How Tier III DCs Deliver Sovereign Data Security You Can Trust

When it comes to hosting critical workloads, one question defines every decision for enterprises, PSUs, and government bodies: Where is the data stored, and under whose jurisdiction does it fall?
In an era where cross-border data flows can complicate compliance, the ability to retain control within national boundaries is no longer optional—it’s a fundamental part of Data Sovereignty india.
Nearly 9 in 10 execs now admit sovereignty risks are real, and most are acting now. (Source)
Our ESDS data center was purpose-built with this principle at its core. It doesn’t just house servers; it operates as a tightly controlled environment designed to meet data sovereignty requirements while providing the infrastructure depth required for government hosting infra.
In this in-depth walkthrough, we’ll step inside the layers of infrastructure, security, and compliance that make our Tier III facility a trusted choice for regulated workloads.
1. Controlled Entry—Security Starts Before the Server Room
Before a single packet of data flows in or out, the physical security protocols begin at the gate. Every individual entering the internal data center—whether staff, vendor, or visitor—is logged, verified, and authorized through multi-factor authentication.
- Visitor Management System (VMS): ID verification at reception, capturing entry and exit logs in real time.
- Access Badges: Role-specific permissions limit movement inside the facility.
- Biometric Verification: Fingerprint and iris scans at multiple checkpoints.
- Device Restrictions: Personal electronics are secured in lockers to prevent unauthorized data transfer.
This zero-trust approach ensures that only vetted personnel can access critical infrastructure, supporting the foundational principles of data sovereignty.
2. Redundant Power Architecture—Ensuring Uninterrupted Operations
In a Tier III facility, uptime is not a marketing term; it’s a deliverable backed by redundancy. The internal data center uses a dual-path power distribution model with N+1 redundancy, meaning every primary power source has a fully operational backup.
- Dual Utility Feeds: Power sourced from two independent utility providers.
- UPS Systems: Online double-conversion units for instant failover.
- Diesel Generators: Capable of extended runtime during grid outages.
- Automated Transfer Switches: Seamless switching without service interruption.
For government hosting infrastructure, where workloads often power essential citizen services, this redundancy is critical to ensuring that data and applications remain available at all times.
3. Precision Cooling—Environmental Stability at Scale
The reliability of compute infrastructure depends on maintaining the right environmental conditions. Our facility’s cooling systems are engineered for both efficiency and resilience.
- Precision Air Conditioning (PAC): Maintains consistent temperature and humidity across server aisles.
- Cold Aisle Containment: Prevents hot and cold air from mixing, optimizing cooling performance.
- Rack-Level Sensors: Monitors environmental variables to preempt potential issues.
- Redundant Cooling Paths: Failover-ready in case of component failure.
By maintaining stable environmental parameters, the internal data center extends hardware lifespan and ensures consistent performance for workloads governed by data sovereignty requirements.
4. Network Backbone—Resilient and Sovereign
A sovereign hosting model isn’t just about where the data is stored — it’s also about how it moves. The facility’s network infrastructure is designed for both resilience and jurisdictional control.
- Carrier-Neutral Access: Multiple ISPs for redundancy and performance flexibility.
- Dual Fiber Paths: Physical separation to prevent single points of failure.
- Dedicated Government Network Links: Supporting secure government hosting infra connections.
- Meet-Me Rooms (MMR): Isolated spaces for interconnections to maintain physical network security.
This network design ensures that sensitive data stays within sovereign control while meeting operational performance demands.
5. Security Operations Center (SOC)—Real-Time Oversight
Physical barriers are only one part of the equation. The internal data center integrates its physical security with continuous operational monitoring through an on-site SOC.
- 24/7 Staffing: Security personnel and engineers working in shifts.
- Video Surveillance: IP cameras covering every critical area, with long-term retention.
- Intrusion Detection: Alerts for unauthorized movement or tampering.
- Integrated Incident Response: Coordination between physical and cyber defense teams.
This ensures that compliance and operational integrity are maintained without gaps—a must for workloads requiring data sovereignty protection.
6. Compliance Alignment—Building to Regulatory Standards
Hosting sensitive workloads means meeting—and maintaining—specific compliance benchmarks. The internal data center holds:
- Tier III Certification: Independent validation of redundancy and uptime capabilities.
- ISO 27001: Information security management compliance.
- MeitY Empanelment: Qualification for government hosting infra contracts.
- Sector-Specific Adherence: Alignment with BFSI and PSU security frameworks.
These certifications aren’t static achievements; they’re sustained through routine audits, penetration tests, and control reviews.
7. Disaster Recovery Integration—Prepared for the Unexpected
Even the most resilient systems require contingency planning. The internal data center incorporates disaster recovery readiness as part of its core architecture:
- Geographically Dispersed DR Sites: For regulatory-compliant replication.
- Automated Failover Systems: Minimal downtime in the event of primary site disruption.
- Recovery Time (RTO) and Recovery Point (RPO) Compliance: Meeting contractual obligations for government hosting infra workloads.
- Test Drills: Periodic simulations to validate readiness.
For regulated workloads, these measures safeguard against data loss while maintaining sovereignty.
