What is Cybersecurity Automation?
According to Security Magazine, cyberattacks happen every 39 seconds. And we cannot stress enough how it has taken center stage as the biggest concern for organizations of all sizes and industries. The increasing frequency and sophistication of cyber threats have made it imperative for businesses to implement robust security measures to protect their sensitive data and secure their networks. One of the key solutions that organizations are turning to is cybersecurity automation. This article will delve into the world of cybersecurity automation, exploring what is cybersecurity automation, the benefits of cybersecurity automation, and its best practices. We will also discuss how organizations can get started with implementing cybersecurity automation solutions. By the end of this article, you will have a comprehensive understanding of cybersecurity automation and its importance in safeguarding your organization against cyber threats.

What is Cybersecurity Automation?
Cybersecurity automation refers to the process of automatically detecting, investigating and remediating cyber threats using programmatic solutions designed specifically for this purpose. It involves leveraging technology to identify potential security risks, categorize and prioritize them, and initiate appropriate responses without human intervention. By automating these tasks, organizations can streamline their security operations and enhance their ability to respond effectively to cyber threats.
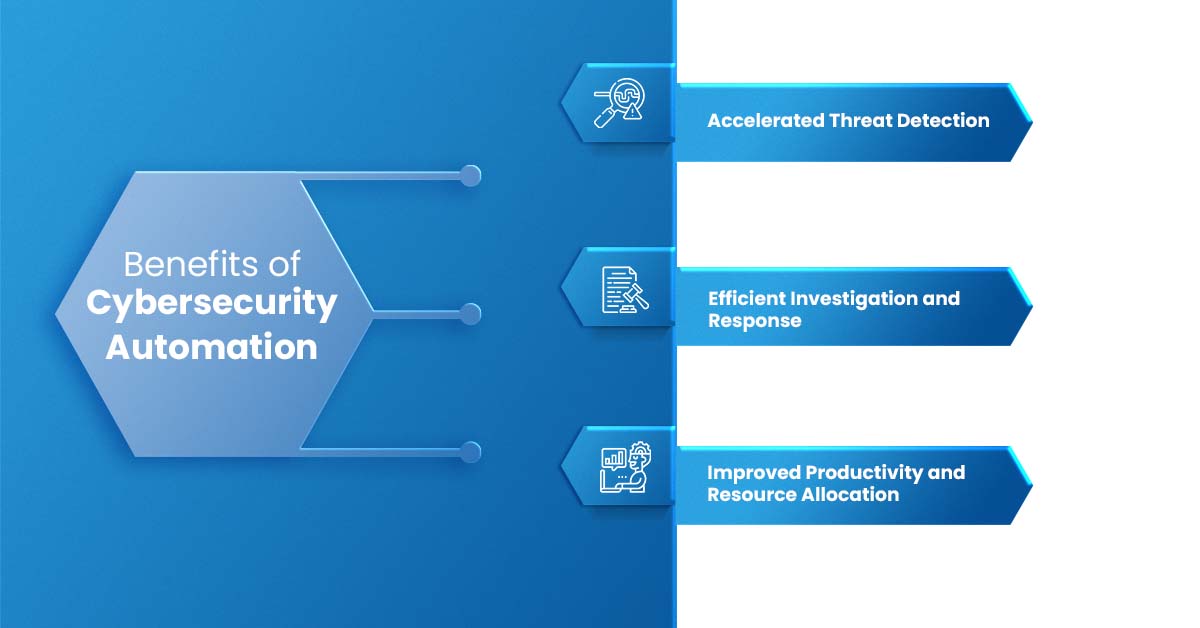
Benefits of Cybersecurity Automation
The Splunk State of Security 2022 Report highlights that it takes a median of 14 hours to recover business-critical applications from cybersecurity-related downtime. Given the cost of downtime at an average of $200,000 per hour, this results in an annual expense of $33.6 million per organization. Additionally, according to Accenture’s “State of Cybersecurity Resilience 2021” report, data breach expenses are projected to rise from $3 trillion to over $5 trillion by 2024.
