04
Apr
Cloud Orchestration Platform eNlight 360°
Management of a cloud infrastructure becomes a tiresome challenge for in-house IT staff when massive IaaS and PaaS deployments take place on the cloud. Using programming to manage the interconnectivity and communication between workloads on public cloud and private cloud infrastructure is known as Cloud Orchestration. Cloud Orchestration solutions are designed to create a cohesive workflow... Read More
29
Mar
Top 5 Tips for Disaster Recovery Planning
In this modern era of “always-on” business, prolonged downtime is not acceptable. It is the need of the generation to keep small or large businesses running all the time. A steady rise in data security attacks and continuously changing IT landscape have revolutionised the disaster recovery market in recent years. According to stats, 86% of... Read More
28
Mar
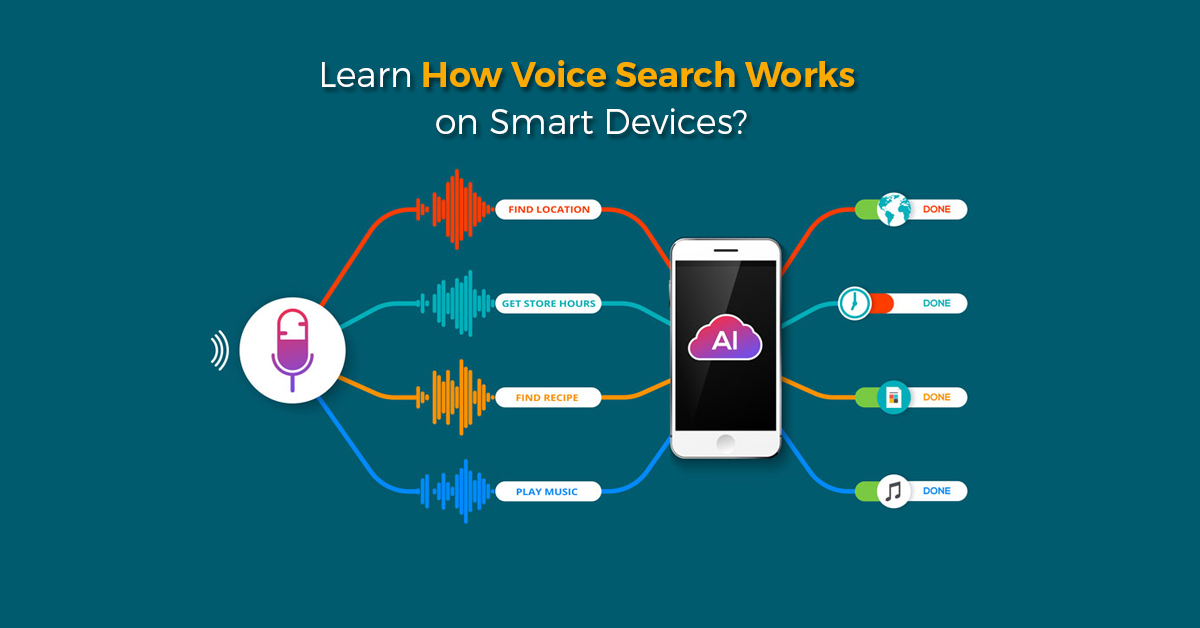
Your Voice Matters – How does Voice Search Work on Smart Devices?