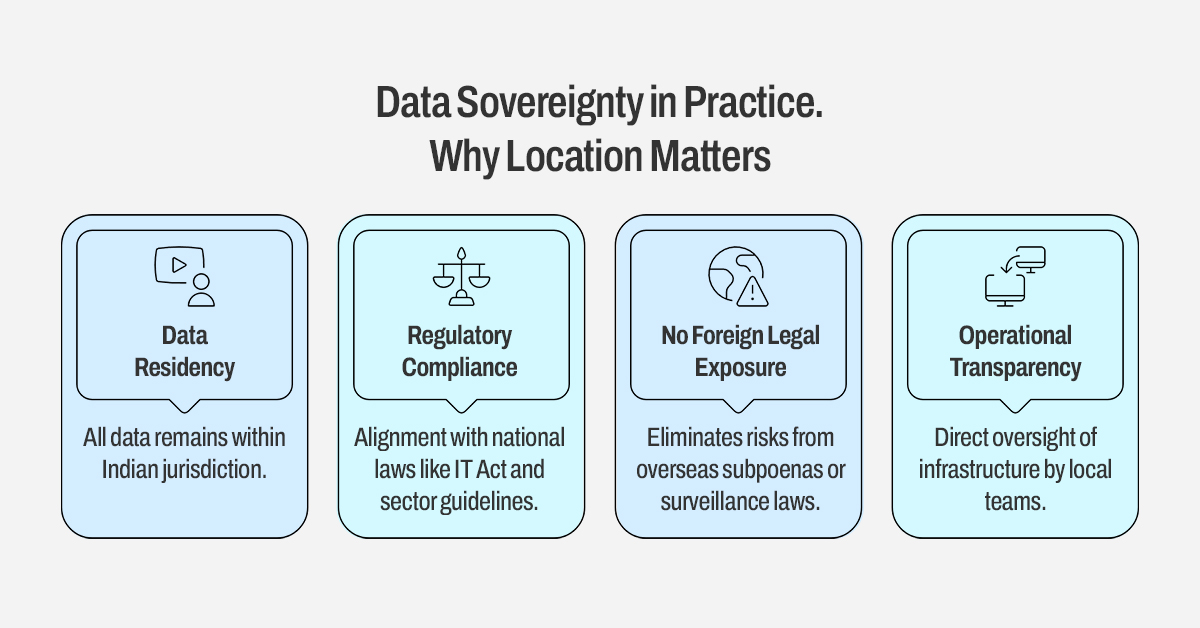
8. Data Sovereignty in Practice—Why Location Matters
Data sovereignty isn’t a theoretical concept—it directly impacts operational risk and compliance posture. Hosting data in a sovereign facility ensures:
- Data Residency: All data remains within Indian jurisdiction.
- Regulatory Compliance: Alignment with national laws like the IT Act and sector guidelines.
- No Foreign Legal Exposure: Eliminates risks from overseas subpoenas or surveillance laws.
- Operational Transparency: Direct oversight of infrastructure by local teams.
For government agencies and regulated industries, these controls are integral to both security and public trust.
9. Inside the NOC — Command and Control
The Network Operations Center functions as the heartbeat of the facility. From here, engineers monitor
- Server Health Metrics including CPU load, memory usage, and storage capacity.
- Network Latency and Bandwidth Utilization across multiple carriers.
- Environmental Data from rack sensors.
- Incident Alerts that trigger defined escalation protocols.
An onsite NOC enables rapid response without dependency on offshore support teams—reinforcing the operational principles of data sovereignty.
10. Automation and Operational Intelligence
Beyond the hardware, operational efficiency comes from smart management:
- AI-Assisted Monitoring: Detects anomalies before they escalate.
- Automated Patching: Ensures security baselines are consistently met.
- Centralized Logging: Audit-ready for compliance verification.
- Load Balancing Automation: Adjusts resources in real time for performance optimization.
These systems allow the internal data center to maintain operational discipline while meeting government hosting infra-SLAs.
11. Sustainability Measures—Responsible Operations
Regulated workloads are increasingly subject to environmental reporting requirements. The facility integrates:
- Energy-Efficient Cooling: Optimized airflow management.
- Renewable Energy Use: Where available within regional supply.
- PUE Monitoring: Tracking efficiency for continuous improvement.
- Waste Reduction Initiatives: Recycling of retired hardware components.
This aligns operational responsibility with broader ESG commitments for both government and enterprise clients.
12. Location Intelligence—Built with Purpose
Choosing a location for an internal data center goes beyond finding available land. Factors include:
- Security Perimeter Control—isolated yet accessible.
- Proximity to Government Hubs—supporting government hosting infrastructure requirements.
- Low-Risk Zone Classification—minimal exposure to seismic or flooding risks.
- Fiber Access Points—reducing latency for mission-critical workloads.
The result is an infrastructure site optimized for both physical security and operational efficiency.
Also read –
Data Sovereignty Matters: Secure Your Cloud Now
Why Data Sovereignty Is Important for Indian Enterprises
Conclusion
For CTOs and CXOs overseeing sensitive workloads, infrastructure decisions have long-term implications. ESDS Tier III data center delivers a blend of security, compliance, and operational stability that supports data sovereignty while meeting the stringent demands of government hosting infra.
From the secure entry checkpoints to the high-availability power grid and AI-driven monitoring systems, every component is designed with one objective: to give organizations full control over their data within India’s jurisdiction.
ESDS operates MeitY-empanelled, Tier III-certified internal data centers across India, providing secure hosting environments for enterprises, BFSI, and government agencies. With a focus on data sovereignty and robust government hosting infrastructure, ESDS combines infrastructure resilience with compliance expertise to help organizations operate with confidence under national jurisdiction.
- 7 Steps to Build a Strong Data Sovereignty Framework - November 3, 2025
- 7 Proven GPUaaS Steps for PSU Success and Secure Resilience - September 26, 2025
- How Tier III DCs Deliver Sovereign Data Security You Can Trust - September 5, 2025
