How to Choose the Right VAPT Service Provider?

VAPT stands for Vulnerability Assessment and Penetration Testing. VAPT is a systematic approach to strengthening your organization’s security posture by detecting, prioritizing, and mitigating infrastructure vulnerabilities. It also helps you keep in compliance with numerous industry requirements throughout the year. Vulnerabilities Assessment and Penetration Testing is the process of identifying and exploiting all potential vulnerabilities in your infrastructure with the ultimate purpose of reducing them. VAPT is performed by security specialists who specialize in offensive exploitation. Simply described, VAPT is a proactive “hacking” activity in which you exploit vulnerabilities in your infrastructure before hackers find them.
External security specialists do VAPT (Vulnerability Assessment & Penetration Testing), leveraging their experience to simulate hacker techniques, find major security flaws, and cooperate with you to develop successful repair solutions.
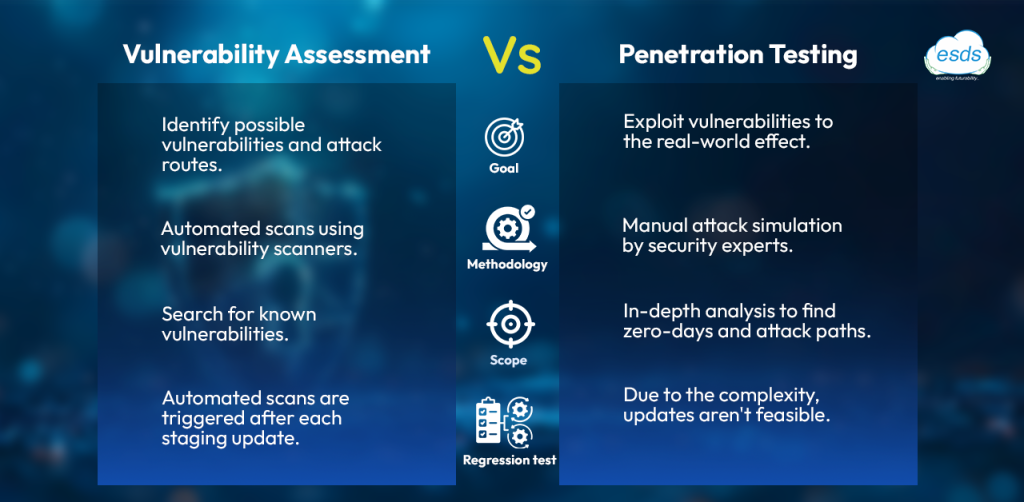
Within a VAPT, the VA (Vulnerability Assessment) uses security engineers and a variety of automated techniques to discover possible vulnerabilities. The VA is followed by a PT (Penetration Test), in which a real-world attack is simulated to exploit the vulnerabilities discovered during the VA.
Did you know? According to a recent Surfshark analysis, India placed sixth in the world for data breaches in 2023, with 5.3 million accounts compromised.
What Does the VAPT Testing Do?
Step 1: Planning and Scoping.
Here, one outlines the goals of vulnerability assessment and penetration testing, its objectives, and its scope. This is about selecting key assets to be tested, making decisions on which testing methodologies or priorities for compliance to take, and developing communication channels with your VAPT testing provider.
Step 2: Information Gathering
During this step in VAPT testing, the testing team formed information on target systems, network architecture, and possible vulnerabilities using publicly available sources and allowed ways. They would, in the case of a gray box, get information from you and start mapping your target systems.
Step 3: Vulnerability Assessment.
The VAPT service providers make use of predefined scanners and automated methods to scan your systems for known vulnerabilities. It identifies potential software weaknesses, configuration settings, and security mechanisms.
Step 4: Penetration testing
The security experts try to exploit the discovered weaknesses by using hacking techniques. It will simulate real-world attacks to see the impact and effectiveness of your security policies.
Step 5: Reporting and Remediation.
Following exploitation, they provide a thorough VAPT report that details the vulnerabilities discovered, exploitation attempts conducted, and suggestions for remedy. This step also includes developing a strategy to resolve vulnerabilities and improve your overall security posture.
Step 6: Rescan and VAPT Certificate Issue
After the vulnerabilities have been fixed, certain penetration testing businesses may offer rescans to confirm the above, create clean reports, and issue publicly verifiable VAPT certificates to aid compliance checks.
