your data center management strategy? - March 22, 2024