How to Prevent The Distributed Denial of Service Attack with ESDS eNlight WAF
For over a decade, the unparalleled digital transformation has led businesses to keep investing in their cyber resilience. Making such investments is essential to shielding modern businesses against various kinds of cyberattacks. Distributed Denial of Service (DDoS) attacks are amongst the most advanced kinds of cyberattacks. The Distributed Denial of Service (DDoS) attacks are malicious entity attempting to overwhelm a networked resource (such as a website or networked services) with an excessive volume of internet traffic towards making it inaccessible to its users. The majority of DDoS attacks involve botnets – one or more infected computer networks – to overwhelm the target resource with traffic. Data from several forms of traffic, including HTTP (Hypertext Transfer Protocol) requests, UDP (User Datagram Protocol) packets (also known as UDP floods), ICMP (Internet Control Message Protocol) packets, and more, can be combined into one traffic stream.
DDoS attacks can have disastrous impacts on people and organizations alike. These attacks, for example, may result in financial losses, harm to one’s reputation, and legal problems (such as obligations regarding private information). A number of companies have seen similar outcomes in recent years as a result of well-known attacks against their infrastructures. In this context, consider the DDoS attack that occurred against the GitHub code-sharing website in 2018, which at the time was thought to be the biggest attack in history.
Over the last couple of years, there have also been multiple DDoS attacks. Conveniently labeled as “reflection amplification,” the attacks used a novel approach to increase the traffic. This innovation is indicative of how DDoS attacks are always changing, and businesses need to be aware of the most recent attack techniques. The first step in defending against DDoS attacks is for people and organizations to understand the risks involved and how difficult these attacks can be.
Solving the DDoS Puzzle
DDoS attacks are particularly popular among hacker communities since they are exceptionally difficult to prevent. Organizations struggle to detect and respond to DDoS attacks for the following reasons, in particular:

- 6 Ways AI Reinvents the Security Landscape - January 9, 2024
- Top 6 Current Cybersecurity Trends For 2024 - January 9, 2024
- What Have We Learned from The Recent Cybersecurity Incidents? - January 3, 2024
Determining the nature of the DDoS attack is crucial for allocating resources for the cyber defense appropriately. The following are the most typical types of DDoS attacks:
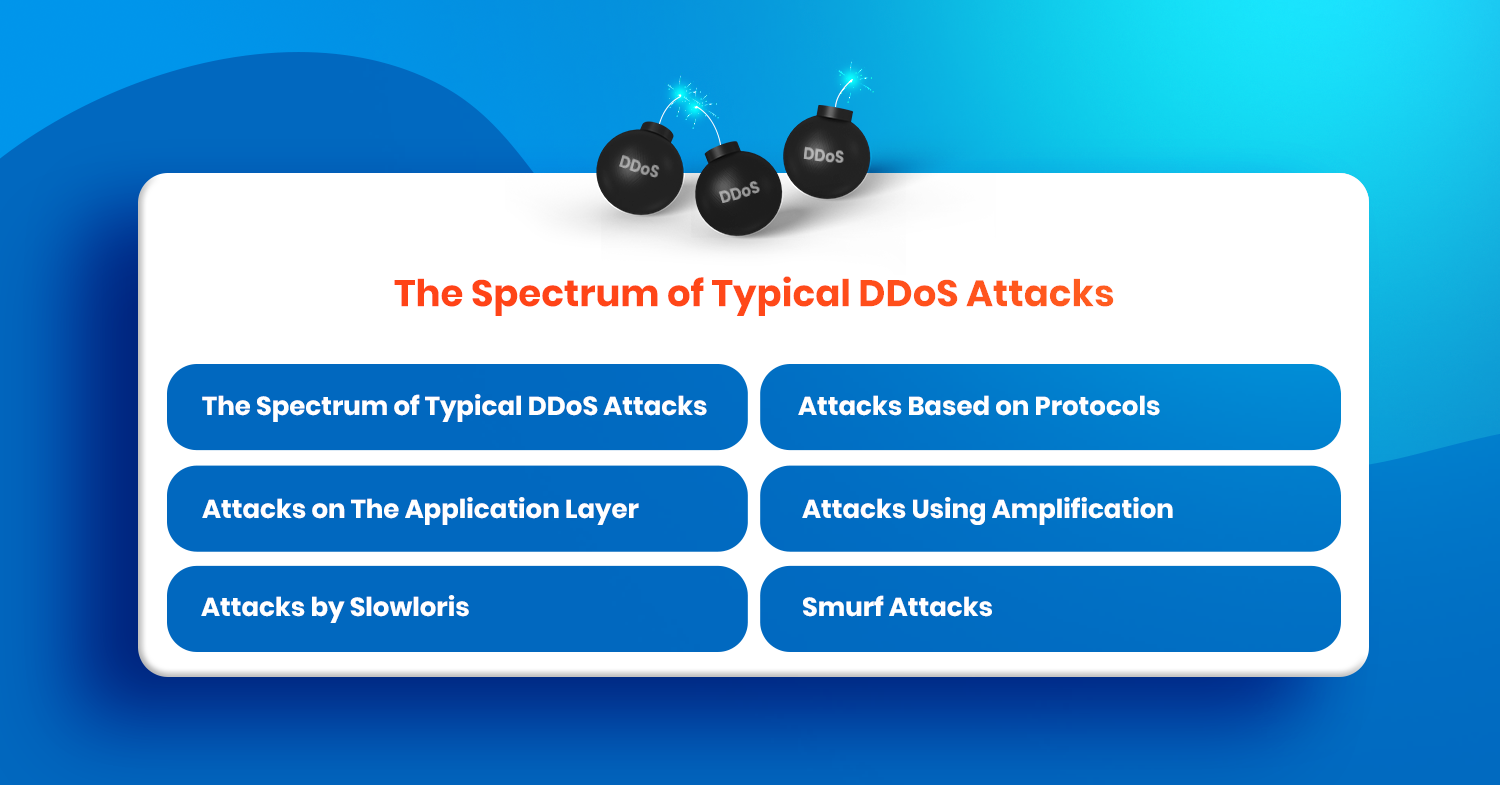
Attacks that combine two or more of the discussed attack categories are known as hybrid attacks. Their unique attack patterns, which mix multiple tactics, make them highly challenging to deal with.
In a nutshell, DDoS attacks are one of the most frequently applied techniques by cybercriminals to target present-day digital infrastructures and businesses. These attacks are getting tougher to stop and more sophisticated over time. Designing an effective cyber-defense against these threats necessitates a multi-layered strategy that combines application-layer, network-based, and cloud-based security measures. Organizations also need to devise reliable incident response plans in case of DDoS attacks. Having such plans in place can enable them to promptly respond to DDoS attacks, which is a must for lessening their impact.
How Can ESDS eNlight WAF help?
ESDS eNlight WAF is a specially engineered intelligent Cloud Hosted Web Application Firewall that allows you to filter incoming and outgoing web traffic and block threats like injection, cross site scripting and other attacks of the OWASP Top10.
It also allows the user to create custom rules for blocking web attacks. The illegitimate traffic gets automatically blocked by the eNlight WAF when anomaly threshold reaches and the custom response is sent to the attacker. With the Pay-As-You-Grow model, we ensure you’re billed solely for the resources you utilize.
Create your own defense rules and watch eNlight WAF defends the unwanted visitors with custom responses whenever anomalies strike!
