A Complete Guide to Privileged Access Management (PAM)
A system for information security called privileged access management (PAM) protects identities with privileged access or skills above and beyond those of regular users. PAM functions through a combination of people, processes, and technology.

Due to the privileged risk accounts pose to the technological environment, we handle them cautiously. For instance, if someone were to misuse the administrator or service account credentials, the organization’s systems and private information might be compromised. Threat actors compromising privileged access accounts cause data breaches. We need to add more levels of security because, in a technological environment, these accounts contain the keys to unlock every door. A solution for Privileged Access Management provides further security.
What does Privileged Access Management Do?
A crucial security measure is privileged access management, which makes it easier for enterprises to define, track, and manage privileged access across all of their IT systems, applications, and infrastructure. In order to provide people only the access they require, PAM solutions impose the least privileged access and centralize management of administrator roles.
Technical restrictions limit access to only authorized users and can make use of better authentication techniques, thus privileged access management technologies reduce the need to share passwords. By upholding the principle of least privilege, which demands that users only have the access necessary to perform their job functions, it also fights insider threats and privilege abuse. Superusers with unlimited access can be removed by tying access to job positions and consequently, individual accounts. For high-risk servers, these technologies might additionally demand additional authorization, boosting security. Finally, user accountability is provided through privileged access management using tools like keystroke tracking.
Why Is Privileged Access Management Essential?

In order to safeguard their data and systems against unauthorized users, many businesses now place a high focus on controlling privileged access effectively. That’s because unauthorized access has the potential to damage sensitive information, reveal valuable business data, and have a negative impact on system dependability. Privileged accounts frequently offer a simple means to access a company’s platforms, networks, and systems. Additionally, given the recent significant upheaval in the workforce, they create a significant opportunity for threat actors.
The good news is that enterprises are prioritizing their investment in privileged access control as a result of this disruption. In the upcoming year, businesses will prioritize putting in place efficient PAM systems, according to the 2020 Identity and Access Management Report. Particularly, 57% of those surveyed said it is their top investment concern. In a similar vein, Gartner forecasts that in the upcoming years, more than two-thirds of businesses will employ privileged access control.
Protecting high-level privileged accounts is a crucial part of a comprehensive, layered security strategy. IT and security teams are better able to stop internal and external attacks on vital systems by having complete control over privileged accounts.
What Are Privileged Access Management Best Practices?
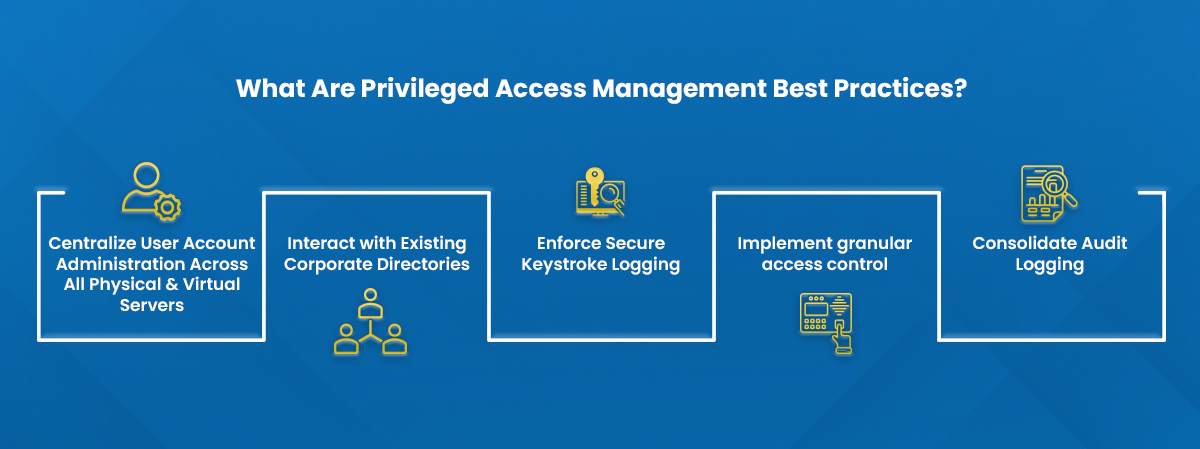
Privileged account management can first appear overwhelming, but there are a number of best practices that can assist organizations in efficiently managing these higher-level accounts.
Centralize User Account Administration Across All Physical and Virtual Servers
By centralizing user account administration across your environment, you can track and audit which users have access to which devices.
Interact with Existing Corporate Directories
Privileged account management must smoothly integrate with existing corporate directories and identity management systems so that team and group identities can be instantly linked to the appropriate systems, applications, and data.
Enforce Secure Keystroke Logging
For sensitive sessions, you must also be able to adapt to enforce complete keystroke logging, allowing for the detailed tracking of administrator operations.
Implement granular access control
You need to have enforceable authorization rules that require the use of distinct, auditable user accounts. Implement fine-grained security controls to establish and enforce who, when, how, and from where enhanced privilege is issued.
Consolidate Audit Logging
One component of safeguarding privileged accounts is comprehensive audit logging that is centralized and kept in one place. PAM systems that provide unified audit logs and reports from all of your server domains should be used in a separate security domain.
Common Techniques the Organization Must Employ to Ensure PAM Is Implemented Correctly
- Every organization that makes use of PAM should adhere to the following standard practices for the proper implementation of PAM Software
- All privileged accounts should be properly inventoried and kept current by the organization.
- Organizations shouldn’t permit account sharing by granting administrative access.
- When choosing a password, every firm should follow its password policy.
- Give the restricted members access to the privileged account.
- Utilize a variety of tools and monitoring programmes to properly learn what the privileged users are doing.
- Staff members should be made aware of changes to privileged access policies and procedures so they may make sure they are using and managing their privileged credentials properly.
- Every organization should keep up-to-date records of its account management policies and procedures.
The final Word
Privileged access management aids organizations in safeguarding privileged accounts and credentials. The information gives you a complete comprehension of how to utilize PAM and what to keep in mind when using Privileged Access Management (PAM). In order to achieve privilege maturity, many businesses follow a similar approach, targeting quick wins and the greatest risks initially before gradually enhancing privileged security measures across the entire enterprise. The optimum strategy, however, will only be identified after conducting a thorough audit of privileged risks and outlining the measures necessary to reach the ideal state of privileged access security policy.
- Why does your business need Endpoint Detection and Response (EDR)? - May 15, 2024
- Are your business endpoints completely secure? - March 26, 2024
- Is Colocation key to transforming your data center management strategy? - March 22, 2024