The longer the time taken to detect, investigate, and respond to a cyber-attack, the greater its potential impact, including the likelihood of causing downtime. In the current threat landscape, swift identification and resolution of cyber threats are crucial for minimizing attack consequences. Before automated security processes were integrated into security operations centers, human analysts were solely responsible for manually addressing all threats. This involved investigating numerous alerts, enhancing them with threat intelligence, and deciding on appropriate actions for containment and remediation. Given the influx of alerts in modern organizations, this level of manual intervention is no longer feasible.
Compounding this issue, many alerts are not linked to cyber threats or malicious activity, despite appearing so initially. Consequently, analysts invest valuable time into investigating false positives, leading to alert fatigue and diverting them from more critical duties. Security automation carries out these tasks automatically and instantly, surpassing the capabilities of even the most skilled human analyst.
With more time available, security analysts can engage in more rewarding strategic activities, including growth planning, proactive threat hunting, and conducting in-depth security analyses. This stands as a significant advantage of security automation for both the organization and its security team.
Here are the key benefits of cybersecurity automation
Accelerated Threat Detection
One of the primary advantages of cybersecurity automation is its ability to accelerate threat detection. Traditional security operations typically rely on human analysts to analyze a vast number of security alerts, which can lead to alert fatigue and the risk of overlooking critical threats. With automation, organizations can leverage advanced algorithms and machine learning techniques to quickly identify and categorize potential threats, reducing the risk of missing critical security incidents.
Efficient Investigation and Response
Cybersecurity automation solutions excel at enriching, correlating, grouping, and prioritizing alerts, which accelerates the investigation process. By integrating threat intelligence and leveraging predefined actions, automation platforms can effectively contain and remediate security issues. These solutions can perform these actions in seconds, often without requiring human intervention. This not only improves response times but also reduces the likelihood of errors caused by alert fatigue.
Improved Productivity and Resource Allocation
Automating repetitive and manual security tasks allows security analysts to focus on more strategic activities. With fewer mundane tasks to handle, security teams can channel their efforts toward proactive threat hunting, security analysis, and planning for growth. This not only enhances the productivity of security analysts but also ensures that their expertise is utilized for higher-value tasks.
When Does an Organization Need Cybersecurity Automation?
While cybersecurity automation offers significant benefits, it may not be necessary for every organization. Here are some signs that indicate an organization could benefit from implementing cybersecurity automation:
- High Alert Volume and Alert Fatigue: If your security team is overwhelmed by the sheer volume of security alerts and is experiencing alert fatigue, it may be a sign that automation is needed. Automating the triage and analysis of alerts can help reduce the burden on security analysts and allow them to focus on critical incidents.
- Increased Dwell Times and Slow Incident Response: If your organization is experiencing long dwell times, which refers to the length of time a threat goes undetected, it may indicate a need for automation. Slow incident response times can be detrimental, as it increases the potential impact of cyber-attacks. Automating incident response can help organizations detect and respond to threats more efficiently.
- Overwhelming False Positives: If your security team is spending a significant amount of time investigating false positives, it may indicate a need for automation. By automating the identification and elimination of false positives, organizations can reduce the time wasted on non-threatening incidents and focus on genuine security threats.
Cybersecurity Automation Solutions
Implementing a cybersecurity automation solution is crucial for organizations looking to enhance their security posture. These solutions offer a unified approach to handle security needs across the entire organization, streamlining security operations and ensuring consistent and auditable processes. Here are some key capabilities of cybersecurity automation platforms:
Standardized Workflows
Cybersecurity automation platforms leverage playbooks to establish standardized workflows. These playbooks define the actions to be taken in specific scenarios, ensuring consistent and repeatable processes. Standardized actions can include quarantining malware-infected files, performing geolocation lookups, blocking URLs, and more. By standardizing workflows, organizations can reduce the risk of errors and ensure a more efficient response to security incidents.
