What you should know about Cloud Security?
Cloud Security
Security is an important parameter for the functioning of any organization in today’s IOT world. Let’s review about security breaches and steps to mitigate them.
We all are aware of the dangerous harm that viruses can cause to enterprise IT. The trojan and malware attacks can cripple the organisational IT.
Apart from the traditional viruses, trojans and malware; the most dangerous security threat in the modern world are hackers.
A successful cyberattack can bring IT operations (or related) to a standstill for hours, also days and weeks, depending on the severity of the attacks. The financial damage and reputational damage can continue much longer making the organisation very difficult to bounce back.
Studies show that about 71% of small and middle sized organisations fall prey to attacks of cyber criminals.
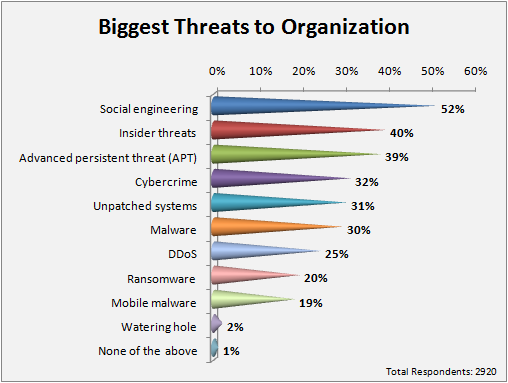
Ref: CIO and Leader article
Security in Cloud Computing
We now live in the Cloud era where majority of services we use, dwell in the Cloud. Subsequent to the benefits such as efficiency and cost-saving, the prime concern of security in the cloud cannot be overlooked. Initiatives like BYOD , IT departments can lose sight and control over the application, making IT more vulnerable to cyber attacks.
Irrespective of the security protocols followed by the enterprises, the staff tries to download applications, softwares for professional purpose which they think are needed and useful for them making it actually a hazard in disguise.
We are using Cloud in all phases of life-be it professional or personal. The family photographs, official documents, critical client data are stored and accessed in the cloud.
Be secure from Hackers
Hackers do this act, because the information has some stake value, they earn their bread-and-butter from the hacks. With the advancement of technology , the hacking groups have become technically sound and sophisticated.
Post breach, intangible slashes an organization suffers is loss of customer loyalty and market capital.
In November 2014, the hacker world invaded Sony Pictures Entertainment and leaked confidential data like salaries, emails, high profile celebrity personal information and copies of unreleased films.
We can’t forget the Ashley Madison hack in mid-July 2015 where hacker group penetrated into the servers to get information of 37million online users. They got access to PayPal accounts, windows passwords and names of the people using this ‘personal space’ site.
Lately, a popular smartphone game ‘Clash of Kings’ forum was hacked (July 2016), giving access to data of about 1.6 million users. The mobile data, social network data and other critical data was put to risk.
Ways to ensure Security in Cloud
To be safe and secure, CIOs and CISOs can’t blindly trust the third party cloud vendors.Even the approved and renowned cloud vendors should be scrutinized, on regular basis, to check whether they meet up to your demands! Understand how the cyber criminals are kept away from your data, the level of security and liability of cloud service provider in case of any breach.
Make it a practice to scan IT systems at regular intervals and the risk assessment is done periodically.
Scan the corporate website with website scanning tools like ESDS VTMScan which not only detects the vulnerability but also tests with minor attacks. Update software used for organizational purpose like CMS, OS, Antivirus etc.
To bounce back immediately after the security breach or mitigate the effect due to cyber attack, a functional incident response team is vital. The team will work in two phases viz. planning phase and response-recovery phase post attacks.
Cloud Storage is cheap but the data is valuable. So next time when you find a flaw in security, fix it immediately.
Speak to our cloud experts and know how your data can rest securely in eNlight Cloud. Click to call.
- The Impacts of GST on Organisational IT - June 23, 2017
- Cloud Technology becomes more intelligent with AI - June 5, 2017
- 5 Easy Hacks to prevent WannaCry Ransomware Attacks and keep your System Safe! - May 13, 2017