Difference between Vulnerability Assessment and Penetration Testing
Choose Your Expert VAPT Service Provider
Below is the diagram with a brief understanding to help you decide on the VAT service provider.

- Understand your needs.
Before looking at supplier possibilities, consider your organization’s particular needs. Consider the size and complexity of your IT infrastructure, industry laws, budget, timetable, and VAPT scope.
- Methodology Depth
Look for VAPT service providers who use proven approaches like the OWASP Testing Guide (OTG) or PTES (Penetration Testing Execution Standard) to conduct a thorough examination.
- Better Communication: –
When selecting a VAPT provider, prioritize open and honest communication, as the procedure might take 10-15 business days. They should give you regular progress updates, comprehensive explanations of results, and a joint repair strategy to reduce bottlenecks and maximize VAPT cycle efficacy.
- Cost Effectiveness: –
When selecting a VAPT provider, consider value and ROI beyond the initial assessment. Examine the complexity of reports, customizable metrics (if available), post-assessment help, remedial advice, and retesting choices.
What Makes ESDS VAPT Services Better Compared to Others?
A Vulnerability Assessment and Penetration Testing (VAPT) service performed once a year may not be sufficient for website security. To assure your website security throughout the year, we provide extra yearly website vulnerability screening services with ESDS’ very own VTMScan.
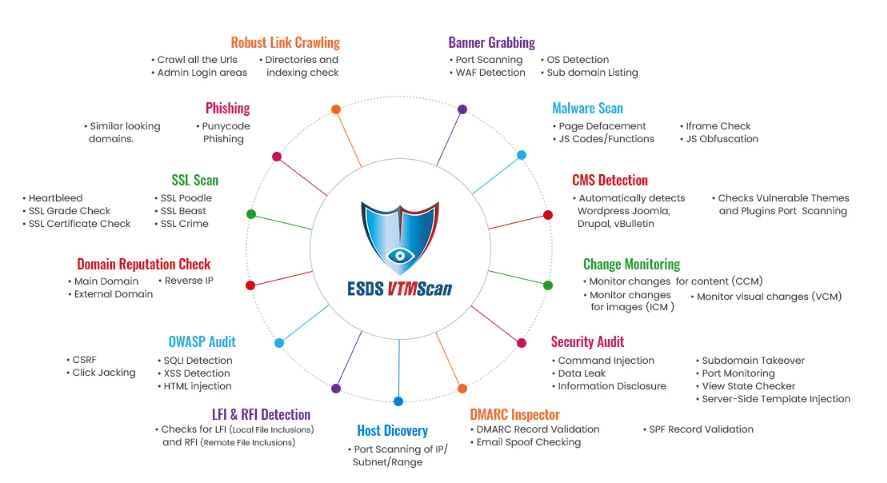
VTMScan is a sophisticated website vulnerability scanner that detects all types of online threats and cyberattacks, including OWASP Top-10 vulnerabilities, SQL injections, and Cross-Site Scripting, to mention a few. VTMScan provides total website protection by conducting a comprehensive security assessment four times per year.
Below is the diagram that will give you a complete overview of ESDS VAPT Testing Services.
How Does the ESDS VAPT Services Methodology Work?
Behind the working of ESDS VAPT Services lie four steps, which are as follows: –
- Pre-assessment: Reviewing the scope by the ESDS VAPT service provider and defining objective formulation; information gathering and identification of the potential risks before the assessment.
- Testing: Performing the scanning, and also conducting automated and manual testing.
- Post-Assessment: Prepare the vulnerabilities report and present it for discussion with the customer.
- Rescanning: The rescanning of all closed vulnerabilities, finding report sharing, and discussing the last ESDS VAPT service project sign-off.
Final Thought
With the present state of cybercrime, the issue is no longer whether to participate in a VAPT but which vulnerability assessment and penetration testing are ideal for you.
A complete Vulnerability Assessment and Penetration Testing with continuous scanning not only strengthens your security posture but also fosters a security-first strategy, ensures compliance throughout the year, and strengthens consumer trust.
Vulnerability Assessment and Penetration Testing (VAPT) service offered by ESDS analyzes, rates, and ranks the technical strengths and weaknesses of your company’s online security. It is applicable to both websites and web applications. Organizations are given real-time visibility into website security threats through this approach.