Using voice search to interact with smart devices is what we are doing in our daily lives. Initially, it began with using voice search on phones, and later we got accustomed to smart watches, smart speakers, car speakers and much more. Several cloud platforms like Apple’s Siri, Google Assistant, Microsoft Cortana, and Amazon Alexa are... Read More
26
Mar
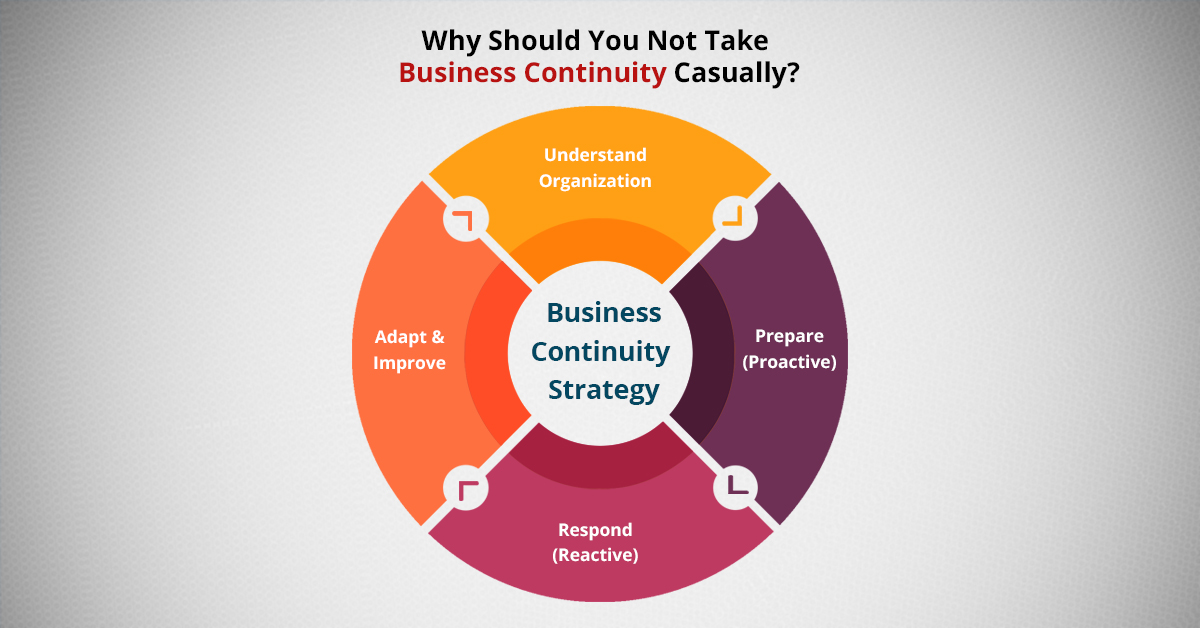
Why Should You Not Take Business Continuity Casually?
Let’s Start With Basics – What is Business Continuity? The term – ‘Business Continuity’ is quite expressive, meaning the ability to continue the business should have even after something disrupting or destroying has happened. The capability to recover and sustain vital operations during, and also after a disaster happens is the definition of business continuity... Read More
25
Mar
Signs of Cyber Attack and How to Respond to them?
Online business is the new trend in this era’s market. Having a website is just like owning a shop and getting a platform to showcase your business and fetch customers, increasing your sales and generate significant revenue. But every business faces some challenges, which if dealt in the right manner can make your way smooth... Read More
22
Mar
What are the key points you should consider before selecting a Colocation Provider?
In the IT world colocation services have turned out to be the most popular commodity. The IT world prefers colocation data centre facility as it allows for renting a space for storing and installing servers and other hardware. It provides the floor space, cooling, power and physical security to the servers, storage and/or applications owned... Read More
22
Mar
Why Data Centres prefer eNlight 360 as a flawless Cloud Management Software?
Modern data centers need constant protection from network data loss and cyber-attacks if not guarded properly. CTOs need to ensure proper monitoring in a data center to avoid any type of outage or downtime during critical processes. So the decision to have a tool in hand to monitor a data center is essential because it... Read More
20
Mar
The Menace of Clickjacking
Clickjacking We are easily enticed by free stuff and end up clicking on things we should not, because once you do that wham! You have just been clickjacked. You may think that you may have just won a lottery but soon all your personal information or even worse. A Clickjacking attack is designed to tricks... Read More
20
Mar
Data Replication or Data Back-Up – Recognize What You Need!
The usage of a back-up strategy by businesses is growing organically. Thinking about early days, manually copying the essential files to a detachable media was a hectic task to the system administrator. In earlier times, a stack of floppy disks would have been sufficient, but as time passed, the storage capacity increased, and the detachable... Read More
18
Mar
Why Should People Consider Colocation?
When your data is stored with Colocation Company, it becomes highly secured and monitored by their technical experts. This vendor offers 24/7 support, building security and infrastructure such as power, cooling, fire protection and redundancy. The most important fact of choosing a colocation provider is – making more effective use of capital and having a... Read More