28
Jan
Cloud storage – A simplified platform
Cloud computing server has been the most popular stuff now a days. It has become the choice of almost every mid-sized and small business entrepreneurs. Cloud storage is basically can be said as the model which consists of networked online storage. In this networked online storage the data is being stored on multiple virtual servers.... Read More
25
Jan
Difference Between Cloud Computing And Dedicated Hosting
Cloud computing is the major shift in the web hosting environment. Looking at the coming era its a strong belief that cloud computing is gonna take a huge place in the web hosting world. Cloud computing is a dynamically scalable and often virtualised form of hosting. Where as, if we speak about the dedicated server... Read More
24
Jan
What are the downsides of moving to cloud hosting?
Cloud hosting previously been used only by the governments and now a days it has made its way towards business both large and small. Every thing which comes has introduced in the market comes with some positive and some negative aspects. Image a multitude of servers that are connected through networks to create a cloud... Read More
23
Jan
Is Colocation cost-effective when compared to a cloud ?
Colocation and Cloud are two different aspects of web hosting services. There are several comparisons between both Colocation web hosting and Cloud web hosting. The basic point is which service is cost- effective while in comparison with each other. When putting this point that is colocation is cost-effective when compared to cloud? Then there were... Read More
22
Jan
Basics : Cloud Computing
Cloud Computing has become a buzzword now a days in the hosting industry. With the advancements in it companies like Google and Microsoft has extended their search/ investigations towards cloud computing. One of the hottest trends in small business and enterprise-sized IT is cloud computing. Cloud computing represents a major shift in the way companies... Read More
20
Jan
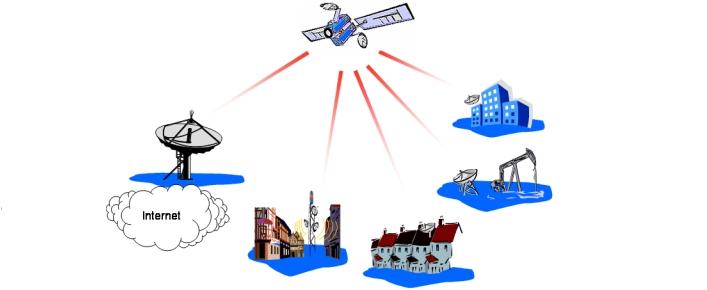
Setting up satellite Internet Connection
Now, a simple user can himself install home satellite internet without having to call a specialist entirely. Before installing a satellite Internet, you need to think whether you really need it or don’t need it. As with any type of communication, the internet via a satellite dish, there are advantages and disadvantages. Plus you can... Read More
18
Jan
Install Apache+PHP+MySQL
In the latest Linux distributions so-called RedHat based distributions installation ligament Apache+PHP+MySQL presents no special problems. But, as always, sometimes there are little pitfalls that often confuse novice admins, owners of dedicated servers, and programmers. We describe this process as an example with Fedora Core 4. We go to the server as root and type... Read More
18
Jan
Active Directory Issues on Dedicated Hosting
When you look at any technical aspect of the server it is considered that it may come up with an technical issues. Similarly, active directory issues on dedicated hosting is one of them. The technical aspect can face some or the other issues because it is automated not man made. Active Directory sites are a very... Read More
17
Jan
Why is WHO.IS Service Used?
WHO.IS service is used to determine the owners of domain names registered in the web and contains information about the company or the people under whose name these domains are registered, and sometimes on the system administrators who are responsible for the system. In addition, WHO.IS contains information about the owners of ranges of network... Read More
15
Jan
What and When Can We Expect From The Cloud?
The concept of cloud computing is Quite fashionable today and it is treated differently. It is the image of computing in which IT resources with a high degree of scalability are provided to users in the form of services through the Internet. A pool of managed computing infrastructure with a high degree of scalability is... Read More