Seamless Integration with Security Systems
A robust cybersecurity automation solution seamlessly integrates with existing security systems, including firewalls, endpoint products, reputation management services, and security incident and event management (SIEM) systems. This integration allows for the orchestration of actions across multiple attack vectors and ensures the involvement of various security tools. By integrating with existing security assets, organizations can optimize their security operations and achieve a more comprehensive defense against cyber threats.
The Evolution of Cybersecurity Automation
Cybersecurity automation has evolved as a response to the increasing number and complexity of cyber threats. Initially, organizations relied on automated incident response systems to identify and respond to security breaches. While these systems helped improve response times, they did not address the underlying need for a more proactive approach to cybersecurity.
This led to the development of cybersecurity automation and orchestration, which focused on connecting security tools and workflows to enable more coordinated and efficient responses to security incidents. Today, security orchestration, automation, and response (SOAR) systems are available, offering a comprehensive solution that automates both responses and their coordination across complex infrastructures. These systems reduce the potential for human error and provide organizations with a more effective defense against cyber threats.
Automation vs. Orchestration
While the terms automation and orchestration are often used interchangeably, they refer to different aspects of cybersecurity operations. Automation focuses on automating specific security tasks, such as threat detection and response. It involves leveraging technology to perform these tasks without human intervention, improving efficiency and reducing errors.
On the other hand, orchestration aims to connect and coordinate various security tools and workflows to ensure they work together seamlessly. It involves integrating different security systems and enabling the exchange of information and collaboration between them. Orchestration enhances the effectiveness of automation by creating a unified and cohesive security infrastructure.
Getting Started with Cybersecurity Automation
Implementing cybersecurity automation requires careful planning and consideration. To get started, organizations should follow these steps:
- Establish Your Needs
Before considering specific vendors, organizations should assess their cybersecurity needs. The cyber risk profile of the organization, as well as the industry it operates in, should be taken into account. By understanding the specific challenges and requirements, organizations can identify the tools, processes, and solutions needed to address their security needs effectively.
- Define Use Cases
Based on the identified needs and priorities, organizations should define specific use cases for cybersecurity automation. These use cases should align with the organization’s goals and address the most pressing security challenges. Taking the time to define clear use cases will help organizations in their research and evaluation of vendors and enable the creation of effective playbooks.
- Research Providers
With defined use cases and requirements in mind, organizations can start researching cybersecurity automation providers. It is crucial to evaluate vendors based on their ability to meet the organization’s specific needs. Factors to consider include ease of use, flexibility, integration capabilities, deployment length, and technical support. It is recommended to opt for vendors that offer solutions with minimal coding requirements and seamless integration with existing tools.
Conclusion:
Cybersecurity automation is a critical component of modern security operations. By automating threat detection, investigation, and response processes, organizations can enhance their ability to defend against cyber threats effectively. Automation enables accelerated threat detection, efficient investigation and response, and improved productivity and resource allocation for security teams. However, it is important to approach cybersecurity automation strategically and follow best practices to maximize its value.
Implementing cybersecurity automation requires careful planning, establishing priorities, and selecting the right solutions. By leveraging automation and security orchestration, organizations can build a robust security infrastructure that protects against cyber threats and ensures the resilience of their operations. Cybersecurity automation is no longer a luxury; it is a necessity in today’s rapidly evolving threat landscape.
Remember, when implementing cybersecurity automation, it is crucial to choose a reliable and trusted partner. ESDS Software Solution Ltd. offers comprehensive cybersecurity solutions that can help organizations automate their security operations and protect against a wide range of cyber threats. With ESDS, you can enhance your security posture and ensure the safety of your digital assets.
- Top 5 Data Center Trends for 2024 - October 11, 2023
- Top 15 Cloud Computing Trends 2024 - October 4, 2023
- What is Infrastructure Monitoring and Why Infrastructure Monitoring Tool is Important for Your Business? - September 20, 2023
